Executive Summary
In the world of financial services, a prominent neobank recently grappled with a pressing issue: the escalating threat posed by malicious bots. Recognized as a global pioneer in fintech, this bank found itself in the crosshairs of cybercriminals using bots to target user accounts. Driven by profit, fraudsters posed a major risk to the business, with a staggering 45% of sector traffic attributed to their activities.
Minimizing the need for frequent credential resets on compromised accounts allowed the neobank to not only fortify its defenses against bad bots, but also to demonstrate the advantages of proactive prevention.

The gravity of this issue is now at the forefront, highlighting the use of bots in manipulating financial transactions, contributing to market volatility, and raising alarm bells for investors. This industry brief utilizes data from our comprehensive bot abuse analysis, focusing on the top attack vectors in financial services during Q1, Q2, and Q3 2023. It seeks to provide data-driven insights into attacks on this industry, offering effective detection and prevention strategies.
Insights are drawn from the Arkose Labs Global Intelligence Network, which includes major corporations and category leaders. These entities, prime targets for cyber threats, provide a unique perspective for monitoring and analyzing cyber activities.
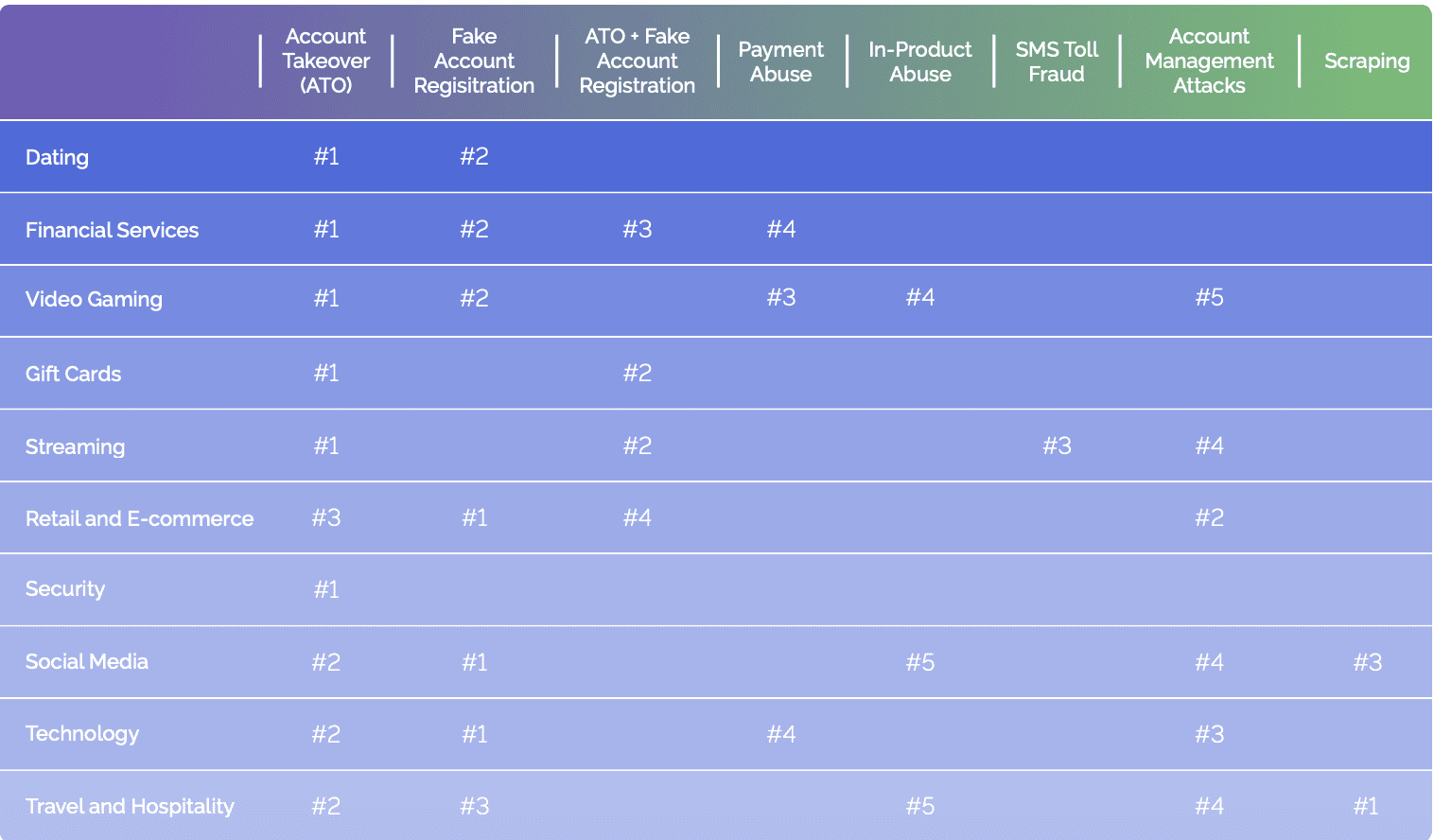
Attack type by industry in H1 2023:
We analyzed billions of sessions worldwide across industries, between January 2023 and September 2023, and assessed three primary attack vectors fraudsters use to launch various cyberattacks. In sum, these methods generated billions of attacks in the first half of 2023 and into Q3, comprising 73% of website and app traffic measured. That means almost ¾ of web traffic to digital properties is malicious.
