What is an adversary-in-the-middle (AITM) attack?
An adversary-in-the-middle (AITM) attack, also known as a man-in-the-middle (MITM) attack, is a type of cyberattack where cybercriminals intercept, relay or alter the communication between two parties without their knowledge, while giving the impression of a direct communication. This can lead to data theft, identity theft, financial theft or other exploitations.
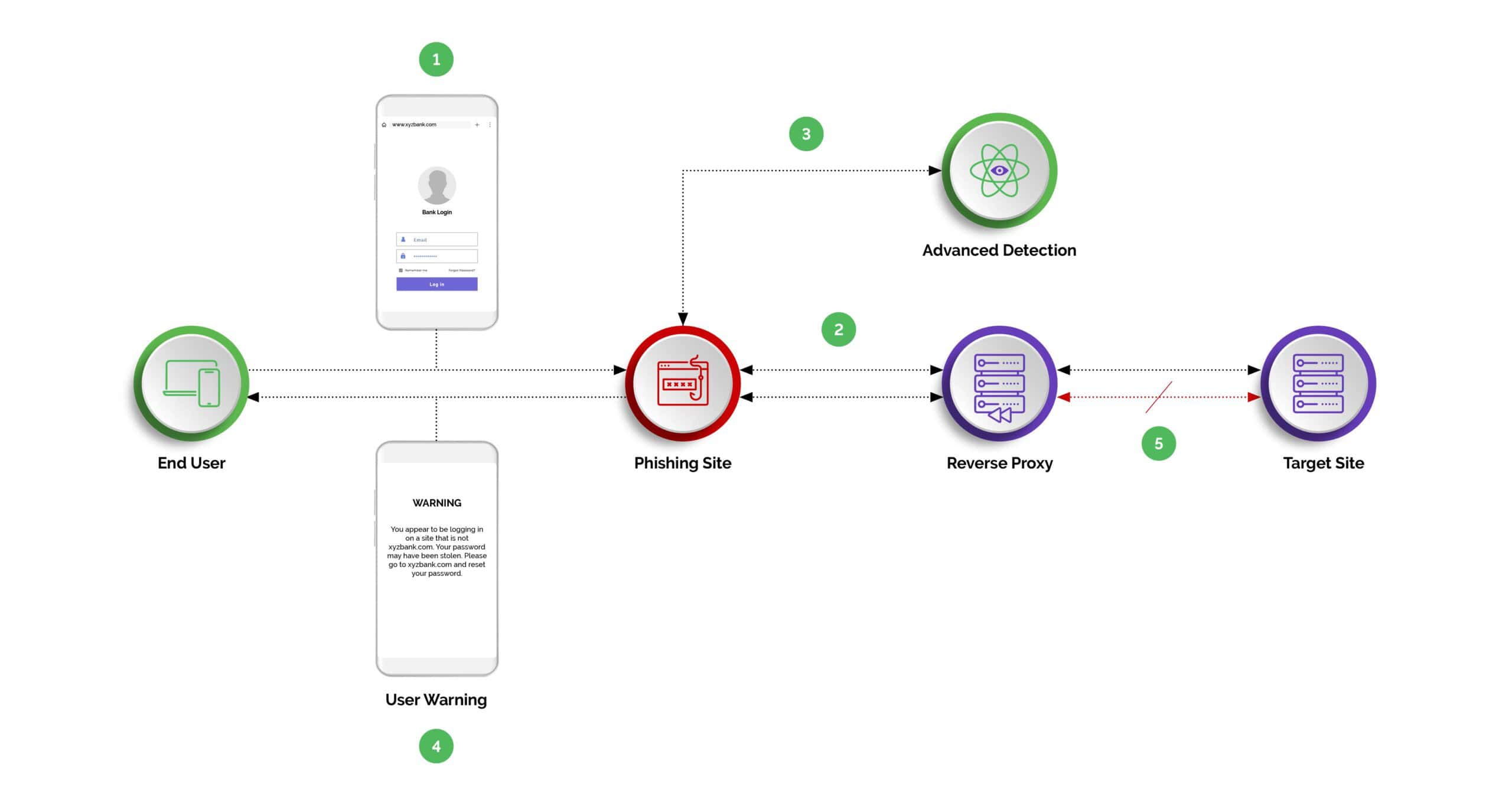
In one common scenario, attackers use advanced phishing sites (also known as reverse-proxy phishing sites) to lure victims into entering sensitive information, such as login credentials or multi-factor authentication (MFA) codes. These sites are designed to mimic legitimate websites almost perfectly, tricking users into believing they are interacting with the real site. As the user inputs their information, it is secretly transmitted to the attacker, who then can use it to access the victim’s accounts, initiate unauthorized transactions, or steal identities. Additionally, attackers might use this intercepted data to launch further attacks, deepening the breach's impact.
In other AITM attacks, bad actors use unsecured Wi-Fi networks, compromised routers, or malware installed on a victim's device to eavesdrop on sensitive information, like login credentials, financial details, or personal data, or to inject malicious content into the communication flow. They position themselves strategically between the sender and the intended recipient, to intercept and/or modify the data being exchanged. By manipulating the communication, attackers may deceive the parties involved into performing actions they wouldn't have otherwise, such as fraudulent transactions or money transfers.
What are the types of adversary-in-the-middle attacks?
Adversary-in-the-middle (AITM) attacks may take various forms, with each type of attack targeting different specific communication protocols or vulnerabilities within a system. Some common types of AITM attacks include:
- Session hijacking: Attackers take over an ongoing session between the victim and a server using a stolen session cookie or session token to impersonate the victim and gain unauthorized access to their account or sensitive information.
