What is web security?
Web security is a term used to collectively refer to the measures and technologies implemented to protect digital platforms such as websites, applications, and others from unauthorized access, data breaches, and other malicious activities.
It helps businesses ensure the confidentiality, integrity, and availability of web-based systems through a wide range of techniques and strategies. With a robust web security posture, businesses can identify growing digital threats and take appropriate actions to mitigate them and ensure website and application security.
Common web security risks for digital businesses
As more and more businesses take the digital route to serve their customers, they are getting exposed to numerous types of security risks. A greater influx of users also brings with it a deluge of bad actors, who try to exploit the loopholes in digital platforms to power several types of criminal activities.
This evolution in attack tactics, combined with easily available criminal toolkits, has resulted in security threats rising for today’s digital businesses and their consumers. Some of the common security risks that today’s digital businesses face, include:
- Account Takeover: Through account takeover attacks, bad actors try to gain unauthorized access to user and business accounts to steal sensitive information or disrupt functionalities of a digital platform, which can result in theft and exploitation of data for criminal activities.
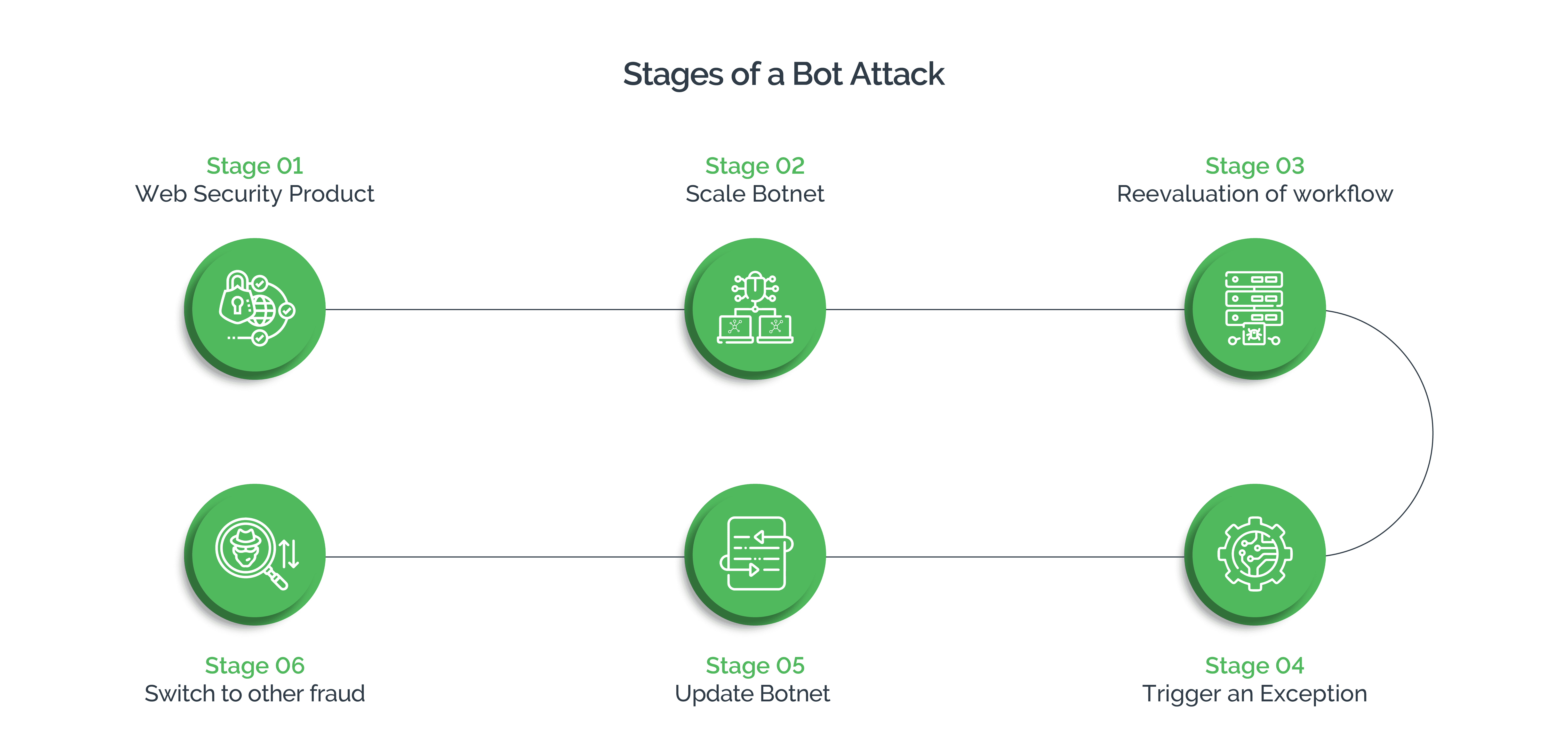
- Automated Bot Attacks: Using easily and cheaply available bots, attackers can automate several types of attacks and achieve scale as bots can execute commands in fraction of time that human attackers would need.
