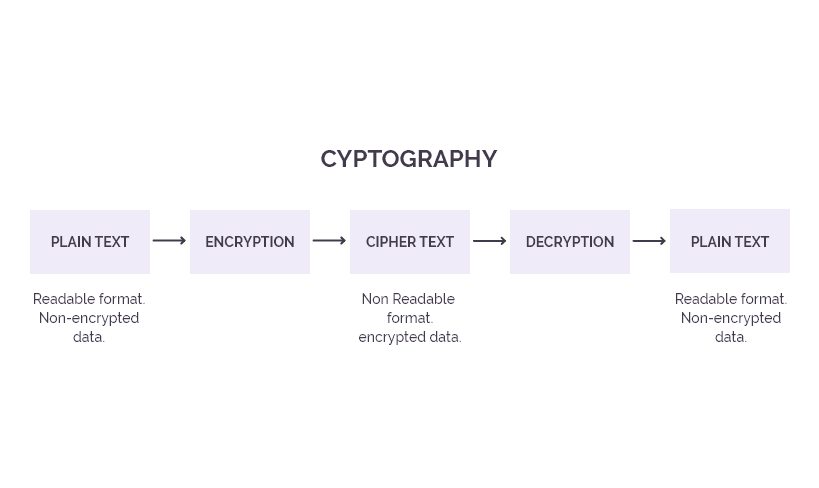
What is online payment fraud?
Online payment fraud is where a bad actor uses a consumer’s stolen payment information for unauthorized digital transactions and payments. Online payment fraud causes losses both to consumers and businesses, including chargeback fees, penalties and costs of remediation to the business.
These do not even include loss of valuable time and effort that merchants have to spend settling the disputes. The consumer faces emotional trauma trying to block compromised cards and getting the losses reversed. Another example of online payment fraud is where consumers themselves initiate a false claim.
Factors leading to a rise in online payment fraud
Online payment fraud is a growing challenge for merchants and businesses as it continues to rise unabated. Online payment fraud is on the rise due to several factors, including vulnerabilities in systems, processes, or human behavior.
One of the main reasons for the rise in online payment fraud is retail purchases becoming digital. Consumers can hail a taxi, order food, socialize and look for romance through a range of apps. They also have multiple digital payment options including card not present, payment apps, digital wallets, peer-to-peer payment platforms, and internet banking among others. While technological advancements have made payments more convenient, they have also introduced new avenues for fraud. A fraudster attempts to exploit weaknesses in online payment systems, mobile payments, and other digital platforms, especially targeting card-not-present (CNP) transactions and Buy Now Pay Later (BNPL) or Point of Sale (PoS) lending, which allows consumers to break the payments into equal installments.
Financial services are increasingly becoming digital with consumers demanding on-the-go banking services. With an increase in globalization and cross-border transactions, there are greater complexities and vulnerabilities in payment systems, which can be exploited by fraudsters operating across different jurisdictions. Furthermore, in-person verification is declining as account onboarding formalities are going digital. While this has made access to banking and financial services easier, it has also opened up a large area for attack. For instance, during the COVID-19 pandemic, attackers stole government-sponsored stimulus checks and unemployment benefits. They also duped many citizens into donating online for fake charities.
The growth of new payment technologies, such as cryptocurrencies or peer-to-peer payment systems, has introduced new risks and uncertainties, as these systems may not have the same level of security or regulation as traditional payment methods.
To make matters worse, weak authentication methods, such as reusing passwords across multiple digital accounts, using easy-to-guess passwords, or lack of multi-factor authentication, make it easier for fraudsters to gain unauthorized access to accounts and conduct fraudulent transactions.
Vastly different compliance requirements make it challenging to enforce consistent security standards. Combined with weak regulatory oversight, inadequate compliance measures create loopholes that fraudsters can exploit, contributing to the growth of online payment fraud.
Common Methods of Online Payment Fraud
Bad actors are in the business of making money. They use the path of least resistance to maximize their exploits. Therefore, they choose the attack method depending on the target and potential returns. Some of the common methods bad actors employ for online payment fraud are:
- Identity Theft: This is the most common method where bad actors compromise consumer accounts through account takeover fraud attacks and steal payment credentials, which are then used for fraudulent transactions.
- Phishing: A form of social engineering, bad actors use emails and fake websites to trick consumers into sharing their financial information such as credit card numbers, bank account details, and login credentials. Attackers then use these valid pieces of information for online payment fraud.