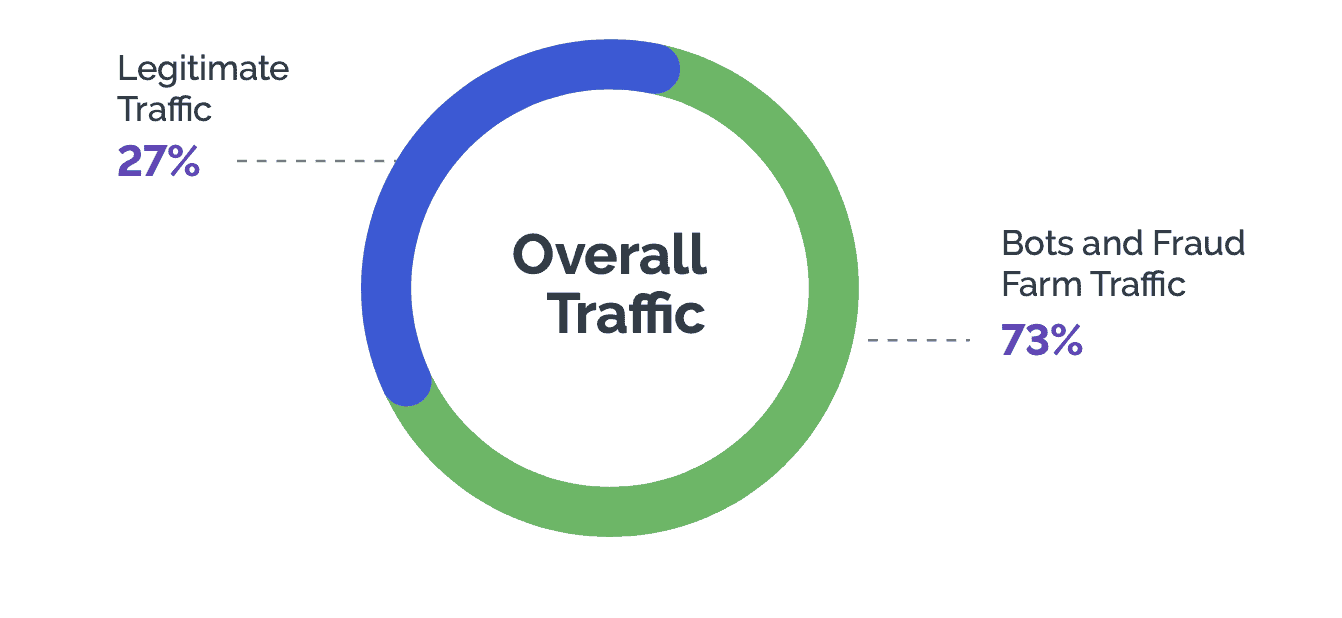
In the financial services sector, criminals dedicate substantial time and resources to activities such as phishing attacks, credential stuffing, and other fraudulent endeavors. But when faced with robust site protection, bad actors can no longer achieve the economic gains they seek and ultimately move on. This principle underlies the core principle of Arkose Labs—making attacks too costly for adversaries to persist.