- Injection Attacks: Malicious code, such as SQL, OS, or script injections, are injected into input fields or parameters of a website, which allow attackers to exploit vulnerabilities, access sensitive data, and execute unauthorized commands.
- Cross-Site Scripting (XSS): Through XSS attacks, bad actors inject malicious scripts into web pages. When these scripts are executed, attackers are able to steal information, hijack user sessions, and execute a host of malicious activities.
- Cross-Site Request Forgery (CSRF): Through CSRF attacks, cyber criminals trick users into performing unintended actions on a website in which they are authenticated, for unauthorized requests.
- Malware and Viruses: Attackers may exploit websites and digital platforms to host or distribute malware, viruses, or other malicious software with an intent to infect users’ systems which can cause loss of data, system compromise, or illegitimate access to user information.
Web security is critical for digital businesses
Web security is critical to safeguarding business and consumer interests. Robust web security helps businesses protect sensitive consumer data and maintain user trust. It not only enables businesses to deliver seamless services, prevent fraudulent activities on their digital platforms, but also helps minimize financial losses, protect intellectual property and comply with regulations.
Modern digital businesses must prioritize web security measures as it is necessary to ensure smooth delivery of services. Web security is also necessary to protect sensitive data from unauthorized access and ensure users’ digital account security. Attacks and compromise of digital platforms can damage brand reputation, degrade user experience, and in worst cases lead to customer churn, resulting in loss of revenue.
Digital businesses may consider deploying web security measures, such as firewalls, intrusion detection systems, and proactive monitoring to prevent operational disruptions.
Important elements of web security
For comprehensive web security, businesses can use a combination of several tools, techniques, and technologies. All these elements work in conjunction to provide a layered defense and protect web applications and systems from various threats and vulnerabilities.
Businesses must also create and implement a comprehensive web security strategy that incorporates these elements for improved security. Some of the important elements of web security include:
- Encryption: Using encryption protocols such as HTTPS (HTTP over SSL/TLS) help secure the communication between the web server and the user's browser. They also help protect data in transit, preventing eavesdropping and tampering.
- Strong Authentication: Using strong user authentication mechanisms, such as unique and strong passwords, multi-factor authentication (MFA), and biometric authentication, among others can help to better identify and prevent suspicious activity. Further, using access control mechanisms, like role-based access control (RBAC), it is possible to limit user permissions to appropriate levels, which helps prevent unauthorized access to critical resources.
- Web Application Firewall (WAF): A WAF is a security solution that monitors web traffic to identify and block malicious requests, such as SQL injections, cross-site scripting (XSS) attacks, and other common vulnerabilities.
- Secure Coding Practices: Follow secure coding guidelines such as input validation, output encoding, and proper error handling to prevent injection attacks, buffer overflows, cross-site request forgery (CSRF), and other attacks.
- Intrusion Detection and Prevention Systems (IDS/IPS): Use these solutions that monitor network traffic and system activity to trigger alerts when risky behavior is identified.
- Working With a Reliable Vendor: Choose a vendor, such as Arkose Labs, that has demonstrated capabilities in protecting digital platforms and consumers without causing disruption to the business or user experience.