- Wire Transfer Scams: Bad actors manipulate consumers and businesses into loaning money with the promise of returning the money at a later date, which never happens.
- Merchant Identity Fraud: Attackers create fake merchant accounts on eCommerce platforms and ‘sell’ fictitious items at disproportionate discounts, only to vanish after receiving the payments.
- Refund Fraud: This refers to the fraud when attackers shop for an item and after receiving it falsely dispute a transaction. They request for a refund, claiming that the bought item was never received. In this way, they get the refund as well as the item.
- Clean Fraud: To execute this type of fraud, bad actors study the online payment fraud detection system that the target business has deployed. They then use stolen payment credentials to circumvent them.
- Payment Card Skimming: Attackers place skimming devices on legitimate card readers, such as ATMs or point-of-sale terminals, to capture card details when individuals swipe or insert their cards. They use the stolen information for fraudulent transactions or to create counterfeit cards.
- Chargeback Fraud: Also known as friendly fraud, it occurs when a legitimate cardholder disputes a valid transaction with their bank to receive a refund while still retaining the purchased goods or services.
- Business Email Compromise (BEC): Impersonate executives or vendors and trick employees into transferring funds or divulging sensitive information through email communication.
- False Billing: Bill for non-existent goods or services through fake invoices.
- Mobile Payment Fraud: Exploit vulnerabilities in mobile payment platforms to steal payment information, hijack accounts, or make unauthorized transactions.
- Cryptocurrency Scams: Use various schemes, such as Ponzi schemes, fake initial coin offerings (ICOs), or phishing attacks, to steal cryptocurrency from investors.
- Pagejacking: Hijack a part of the eCommerce website to redirect consumers to a fake website. This website serves as a conduit to infiltrate the business network’s security system.
- Interception or Man-in-the-Middle (MitM) Attacks: Intercept communication between parties involved in a transaction to manipulate payment details or redirect funds to accounts under their control.
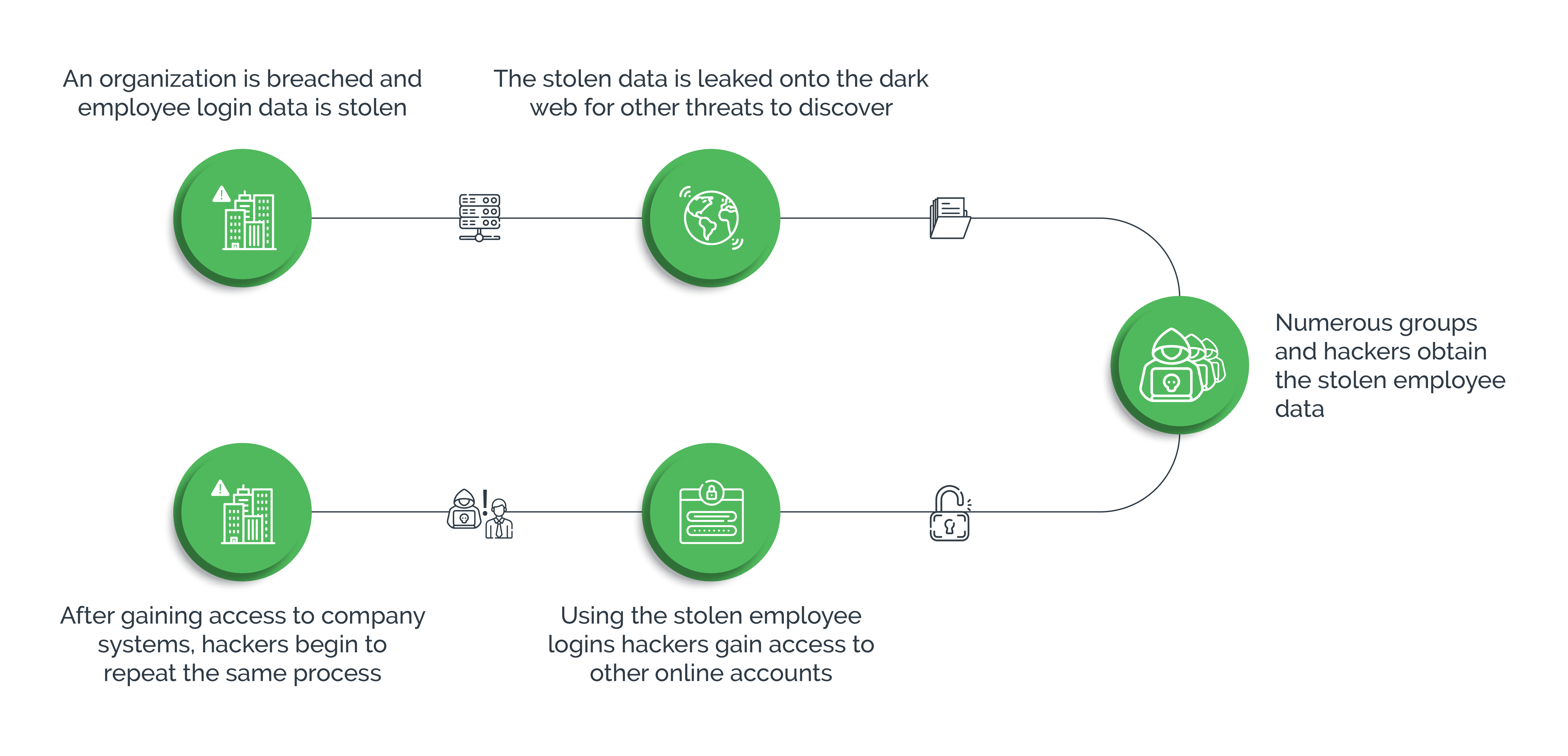
The Role Bots Play in Online Payment Fraud
Bots automate the attack, enabling hackers to execute the attack faster and at scale, while evading detection. Some ways in which bots facilitate fraud are:
- Account Takeover (ATO) Attacks: Hackers program bots to perform large-scale credential stuffing attacks on multiple websites or payment platforms. Successful attempts allow hackers to gain unauthorized access to user accounts, make fraudulent transactions, extract sensitive information, or use the compromised accounts for criminal activities such as money laundering, money muling, and so forth.
