What Are Click Farms?
Click farms, also called fraud farms, are a group of workers which help perpetrate fraud attacks at scale. They are generally low-paid and low-skill resources, used to carry out large-scale attacks while keeping costs down and preserving ROI from attacks. They will be paid a set fee to carry out the same action over and over, such as registering for a bogus account or completing a visual CAPTCHA, which forms part of a larger orchestrated attack.
Most high-velocity attacks are carried out using automation, but with businesses deploying increasingly robust defenses against bots, the role of click farms is to evade defense, and carry out more nuanced attacks, while keeping costs low. These can include higher-value account takeover attempts, or activities that require human intelligence such as writing fake reviews, upvoting or commenting on videos, or writing phishing or spam messages to be sent to good users of a platform.
These workers either operate in a centralized location or through a distributed model where they are connected digitally, and often work on multiple devices at the same time for maximum efficiency.
What Are the Steps of a Click Farm Attack?
The global cybercrime ecosystem is a complex set of shadow services and enables fraudsters to tap into resources from across the globe to help accelerate their attacks and improve their ROI. This includes access to fraud farms, where large teams of lower-skilled workers are made available for hire.
The principal fraudster will typically engage with these workers through the Dark Web, paying in cryptocurrencies. Marketplaces even offer "as-a-service" models and support upgrades, mimicking the business models of legitimate service providers.
Click farm workers will sometimes work on mobile devices since they are smaller and less bulky to fit in a workstation and use a dozen or more at a time in order to carry out attacks at scale.
The Hybrid Model
The attacks can either be entirely carried out by the click farm workers or as a hybrid attack in tandem with malicious bots. An example of this hybrid model in action are organized "solving services", which utilize bots for credential stuffing attacks. Humans are then used to solve any authentication challenge, such as reCAPTCHA, or other forms of step-up authentication that can't be solved by bots.
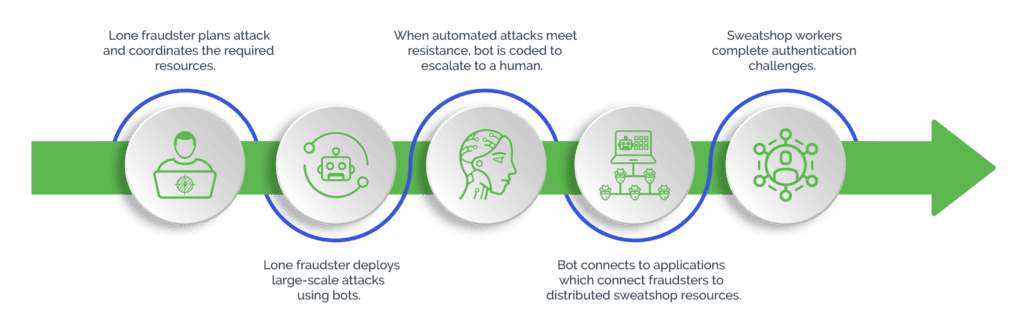
Why Are These Attacks on the Rise?
Fraudsters are increasingly augmenting their efforts by outsourcing fraudulent activity to humans, to increase the efficacy of their attacks. When defending against common attack types, such as account takeover, businesses often have solutions in place to detect malicious automated activity, but can struggle to detect the more subtle signs of human-driven fraud.
The rising human fraud problem highlights the socio-economic drivers behind fraud, and the increase in the number of people incentivised to get involved in cybercrime. Typically, these attacks come from countries where the average income is very low, and there aren't many opportunities for economic advancement. In many geographies where there is high unemployment and a devalued currency, even making $1/hour is desirable. And at the same time, costs for the fraudster are still kept low enough to make the attack profitable. In countries where financial fluctuations are severe, many "regular" people will turn to fraud to survive. For example, many in Venezuela have turned to farming the in-game currency of various online video games, since it is worth more than the country's paper currency.
Limitations of Current Approaches
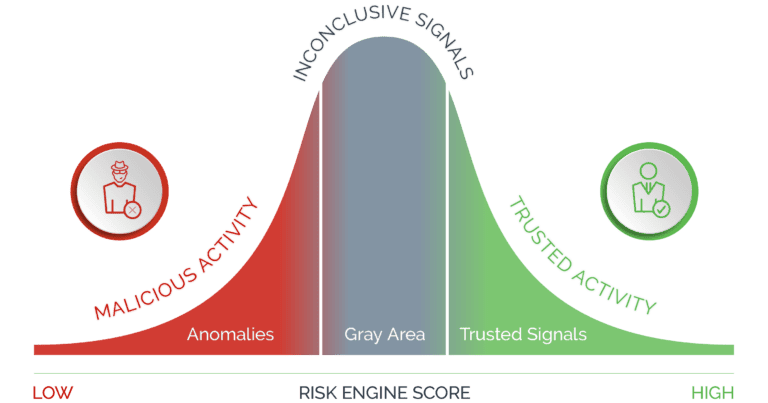
A lack of awareness of the click farm problem, means that there is a limited number of solution providers actively tracking and profiling this source of attacks. Data-driven fraud prevention solutions can be tricked using corrupted digital identity information, meaning that a growing volume of digital traffic does not give clear 'trust' or 'mistrust' signals. Instead it falls into a gray area in between.