Best practices in web security
Web security is an ongoing process. It involves regular monitoring of security assets and continual review and evaluation of the effectiveness of the security measures in place.
For robust web security, businesses must combine technical measures with proactive monitoring to ensure protection of web-based systems and the data they handle. They can also follow the best practices to enhance their web security posture and reduce the risk of security incidents.
Some of the best practices that businesses can follow to enhance web security are as described below:
- Secure Coding Practices: Follow secure coding guidelines, such as sanitizing user inputs, using parameterized queries, employing secure authentication, and session management techniques, among others, to minimize the risk of introducing vulnerabilities.
- Encryption: Implement encryption protocols (such as HTTPS/TLS) to secure data transmission, thereby ensuring confidentiality and integrity of data.
- Patching and Regular Software Updates: To strengthen overall security, keep all software components, web servers, operating systems, and frameworks, up to date with the latest security patches.
- Access Control and Authentication: Use strong user authentication mechanisms, role-based access controls, and enforce least privilege principles to limit unauthorized access to sensitive resources.
- Strong Passwords: Enforce strong password policies. Require users to create strong passwords, follow security best practices, and avoid clicking on suspicious links, to protect themselves from social engineering attacks.
- Secure Configuration Management: Ensure proper configuration of web servers, databases, and other components to reduce security risks. Consider disabling unnecessary services, setting secure default configurations, and implementing least privilege principles.
- Secure Session Management: Implement secure session management techniques, such as session timeouts, secure cookie settings, to protect against session fixation attacks.
- Proper Error Handling: Use custom error pages and log errors securely for proper incident response and troubleshooting. Avoid displaying detailed error messages to users, as they can reveal sensitive information or assist attackers.
- Reporting: Implement security logging mechanisms to detect suspicious activities, and take timely corrective actions.
- Regular Backup and Disaster Recovery: Take regular backups of all sensitive web application data. Create an effective disaster recovery plan to mitigate the impact of security incidents, data loss, or system failures.
- Periodic Audits and Assessment: Use penetration testing and code reviews to regularly assess overall web security and identify vulnerabilities such as injection flaws, broken authentication, and so forth, in web applications, to allow timely remediation.
- User Education and Awareness: Educate users about web security best practices, such as using strong passwords, not opening unsolicited email attachments and links, and recognizing phishing attempts.
- Staying Informed: Keep abreast with latest web security trends, vulnerabilities, and best practices. Collaborate with other businesses to leverage threat intelligence and prepare for the evolving security threats.
Work with Arkose Labs for superior web security
Arkose Labs follows an innovative approach to enhance web security posture and help businesses protect themselves and their users from the ever-evolving cyberthreats. Arkose Labs routes the incoming traffic to its own network in order to deal with threats, while allowing the partner business to continue with business activities.
By triaging the traffic and accurately identifying risky users from good users, Arkose Labs helps improve good customer throughput. While good users can proceed with their digital journeys in a seamless manner, risky users, including human and non-human traffic, face targeted friction in the form of Arkose Matchkey challenges.
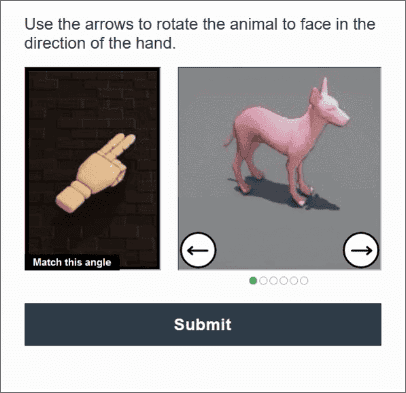
Automatic solvers, scripts and advanced bots are no match to these proprietary CAPTCHA challenges, which sap time and resources to delay completion of the attacks. These delays increase the costs of the attacks and erode the returns, forcing attackers to abandon the attack and move on, thus ensuring long-term security from evolving attack tactics.
Arkose Labs also provides round-the-clock support to its partners and shares valuable insights, raw signals, and attributes, helping clients’ security teams to adapt to evolving attack tactics and ensure comprehensive web security of their digital platforms.