- Credential Harvesting: Bots scrape websites and forums where users may share their login credentials or other personal information. Attackers harvest this data and may sell it to third parties or use themselves for credential stuffing attacks.
- Phishing: Bots can automate the creation and dissemination of phishing emails, messages, or fake websites to trick users into sharing their payment or login information. By impersonating legitimate entities, bots increase the scale and efficiency of phishing attacks.
- Spam and Fraudulent Transactions: Bots can generate high volumes of spam transactions or purchases using stolen payment credentials or fraudulent accounts. This bot traffic can overwhelm online payment fraud detection systems and make fraud prevention harder for security teams.
- Ad Fraud: Bots generate fake clicks or impressions on online advertisements, causing advertisers to pay for non-existent or low-value ad engagements, resulting in financial losses.
- Manipulation of Financial Markets: Programmed bots can manipulate cryptocurrency markets or stock trading to artificially inflate or deflate prices for financial gain, by engaging in unscrupulous trading practices, such as pump-and-dump schemes or spoofing.
- Botnets for Distributed Attacks: Botnets are networks of compromised computers or devices under attackers’ control. Using botnets, attackers can orchestrate distributed denial-of-service (DDoS) attacks against payment processors and payment service providers to cause disruptions in payment processing systems and evade detection amid the chaos.
- Data Scraping and Skimming: Bots can scrape websites or intercept payment data during transactions, especially in eCommerce environments, to steal sensitive information such as credit card details or personally identifiable information (PII) for use in fraudulent activities.
Effective Ways to Detect and Stop Online Payment Fraud
Businesses cannot keep absorbing fraud losses as a cost of doing business. They need to implement effective steps to counter online payment fraud as it can be detrimental to their business continuity. Attackers are always on the lookout for potential targets and it is not a matter of ‘if’ but ‘when’ a business may be attacked next.
A successful attack not only causes financial losses but also has long-term repercussions such as damage to the brand image and customer churn. It is, therefore, essential that businesses adopt measures to detect and stop online payment fraud. Some of the common methods are:
- Address Verification System: Address verification service checks whether the billing address provided during the transaction matches with that on the issuers file. In case of a mismatch, further verification can be carried out.
- Card Verification Value: To authorize online transactions, consumers must provide the CVV code printed on the credit card. If the CVV provided does not match with the card details, the transaction is declined.