The Bad Side of Bots
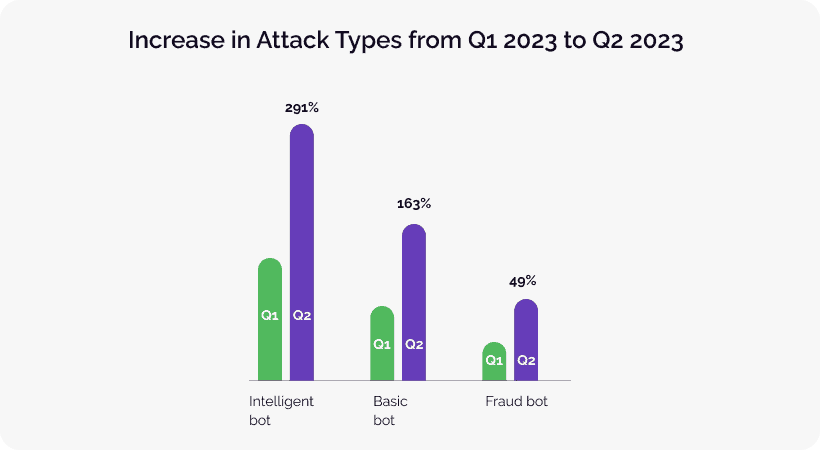
From Q1 2023 to Q2 2023, intelligent bot traffic nearly quadrupled—far outpacing basic bots and heavily contributing to a total increase of approximately 167% for all bot attacks. Specifically for financial services, almost half (45%) of online traffic comes from malicious bots.
Through the end of Q3, we analyzed billions of sessions worldwide for financial services, between January and September of 2023, and assessed three primary attack vectors fraudsters use to launch attacks, like web scraping, fake account creation, ATOs, and payment attacks.
While the prevalence of automated threats is a significant concern, there has also been a marked 26% uptick in human-based attacks during Q3. When malicious bots fail to make it past security defenses, threat actors often turn to human fraud farms to complete their mission.
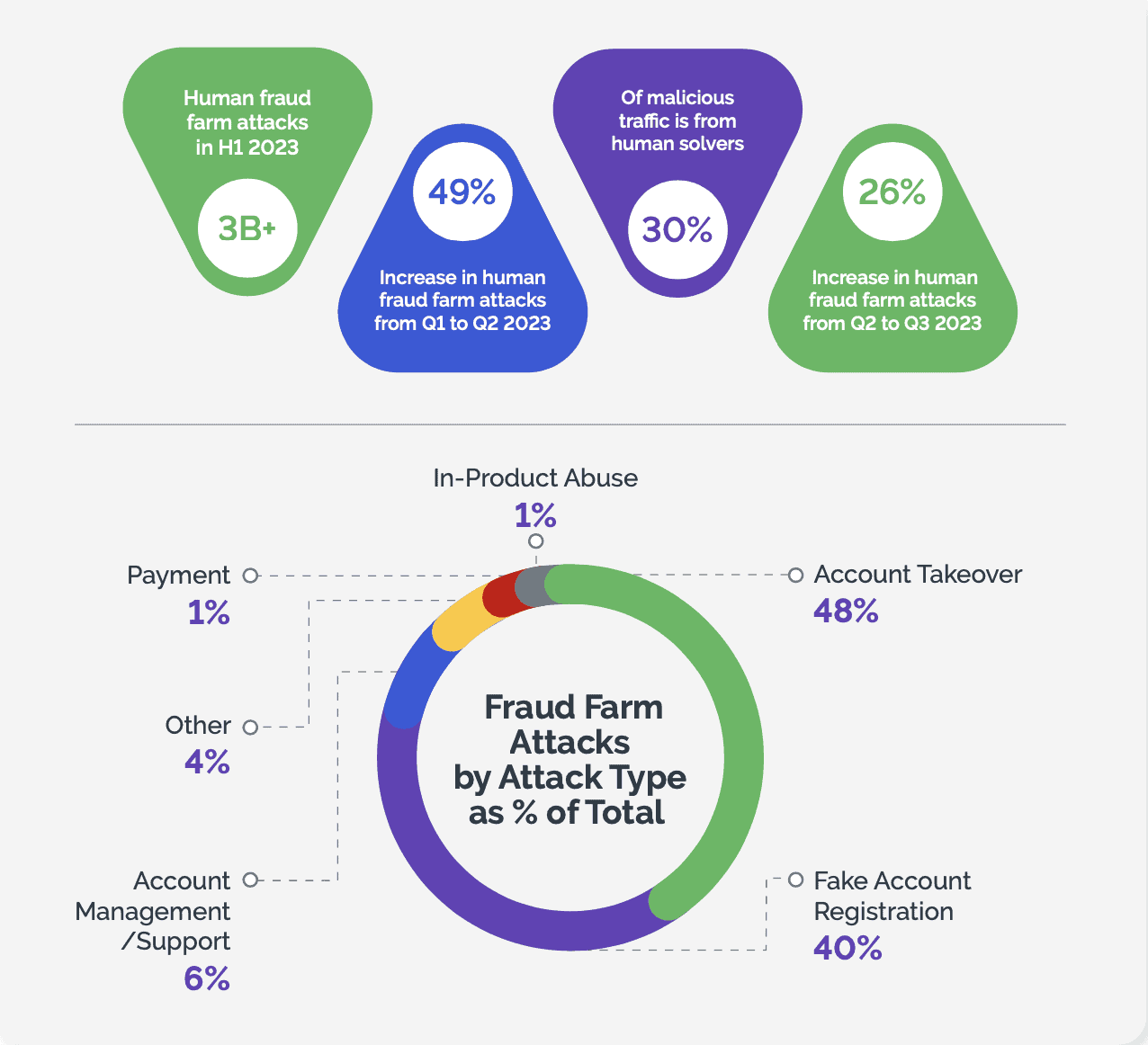
Notably, when the effort-to-attack ratio becomes prohibitively high, causing threat actors to spend excessive time and resources on endeavors like SMS toll fraud, they tend to shift their criminal focus away from financial services companies that are well protected.

