What is Zero Trust, and How Does It Work?
Cyber threats and data breaches are increasingly sophisticated and frequent. A zero trust model can help enterprises mitigate these threats while providing access to systems only on a need-to-know basis and only to users who are continuously verified. Here, we will explore the key principles behind a zero trust network, how it works, why it is so important, and the benefits it offers.
What is Zero Trust?
Zero trust is a security model that assumes no user or device, inside or outside a corporate network perimeter, is trustworthy by default. John Kindervag, a thought-leader and analyst at Forrester Research, coined the phrase "Zero Trust," which is based on the tenet "never trust, always verify." His revolutionary viewpoint was predicated on the idea that risk is a constant element both inside and outside the network.
A zero trust architecture is one based upon this principle. Access to a system or network is never granted based on location. A zero trust security model requires continuous authentication, verification, and authorization of all users, devices, and applications—every endpoint—trying to access the network. The emphasis on continuous monitoring and analytics helps detect any suspicious activities in real-time.
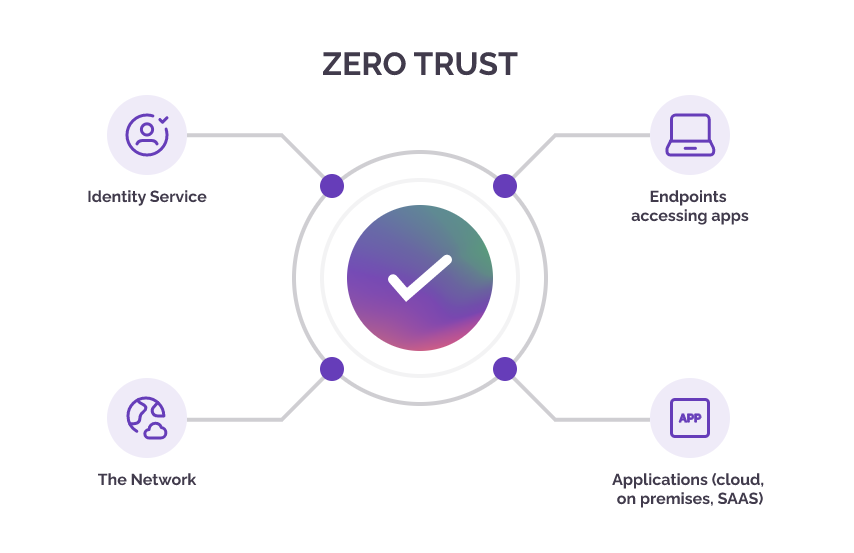
How Does Zero Trust Differ from Conventional Cybersecurity?
A zero trust approach differs significantly from conventional security policies. In a traditional cybersecurity model, everything inside the network is considered trustworthy, while zero trust assumes all users, devices, and networks are potentially compromised.
In a zero trust environment, there is no implicit trust. Access to resources is granted based on identity verification and contextual awareness, such as device health checks and user behavior, rather than network location. It requires continuous monitoring and authentication for all users and all devices, which provides a more robust and comprehensive security framework compared to conventional cybersecurity models.
ON DEMAND: Virtual Panel Series: Panel – Protecting User Accounts in a Zero-Trust World
What is Zero Trust Network Access (ZTNA)?
Zero trust network access (ZTNA) is an IT security solution based on the zero trust model described above. ZTNA offers remote access to an organization's applications, data, and services. In contrast to virtual private networks (VPNs), which allow access to an entire network, ZTNA allows access only to particular services or apps.
ZTNA relies on the prevention of lateral movement using microsegmentation, user verification, multi factor authentication, and least-privilege access.
What is the Prevention of Lateral Movement?
Frequently, after achieving initial network access, an attacker will attempt to move about the network, acquiring user access to more crucial information or systems. This motion is referred to as "lateral movement."
In other words, the point at which an attacker infiltrates a network is not usually the goal. For example, after breaching an endpoint, an attacker might traverse laterally through the networking environment, trying to locate a data center hosting the targeted content.
Preventing lateral movement refers to limiting access to resources within the network based on each user's role and permissions. This is a key aspect of zero trust network access because it helps contain a potential data breach and prevent attackers from moving laterally throughout the network.
In addition to limiting lateral movement, ZTNA emphasizes the importance of using multiple layers of security controls such as firewalls, encryption, and multi-factor authentication.
