What is a Brute Force Attack?
A brute force attack is a hacking technique where an attacker systematically tries all possible combinations of passwords or encryption keys until the correct one is found. This method relies on the attacker's ability to guess or crack the password through trial and error.
Brute force is simple but effective and requires less skill than other, more sophisticated hacking methods. That doesn’t make it any less dangerous, however. Once attackers gain access to a user account or network, they may steal sensitive data, install malware, or even shut down an entire system.
The Motives Behind Brute Force Attacks
Often the motive behind brute force attacks is to gain unauthorized access to sensitive information, accounts, and systems. These compromised accounts, credentials, and systems can then be used for financial gain through identity theft, fraud, and extortion.
These cyberattacks may also be motivated by a political or ideological agenda to disrupt critical infrastructure and services, defame people and businesses, and cause general chaos.
Attackers can use brute force attacks to:
1. Exploit Ads or Activity Data
Exploit ads and activity data for financial benefit by placing spam ads on popular websites, rerouting traffic to illegal sites, infecting websites with malware to collect user data, and testing network security and the strength of encryption protocols used by businesses and organizations.
2. Steal Personal Data
Steal personal data such as passwords, passphrases, usernames, and PINs to gain unauthorized access to sensitive information, such as bank accounts or personal files.
3. Spread Malware
Gain control of a target's system to use it as a launching point for wider attacks against other connected networks or systems, or simply to showcase their hacking skills.
4. Hijack Systems for Malicious Activity
Hijack systems for malicious activities such as a group of machines to launch a distributed denial-of-service (DDoS) attack with the intent to overload or crash a target's security and system. Botnets, networks of compromised computers, can also be utilized to speed up malicious activity.
5. Ruin a Company or Website’s Reputation
Damage the reputation of a company or website by altering confidential information, such as through defacing websites, leaking confidential data, or spreading false information online.
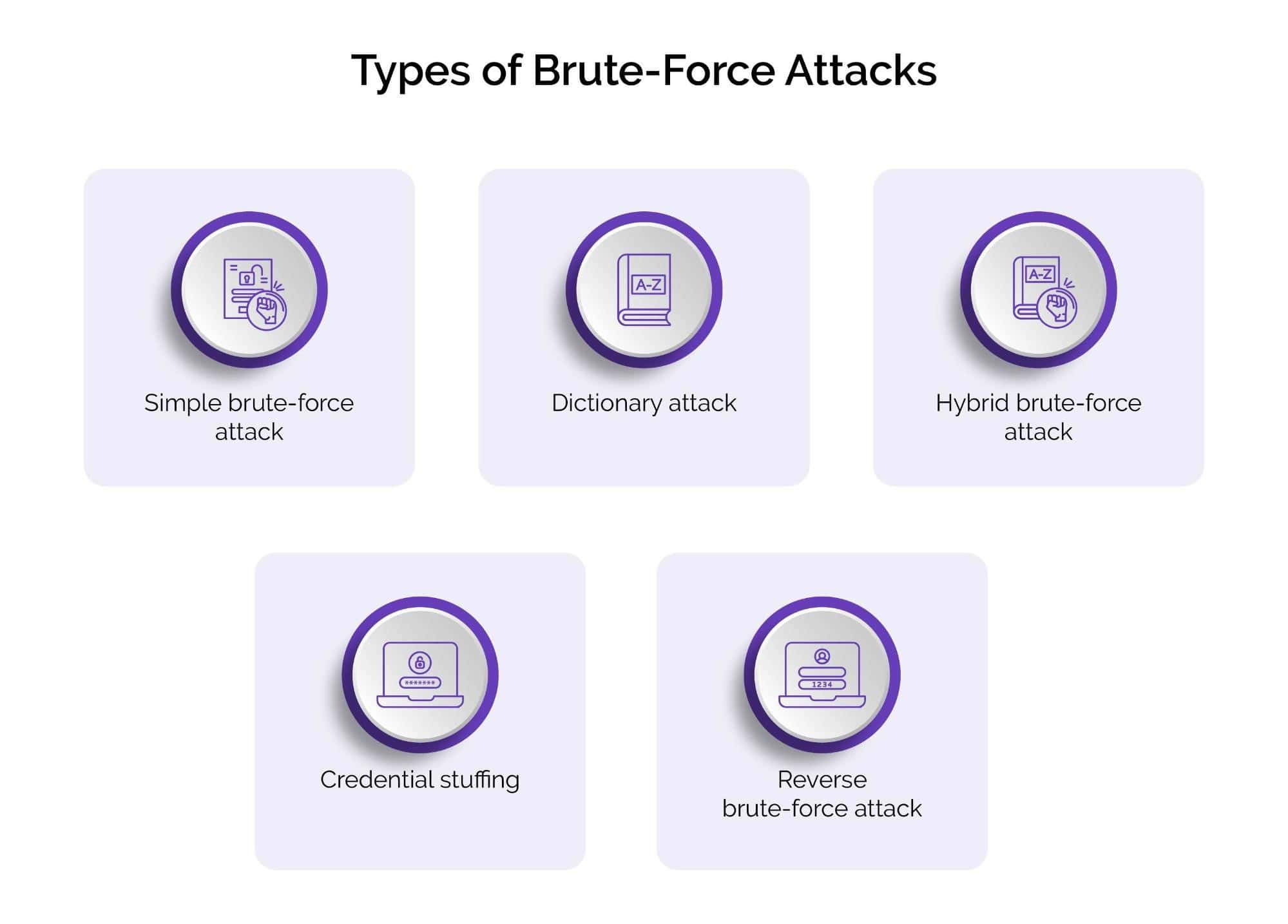
Types of Brute-Force Attacks
Brute force attacks can take several forms, each with its own strengths and weaknesses. Understanding the various types can help businesses take appropriate protective measures. Some common types are:
1. Simple brute-force attacks
Use automated software to test large quantities of possible combinations to decode passwords, PINs, and other forms of login data.