- Payer Authentication: Using this method, which is also called 3D secure, cardholders can generate a code to confirm their identity at the checkout stage. For instance, multiple account logins from the same device or sudden changes in device characteristics, indicating fraudulent activity, can be detected using device fingerprinting. This technique helps identify and track devices used in transactions through unique fingerprints on the basis of attributes such as IP address, browser type, and operating system, among others.
- Risk Scoring: Based on predefined rules and a number of other digital parameters, risk scoring tools evaluate the probability of transaction fraud. For instance, if a cardholder generally makes purchases within a certain geographical region, but suddenly attempts a transaction from an unrecognized location, the system may flag it as suspicious and trigger additional verification steps.
- Monitoring Large Transactions: Bad actors try to max out stolen credit cards quickly through large purchases. Any transaction that is disproportionately large compared to the regular transactions made from the credit card, should raise an alarm. For instance, if a transaction is suspicious and similar to known instances of fraud, such as rapid succession of large purchases, machine learning models can recognize fraud patterns and flag it for further review.
Limitations of These Techniques
Fighting fraud is a constant cat-and-mouse game between attackers and businesses. Being more creative and technically savvy, attackers are able to circumvent common online payment fraud detection techniques. This is because they spend time studying the anti-fraud mechanisms that businesses have deployed, and devise ways to bypass them. Unlike, say, a decade ago when attackers had to build their own attack infrastructure, they now have a whole cybercrime ecosystem – complete with attack toolkits, fraud-as-a-service, expertise, and 24X7 support – to leverage.
In response to new threats, businesses end up deploying multiple solutions that often work standalone and cannot communicate with each other. This not only creates a disjointed security infrastructure but also leads to information overload that needs additional efforts to collate – even before beginning the analysis – thus hampering protection efforts. Furthermore, these solutions tend to treat good users on par with bad actors, which can degrade user experience.
Businesses need a fresh approach to fighting online payment fraud that deters attackers long-term while keeping the interests of good users front and center. Using smart bot detection and risk mitigation software can help businesses thwart bot-driven credential stuffing attacks. Smart bot management solutions like Arkose Bot Manager use advanced algorithms and machine learning techniques to analyze patterns in user behavior, identify abnormal and automated login attempts, and detect anomalies or subtle differences between legitimate user interactions and automated bot activity.
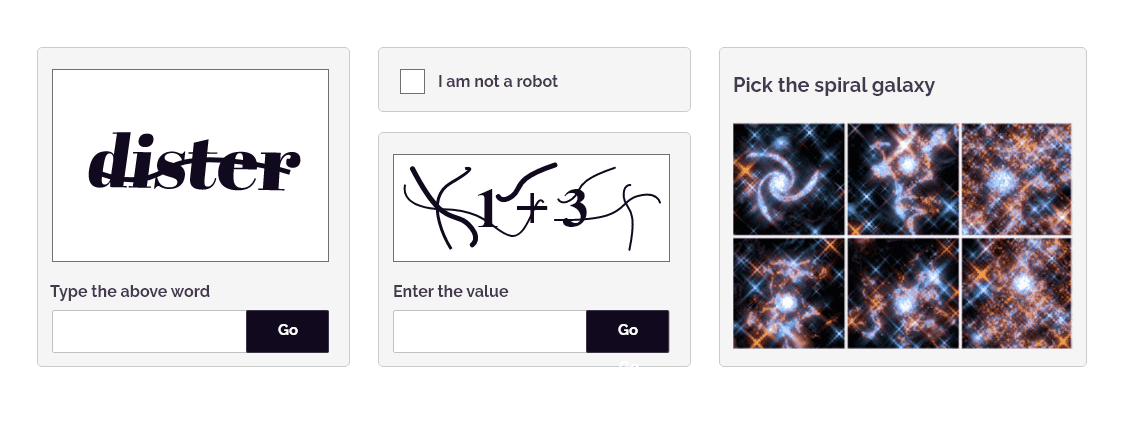
Further, advanced challenge-response authentication mechanisms, such as Arkose MatchKey challenges can prove more effective than legacy CAPTCHAs in stopping automated bot attacks. Businesses must add additional layers of security that deter bots from successfully logging in with stolen credentials with security measures such as rate limiting or multifactor authentication. Real-time monitoring and proactive blocking of suspicious IP addresses or bot-infected devices can help businesses prevent fraudulent access attempts, safeguarding user accounts and sensitive information from potential compromise.
Discover how Arkose Labs empowers banks, fintechs, and other financial institutions to fight online payment fraud.