Beating these adversaries demands technology that dynamically targets human solvers and applies adaptive, time-consuming challenges. With this capability in place, financial services organizations can defeat the economics behind attacks that exploit human labor at scale.
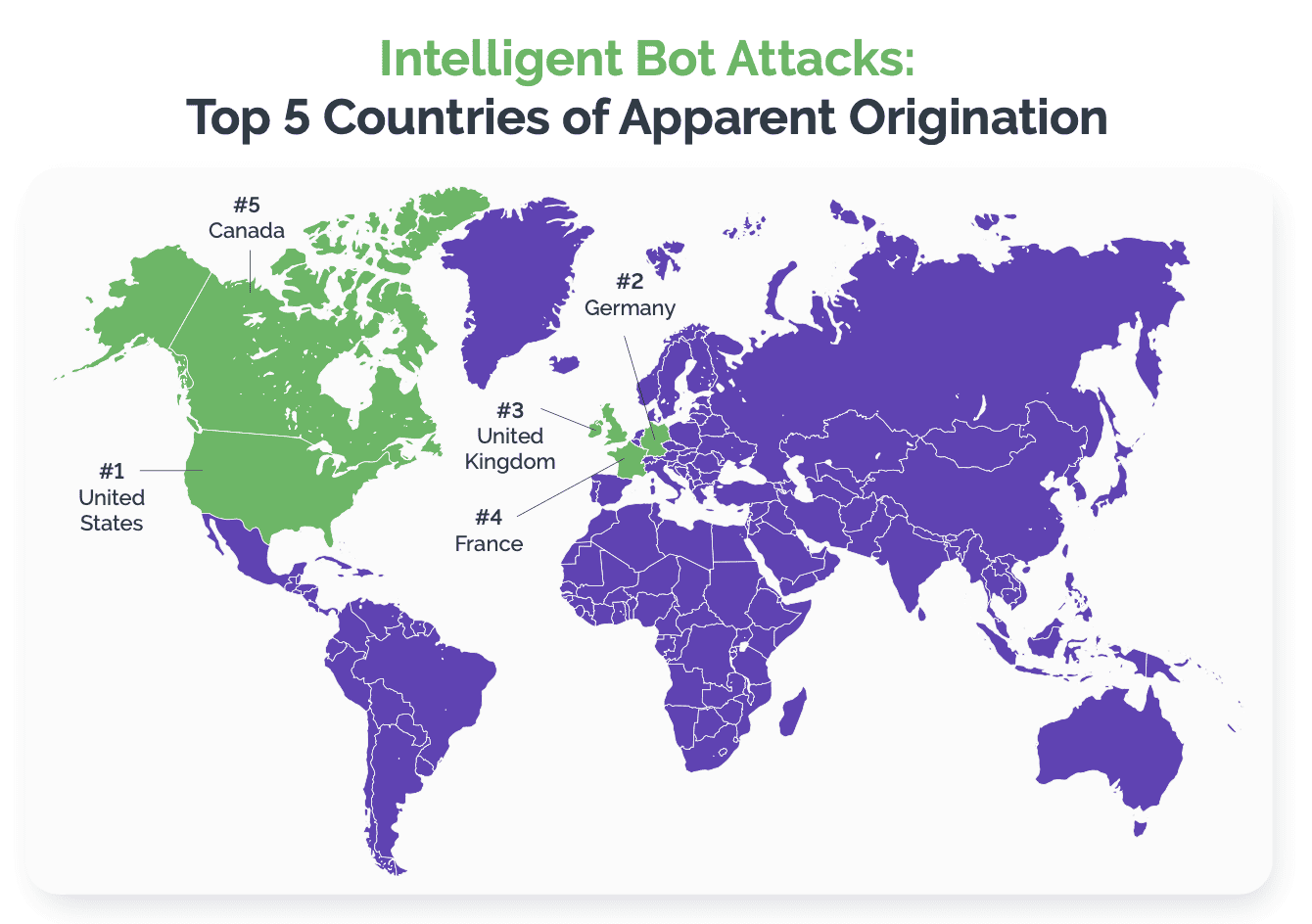
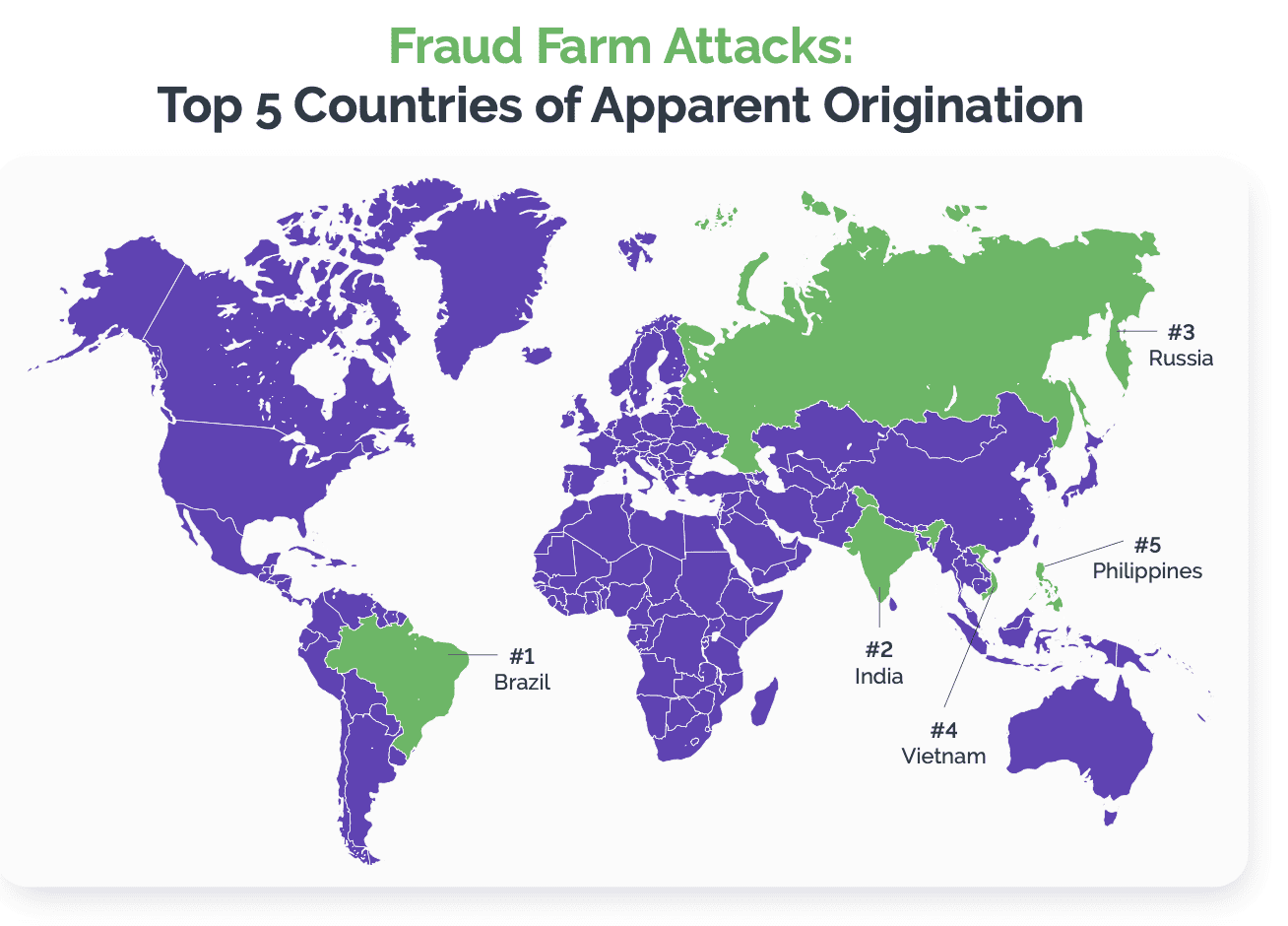
