An attacker sets up a man-in-the-middle phishing site and proxy server, then sends a phishing email.
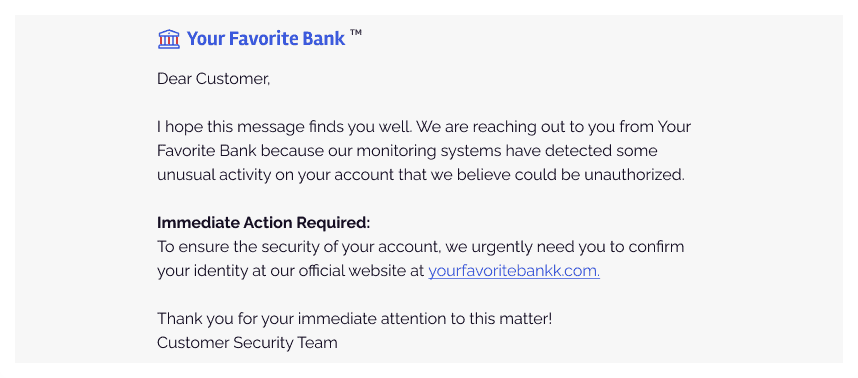
Does the end user detect the phishing attempt?
Yes

User ignores or reports the phishing email, and so the attack fails.
No

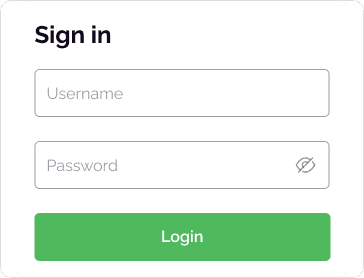
The victim clicks the link in the email, inputs their credentials into the phishing site.
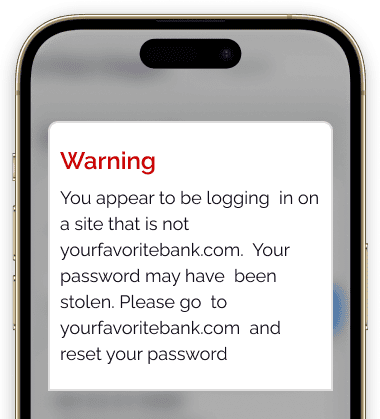
Does the bank use MITM phishing detection software?
Yes

Warning message alerts the user to the scam.
No

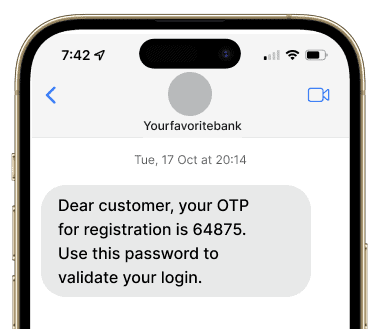
The reverse proxy server captures the user credentials, forwarding them to the legitimate bank site. The bank uses MFA and sends an OTP to the user.
The user heeds the warning, and the attack fails.

Consumer enters the OTP into the phishing site.
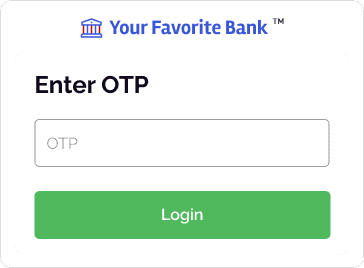
The reverse proxy server forwards the MFA token to the legitimate banksite. The attacker logs into the user’s account.

The attacker can now drain the account, apply for loans, harvest personal information, or carry out other heinous activities.

Malicious players are bypassing MFA. Your bank requires an additional layer of security. Man-in-the-middle detection systems like Arkose Phishing Protection detect, alert and block dangerous MITM phishing attack campaigns.
Learn MoreDownload the full infographic
Download PDF Version