- Packet sniffing: Hacker intercepts and monitors the network traffic passing between two parties to capture packets of data, enabling them to read private messages, extract sensitive information such as user credentials, financial data, or personal information.
- ARP spoofing: In Address Resolution Protocol (ARP) spoofing, cybercriminals intercept and modify the traffic between the sender and the intended recipient by manipulating the ARP cache of a victim's device or router to associate the attacker's MAC address with the IP address of another legitimate device on the network.
- DNS spoofing: In Domain Name System (DNS) spoofing, attackers can redirect users to fake websites or intercept their communications, by redirecting DNS queries to a malicious server controlled by the attacker.
- SSL stripping: Bad actor downgrades a secure HTTPS connection to an unencrypted HTTP connection to intercept and read the supposedly encrypted data exchanged between the victim and the server.
- WiFi eavesdropping: Attackers intercept WiFi communications and capture sensitive information transmitted over the network, such as passwords, emails, or financial transactions, by exploiting vulnerabilities in wireless networks or by setting up rogue access points.
How AITM phishing attacks work
Adversary-in-the-middle phishing attacks operate by positioning the attacker between the victim and the legitimate entity being impersonated, such as a banking website or an online service. This allows the attacker to intercept, capture, and manipulate the communication in real-time. Here’s a closer look at how these attacks typically unfold:
- Setting Up a Phishing Site
The attacker sets up a malicious website that closely mimics a legitimate site that the victim trusts. This could be a bank, an email service, or any other online platform requiring login credentials. - Luring the Victim
The victim is lured to this phishing site through various means, such as a deceptive email, a text message, or even through compromised websites. These messages often create a sense of urgency, prompting the user to act immediately by clicking on a provided link. - Intercepting Communications
Once the victim attempts to log in or enter sensitive information on the phishing site, the attacker captures this data. However, unlike simple phishing schemes, in AITM attacks, the information is also relayed to the legitimate website in real-time. This means the attacker not only obtains the login credentials but also successfully logs in to the real site, bypassing two-factor authentication (2FA) or other security measures the user might have in place. - Session Hijacking
With the victim's credentials and active session information, the attacker can hijack the session. In some cases, they might manipulate the content of the communication, request additional information (like credit card numbers or social security numbers), or perform unauthorized transactions. - Covering Tracks
Throughout this process, the victim might remain unaware of the ongoing attack, as the attacker can relay content from the legitimate site back to the victim, creating the illusion of a secure connection. The attacker might also take steps to cover their tracks, making detection and response more challenging.
AITM attacks are particularly dangerous because they can circumvent traditional security measures like 2FA, SSL/TLS encryption, and others designed to secure the communication between a user and a website. To protect against AITM attacks, users are advised to verify the authenticity of URLs before entering sensitive information, use advanced security solutions like multi-factor authentication methods that are harder to intercept (such as app-based or hardware token 2FA), and stay educated about the latest phishing tactics.

Prime targets of adversary-in-the-middle attacks
Adversary-in-the-middle (AiTM) attacks target various industries, focusing on sectors that handle sensitive information and valuable transactions. Below are the prime targets that attract such attacks due to the potential risks involved:
- Financial Institutions: Stealing credentials to gain unauthorized access or perform fraudulent transactions.
- E-commerce Platforms: Compromising payment details and manipulating transactions for monetary gain.
- Government and Military Organizations: Targeting highly sensitive data.
- Critical Infrastructure: Disruptions can have severe impacts on operations.
What are the risks associated with adversary-in-the-middle attacks?
Adversary-in-the-middle (AiTM) attacks bring a range of serious risks for businesses and consumers. Here’s a breakdown of the potential consequences:
Data Breach: Interception of sensitive information like credentials, personal data, and financial details.
Identity Theft and Financial Losses: Stolen information can lead to unauthorized access and fraudulent activities.
Data Manipulation: Attackers may alter transactions or inject malware into communications.
Reputation Damage: Loss of trust, potential legal liabilities, and regulatory penalties can result from such breaches.
How can you identify signs of an adversary-in-the-middle attack?
Recognizing the indicators of a potential AITM attack can help organizations take timely actions. Here are some key warning signs:
- Unexplained spikes in network traffic: Sudden, unusual increases in traffic could signal malicious activity.
- SSL certificate warnings: Alerts about invalid or missing certificates during a secure connection.
- Unusual session durations: Longer-than-expected session times or sudden session terminations.
- Unauthorized account activity: Unexpected account lockouts or unexplained multi-factor authentication prompts.
- Communication with suspicious entities: Connections to known malicious domains or servers.
How to prevent adversary-in-the-middle attacks
Preventing adversary-in-the-middle (AITM) attacks requires multiple layers of defense to safeguard communication channels and sensitive data:
Phishing protection software: Use tools like Arkose Phishing Protection to monitor and block phishing attempts in real time.
Multi-factor authentication (MFA): Ensure the secure verification of user identities and prevent token interception.
Encryption: Implement robust encryption protocols like TLS/SSL for secure data transmission.
Regular updates and audits: Perform ongoing security checks and vulnerability assessments.
User education: Train employees to recognize phishing and security threats.
These measures enhance security and prevent unauthorized access through AITM attacks.
How Can We at Arkose Labs Help with Adversary-in-the-Middle Attacks?
At Arkose Labs, we provide advanced solutions designed to tackle adversary-in-the-middle (AITM) attacks. Our phishing protection tools actively block phishing attempts before attackers can compromise your accounts. We also secure multi-factor authentication (MFA) by preventing the interception of login credentials and authentication tokens. With real-time monitoring and alerts, we enhance your security, keeping your communications and sensitive data safe from unauthorized access.Request a demo.