Concerning Trends and Crimes in Financial Services
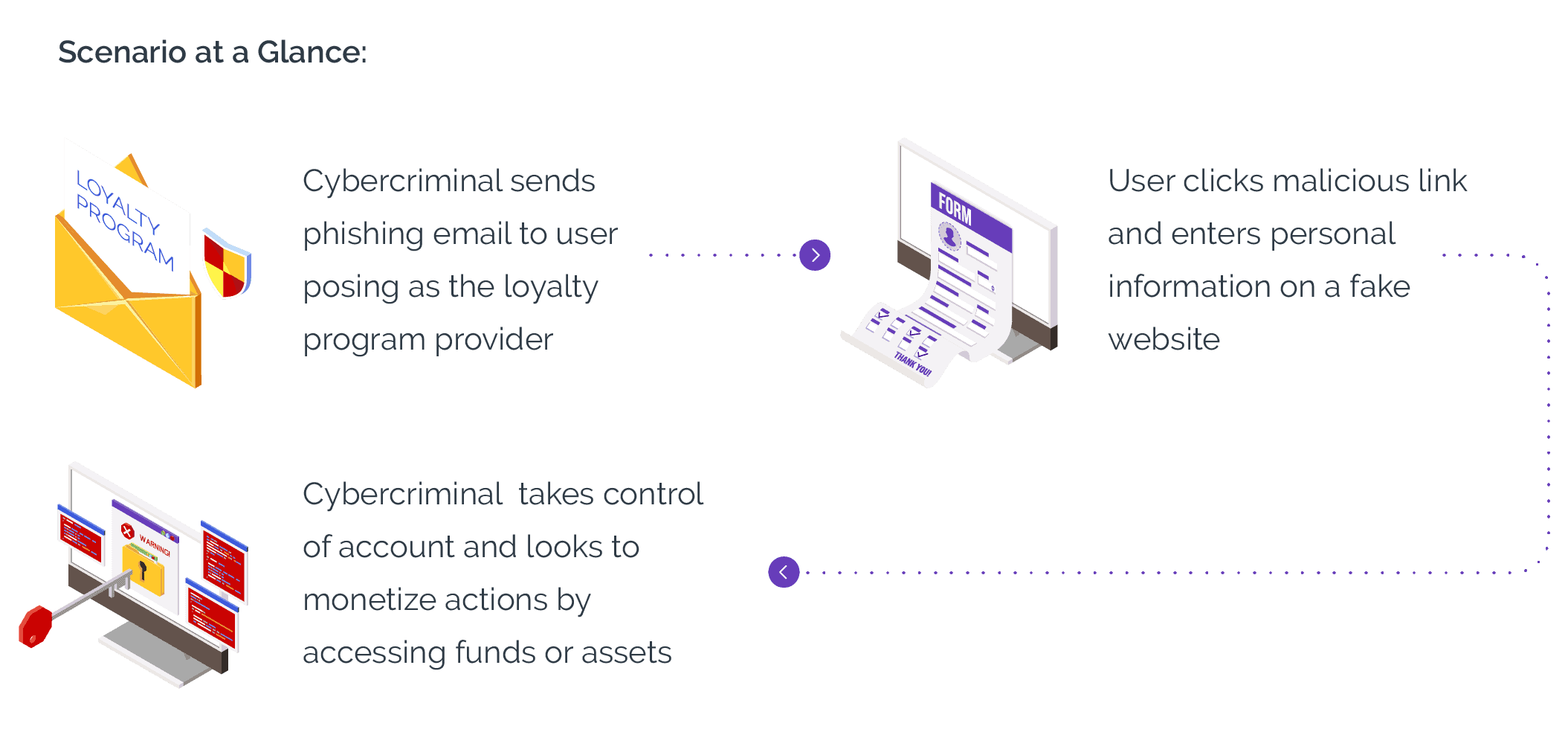
Cybercrime in financial services typically starts on a company’s website or mobile app where, in normal circumstances, a legitimate person registers (or signs up) for an online account or logs in to an online account they have already created.
Take the US banking sector as an example. It's estimated that 208 million online bank accounts exist today. To create those digital accounts, the consumer had to first register online with the bank. From a threat actor’s perspective, that represents 208 million vulnerability points that can only be reached through the effective use of bots.
