Whaling attacks, also known as whaling phishing, are a type of spear-phishing attack that specifically targets high-level executives within a company. In these attacks, there is also a social engineering component. Attackers invest more time and effort than they would in a large-scale phishing attack to gather personal details, such as job titles, and information from LinkedIn, Facebook, or Twitter profiles, to make their emails look as legitimate as possible.
Whaling attacks are called so because they are like "whaling"—instead of casting a wide net to catch as many victims (fish) as possible, the attacker hunts a single, lucrative target, like a top executive (a whale). Overall, whaling attacks are a serious threat to businesses that need to keep sensitive information safe, and employees at all levels of a business should take them seriously. According to the FBI’s Internet Crime Complaint Center (IC3), phishing was the number one tactic used by cybercriminals1.
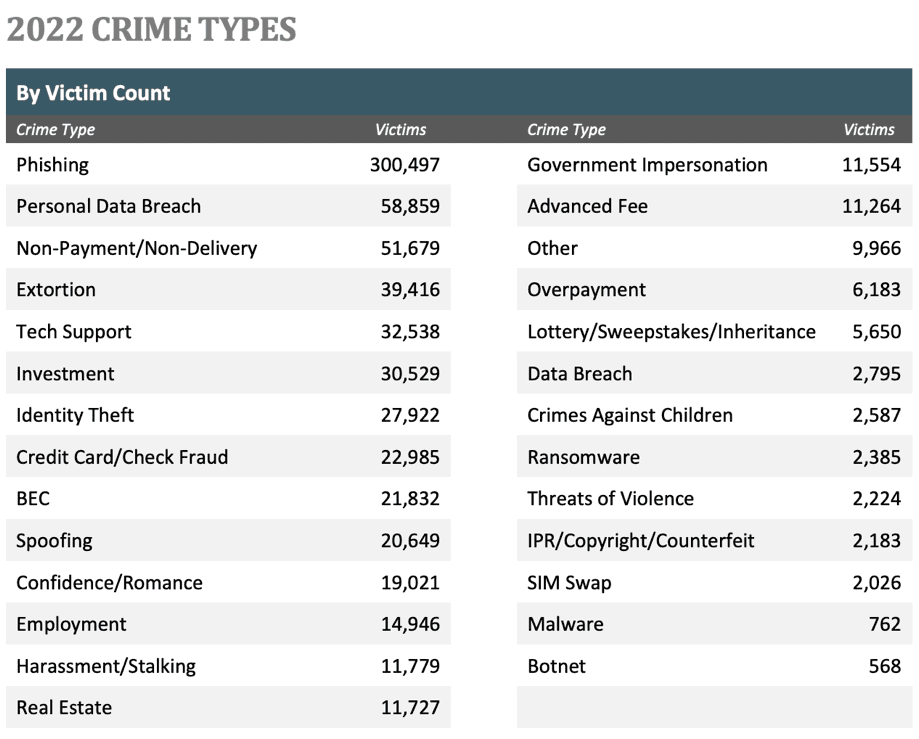
How Whaling Attacks Work
Whaling is a type of spear-phishing attack that tries to get sensitive personal or business information from well-known people, often high-ranking employees or executives in a company. Attackers often spend a lot of time and money gathering personal information about their targets so they can send an email that looks real and makes it more likely that the target will fall for their trick. Often, business email compromise techniques are used in these types of attacks to get to confidential information and compromise accounts. Due to the extensive effort involved in a whaling attack, they are typically more difficult to execute successfully compared to traditional phishing attacks, which is why it's important for organizations to take proactive measures to protect against potential attacks.
Whaling vs. Phishing vs. Spear-Phishing
People often confuse phishing attacks, whaling phishing attacks, and spear-phishing attacks. All of these are types of phishing scams that try to get sensitive information from users or trick them into taking quick action that turns out to be harmful. The differences lie in the specificity of the target.
Phishing is a broad term for any type of attack that tries to trick victims into doing something, like clicking a link, giving away sensitive information like usernames, passwords, and financial records for bad reasons, installing malware, or making a fraudulent financial payment or wire transfer. Normal phishing email attacks usually involve sending emails to a large number of people without knowing how many of them will be successful.
Spear phishing attacks use fake emails to try to get sensitive information from a specific person or organization without their permission.
Whaling email attacks, on the other hand, normally target just one person at a time, usually a high-ranking person who has access to very specific information.
Spear phishing can be used to attack any specific person, while whaling is a type of spear-phishing that specifically targets a specific high-level employee. Both types of attacks usually take the attacker more time and work than regular phishing attacks.
What are the Consequences of a Whaling Attack?
A whaling phishing attack is a type of social engineering attack designed to deceive individuals by masquerading as trusted names or groups, and these attacks can have severe consequences for organizations, such as CEO fraud, data loss, revenue loss, and reputational damage.