Without secondary screening of this suspicious traffic businesses struggle to deal effectively with this issue. Additionally, businesses have struggled to implement an approach that works effectively across the bot, click farm and hybrid attack spectrum. Legacy approaches to deal with large-scale attacks are completely ineffective against human-driven attacks.
How to Combat Click Farm Attacks?
Analyze Real-Time Data
Optimal risk detection involves combining rich data intelligence with powerful analytics to discern intent and behavior in real-time.
That's why Arkose Labs analyzes data such as device and browser intelligence, canvas fingerprint, completion time, solve rate, and a host of other parameters to determine the risk profile of traffic. Rather than blocking or accepting transactions based purely on real-time data, however, secondary screening of risky traffic is vital for spotting human-driven attacks.
The platform also has an 'intelligence credit system' that scores the users based on the risk decisioning and their interaction with the challenges. This is used to deter brute force attacks by enabling appropriate defences to automatically trigger.
Determine Intent Based on Behavioral Patterns
Both lone fraudsters and click farms display subtle but identifiable signs of activity. To identify these telltale signs, the key is to evaluate fraud pattern data harvested across different websites and apps, and then ensure the correct tools are in place to flag risky users in real-time.
Detailed logs of user activity are provided to clients by Arkose Labs' servers. Each user session is tagged with a unique token with rich insights including telemetry data, risk level, and information from across the network.
Data from the Arkose Labs platform can be used to further train client's internal models, with data reinforcing good and bad user intent. This data includes telltale signals, reasons for suspicion flagging, fingerprint information, and more.
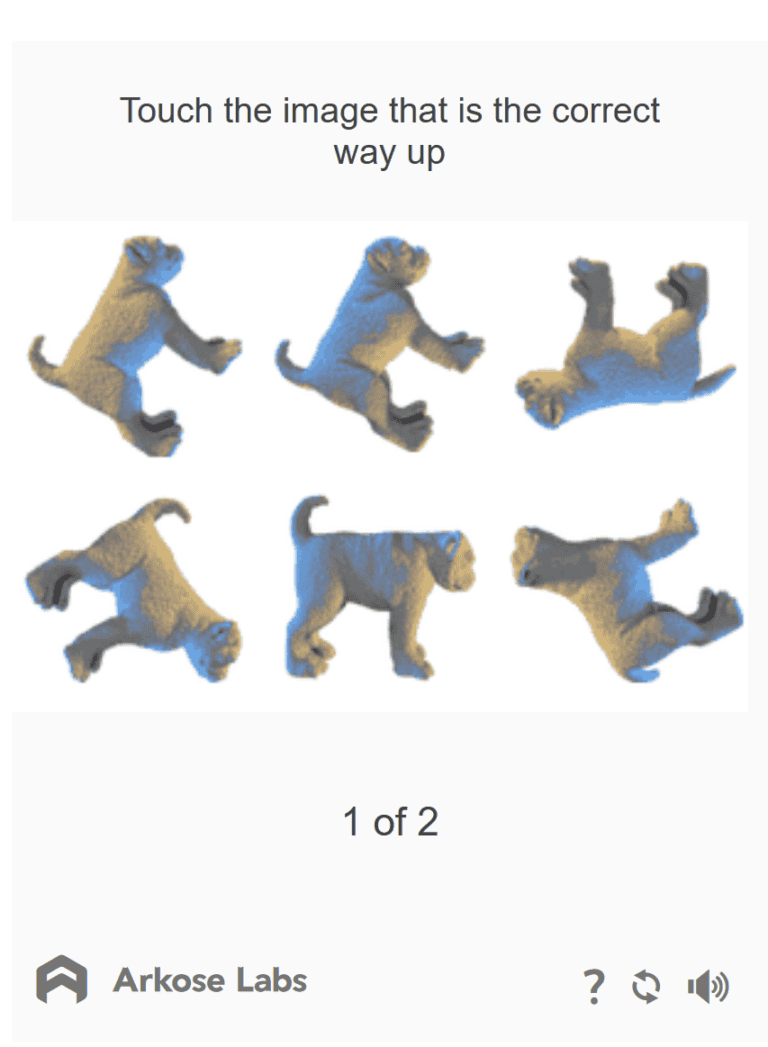
Time-Sapping Challenges
When suspected click farm traffic is identified, it is then presented with increasingly difficult and complex challenges that require an onerous amount of time and effort to solve. Since many of these workers have to meet an hourly quota, this friction compels them to quickly abandon attacks on those sites, and conduct attacks elsewhere. It should be noted these challenges are specifically reserved to frustrate click farm workers; good users will not have to endure them.
The solve patterns of these challenges are telling, and challenges can either be timed (to stop queued solve pipelines) or take a long period of human attention to solve (to sap efficiency). The platform tailors the type of challenge based on the nature of the attack.
To learn more about how Arkose Labs can help your business stop click farm attacks, click here to book a demo.