In Q2 2023, there was a 202% increase in bots attempting to take over consumer financial accounts, and a 164% increase in bots attempting to establish fake new bank accounts. In fact, fake account creation became the primary attack type, outpacing ATOs and increasing more than 36,000% in Q3 over Q2.
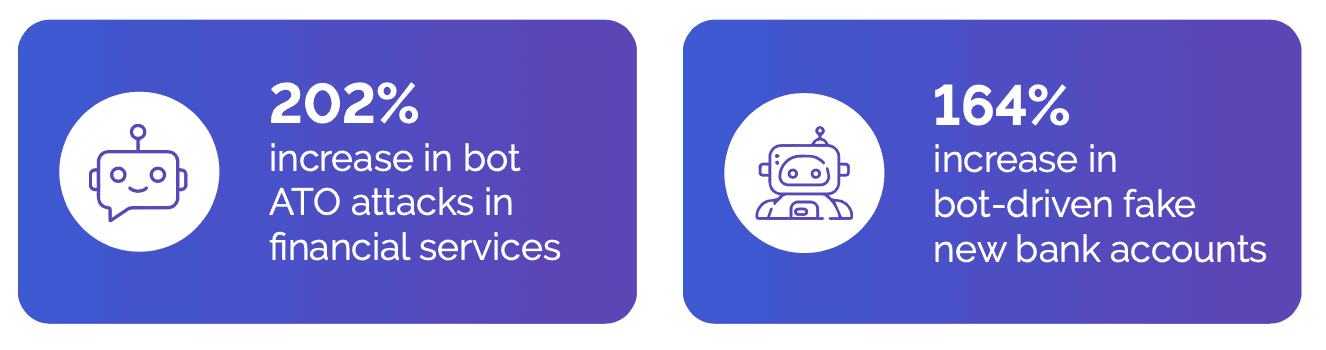
Bad actors were most likely trying to drain account balances through ATO attacks, while online fake accounts were likely the preferred methods to launder illicit proceeds gained from real-world crimes.
These account-based threats are often predicate offenses to larger crimes like money laundering and human trafficking, a heinous but highly lucrative crime reaching $150 billion in profit. Online accounts at banks, credit unions, and digital banks frequently serve as a layer in the money laundering process, facilitating the movement of funds.
Two Cyber Threats Driving Bot Attacks in Financial Services
Two technology trends, influenced by powerful economic forces, are driving the surge in bot and human fraud farm attacks:
1. Generative AI (GenAI):
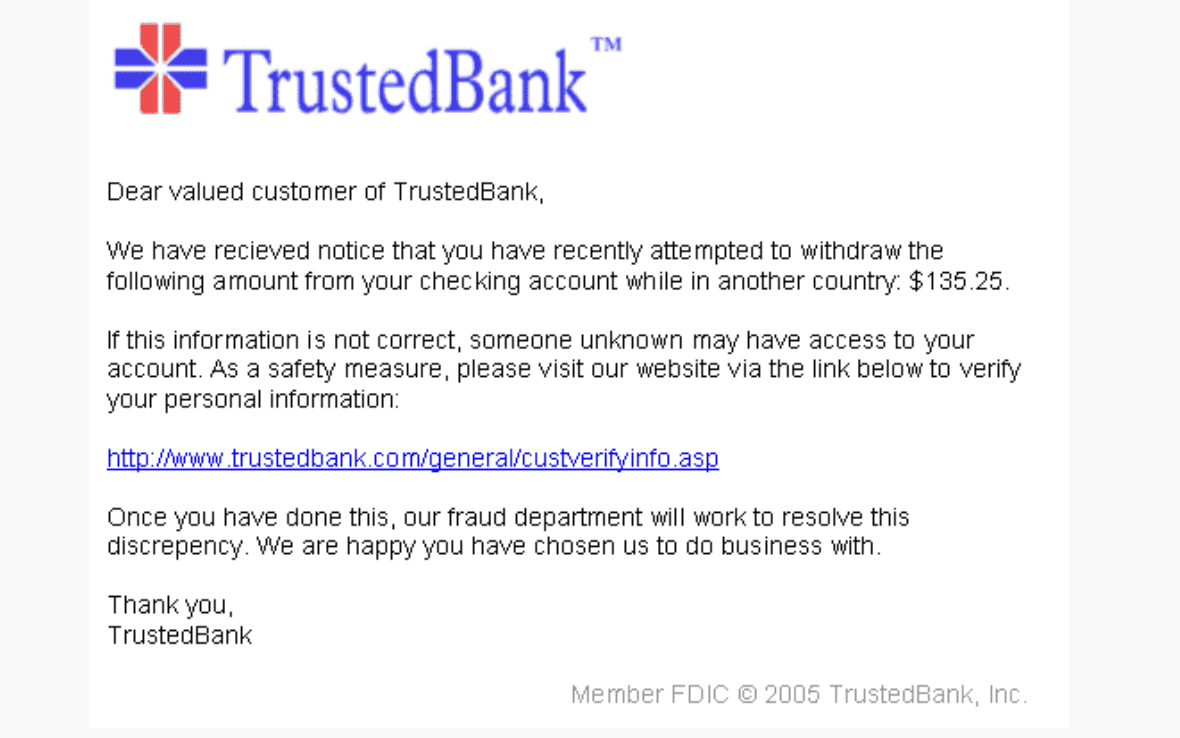
GenAI technology presents a multifaceted threat to financial services by facilitating attacks through various means. It empowers malicious actors to craft convincing phishing emails, tailor investment opportunities, or devise enticing loyalty programs, all aimed at deceiving consumers through personalized communication. These emails often include links leading to counterfeit login pages or malicious attachments, with the goal of compromising user accounts or financial systems.