Microsegmentation
One of the main principles behind the zero trust security model is microsegmentation. This involves taking network segmentation a step further by breaking it into smaller segments in order to limit access to sensitive data and resources. Each segment is assigned unique permissions and access controls based on user identity and other contextual factors, which helps prevent lateral movement by attackers who have gained access to one part of the network. Microsegmentation can be implemented using software-defined networking (SDN) technologies, which provide a scalable and flexible way to create and manage segments within the network. By implementing microsegmentation, organizations can improve their overall security posture by reducing the attack surface and limiting the potential impact of a compromise.
User Verification
User verification is based on three pillars: identity, context, and security posture.
Identity
User identification, authentication, and authorization are all aspects of identity. In other words: Who are you? Are you who you say you are? Do you have permission to use that resource? Multi-factor authentication (MFA) should be used for identification.
Context
Context also refers to the user's method of attempting to access the resource. It is built on the principle of least privilege. Least-privilege access refers to the practice in which people are given access only at the lowest level necessary for them to perform their duties. In fact, users are not even able to see the applications to which they do not have access.
Security Posture
The device that someone uses to connect to a network determines their security posture. Every device must be secure according to the zero trust paradigm. This may be accomplished by verifying that the antivirus software, the operating system, or mobile device management (MDM) applications are all current.
Multi-Factor Authentication (MFA)
MFA requires users to provide multiple forms of identification, such as a password and biometric scan. This extra layer of security helps prevent unauthorized access to sensitive data and systems. MFA can be implemented through various methods, including hardware tokens, software tokens, and biometric authentication. The best way to set up MFA is in conjunction with a robust bot management solution—like Arkose Labs—that can be configured on the website's login and registration workflows prior to the MFA step. The login or registration can be completed only if the web server receives the token issued by Arkose Matchkey, the strongest CAPTCHA challenge response in the business.
Webinar: Beyond MFA: Building a User-Centric Authentication Strategy That Stops Attacks. Watch Now!

RECOMMENDED RESOURCE
Webinar: Beyond MFA: Building a User-Centric Authentication Strategy That Stops Attacks
Benefits of Zero Trust Architecture
The benefits of a zero trust architecture include secure access to critical applications and data and a simplified security infrastructure.
Secure Access to Applications and Data
By using granular access control for sensitive information, zero trust allows for visibility and auditing of all user activity, making it easier to detect and respond to potential security threats. The impact of a breach can be significantly diminished by restricting what users can access and how long they have access to it for. Bad actors are far less likely to find the data they're looking for if access is limited to a small dataset and is time-bound.
Greater Visibility
You can choose what to include in your security plan based on the importance and risk you assign to each asset or activity. Once you set up monitoring to cover all of your assets and activities, you will have improved threat intelligence with total visibility into all access requests, including the time, location, and apps associated with each request. An ideal security system tracks all activities and flags suspicious behavior.
Simplified Security Infrastructure
Because zero trust is built on a foundation of ongoing monitoring and analytics, access request evaluation may be automated. Access is automatically provided if the privileged access management (PAM) system determines that the request's key identifiers pose a minimal risk.
Automation streamlines access to only what users require without needing administrator consent. Only when an automatic system flags a request as suspicious does it require approval. This can significantly improve security posture while also reducing the workload on IT staff.
Continuous Compliance
By analyzing and logging each access request, a zero trust architecture supports continuous compliance by creating an audit trail that tracks the time, place, and associated application for each request. This improves the speed and effectiveness of governance, and the effort needed to comply with audits is reduced.
Conclusion
Zero Trust is a comprehensive security model that can help organizations protect their data, applications, and infrastructure from cyber threats. This model prioritizes “never trust, always verify” access policies to ensure that only authenticated and authorized users have access to sensitive data and resources.
However, attackers find new ways to exploit network vulnerabilities every day, so authentication is not a one-size-fits-all exercise. To keep up with the latest tactics of ATOs, fake accounts, and abuse, authentication requires a full funnel approach that starts at registration and login pages and works downstream like attackers do. A robust bot management solution should be a part of all security strategies, including zero trust networks.
Arkose Labs combines highly-transparent detection with targeted attack response to catch fraud early in the customer journey, without impacting good users. Our AI-powered platform combines defense-in-depth detection with dynamic attack response to navigate unclear trust signals without disrupting the good user experience. Enterprise security teams gain the advanced detection power, risk insights, and option for user-friendly enforcement they need to go from fraud mitigation to fraud deterrence.
Want to learn more? Book a demo today!