The primary goal of a whaling attack is to gain access to money or sensitive data, such as employee payroll information or income tax data. Once the attacker succeeds, the organization may experience significant financial losses.
Financial loss
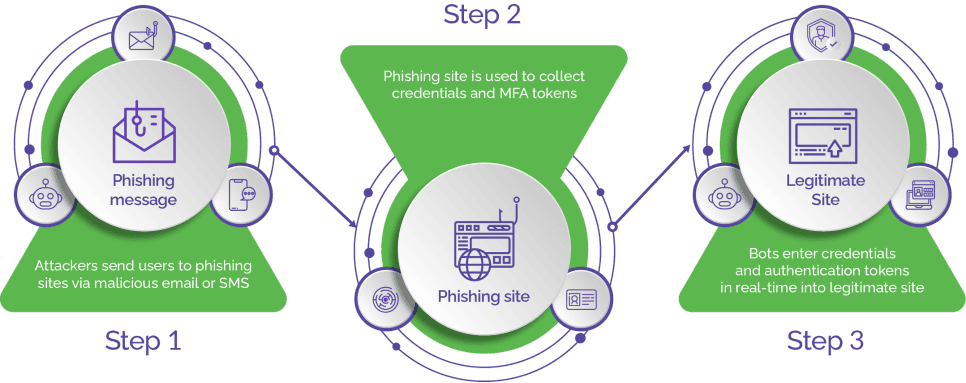
Attackers often masquerade as a known entity (such as a vendor or partner), spoof an email address or website (see image below), and present a false sense of urgency—perhaps mentioning an unpaid invoice that needs to be paid right away. The malicious sender then asks for wire transfers, money, or private information. If the high-level target is a busy CEO or CFO who just wants to resolve the issue, they may comply with wire transfer instructions without giving it more thought. In some cases, whaling attacks result in the transfer of significant sums of money from the target company to the scammer's account. The cost of remedying a whaling attack can be high and may require a security team to take extensive measures to prevent future data breaches.
Reputational damage
Whaling attacks are particularly dangerous because they target senior individuals within an organization. By using fraudulent communications to appear as if they are from someone influential, attackers can gain access to sensitive information.
When employee or customer data is compromised through a whaling attack, it can lead to negative press and a loss of customer trust. This can also result in the loss of reputation-led relationships such as brand deals and sponsorships. A whaling attack is embarrassing for both the executive who is attacked and the organization as a whole.
How to Avoid a Whaling Attack
Organizations can protect sensitive data and avoid financial losses by teaching all employees how to recognize and avoid whaling attacks. This can be done through security awareness training and data protection procedures that teach executives how to limit online personal information. All employees should pay special attention to emails from outside the company and make sure they are really from a trusted source. This is especially important for emails that ask for credentials or come with an attachment or link.
Companies can stage fake whaling attacks and teach employees how to spot and report email spoofing and whale phishing attempts. identifying and preventing malicious emails from reaching users.Email filters and other anti-phishing tools can also help users find and stop malicious emails from getting to them. Furthermore, organizations should use technologies such as two-factor authentication and encryption as part of an overall cybersecurity plan. They also should install and update antivirus and anti-malware software to reduce the chances of the installation of ransomware. These measures can play a critical role in increasing the detection of, and reducing the likelihood of, a whaling attack.
Prevent Whaling Attacks with Arkose Labs
All phishing methods, including whaling attacks, have evolved in recent years with the introduction of sophisticated platforms that are built to easily evade detection. The new breed of phishing methods, like Adversary-in-the-Middle (AITM) reverse proxy, and cybercrime-as-a-service platforms like EvilProxy and Caffeine Proxy, make it difficult to detect and mitigate attacks. Phishing continues to evolve, and needs a comprehensive security posture to defend against the malicious attacks. While traditional detection and mitigation methods provide a certain amount of security, they are often unable to provide comprehensive security within a reasonable cost and complexity. In this case, a robust bot management platform, like Arkose Labs, is the answer.
Arkose Labs provides a multilayered defense against advanced, persistent attacks on user accounts. It is backed by a commercial guarantee on the efficacy of the solution, with a promise to defeat the automated login attacks that advanced phishing relies on.
Conclusion
Whaling attacks are a sophisticated type of phishing attack that target high-level executives and individuals within an organization. Falling prey to a whaling attack can be catastrophic, from financial losses to irreversible damage to a company's reputation. It is crucial to implement multistep verification, educate employees on social media usage, adopt strict data protection policies, and invest in anti-phishing tools. If you would like to learn more about how Arkose Labs can help secure your enterprise from advanced threats like whaling phishing attacks, book a meeting with us today.