Meticulously personalized using publicly available information, these deceptive emails convincingly mimic the communication style and branding of legitimate businesses. In fact, 46% of attacks on financial organizations involve some form of phishing.1 As unsuspecting consumers engage with these emails, they may inadvertently divulge sensitive information such as login credentials and personal details.
2. Cybercrime-as-a-Service (CaaS):
Bad actors are advancing their skills by embracing the CaaS model, deploying bots and unleashing attacks that cause trillions of dollars in damages. It involves the utilization of ready-made, purpose-built software kits for purchase by fraudsters, so they can orchestrate attacks on financial institutions. This shift lowers the barrier to entry and grants access to cybercrime for a broader range of actors.
Individuals possessing technical expertise are constructing these bots and distributing them to threat actors lacking such technical proficiency. Skilled attackers can now sustain themselves by building and selling bots to other fraudsters, even providing training on how to operate them, eliminating the need for direct involvement in criminal activities. CaaS is altering the entry requirements for newcomers to fraud as well as experienced technical attackers.
The CaaS model directly impacts financial services by establishing an online bazaar where cybercriminals can easily procure ready-made bots, tools, and expertise, like “customer service” and “training” modules. These digital marketplaces enhance the efficiency and reach of cyber threats, posing an immediate risk to the security of online transactions, consumer data, and overall operations.
The affordability and popularity of these marketplaces are pressing security teams to bolster their efforts against these rising threats. The widespread impact, economic incentives for cybercriminals, increased sophistication of attacks, and the potential monetization of stolen data contribute to the need for enhanced vigilance. As these marketplaces attract a broader range of threat actors and pose challenges in terms of reputation management and regulatory compliance, security teams must stay ahead of evolving attacks.

Industry Benchmarks
In the first half of 2023, nearly every industry experienced an increase in the number of attacks. Here are the top 5 sectors under attack, by volume:

The Growing Scourge of Attacks
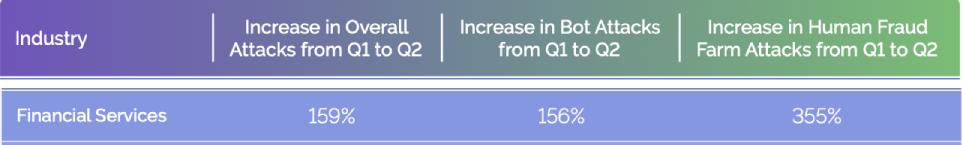
Attack Type Breakdown by Industry in H1 2023

Arkose Labs Can Help
Arkose Labs safeguards businesses by disrupting the financial incentives driving bot attacks. Our long-term bot mitigation and account security solutions focus on protecting critical user touch-points: account login and registration. By identifying hidden attack signals and undermining attackers' return on investment, we enhance security without compromising user experience.

Our unique platform, Arkose Bot Manager, analyzes user session data to assess context, behavior, and reputation, classifying traffic based on risk profiles. Suspicious traffic faces enforcement challenges, distinguishing b etween legitimate users and fraudsters to block automated activities and ensure a secure consumer experience.
Arkose Labs for Financial Services
Book a Meeting
Meet with a fraud and account security expert