2. Dictionary attacks
Crack a password-protected security system by using a list -- or dictionary -- of common words and phrases. Although the success rate is lower, dictionary attacks are popular in hacking reused, common, weak or simple passwords.
3. Hybrid brute-force attacks
Combine elements of both simple brute force and dictionary attacks to increase the likelihood of success, such as modifying words in a dictionary by adding numbers or changing the letter case.
4. Credential stuffing
Use known, valid credentials that have been exposed in data breaches to gain entry into digital accounts and systems across several systems, since many people use the same username and password across multiple accounts.
5. Reverse brute-force attacks
Use a known password with various usernames or encrypted files to get network access. Many users have common passwords, such as "password" or “123456”, making it easier for attackers to guess usernames.
6. PIN Brute Force Attacks
Commonly used against mobile devices or electronic systems to try all possible Personal Identification Numbers (PINs) until the correct one is found.
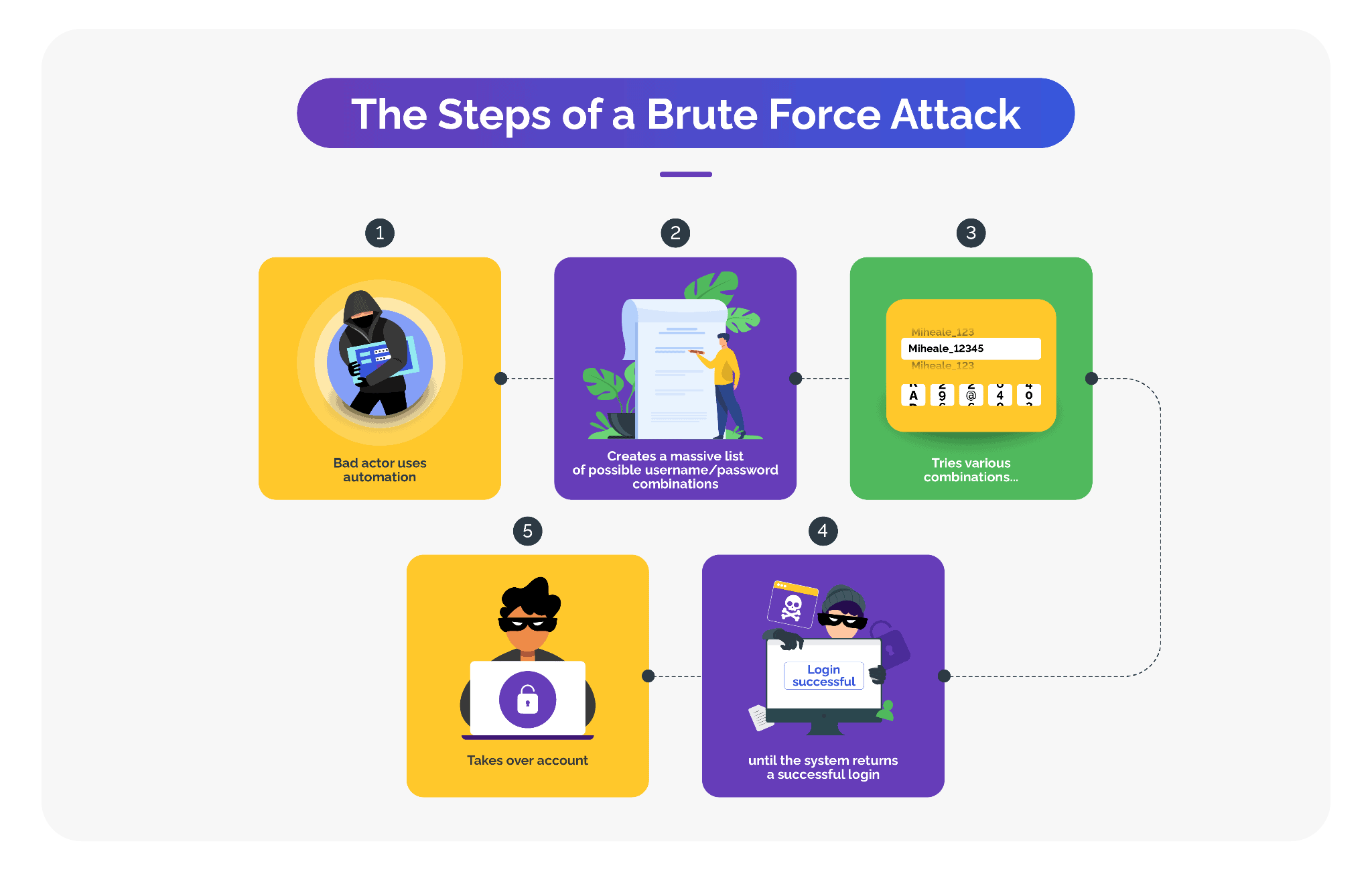
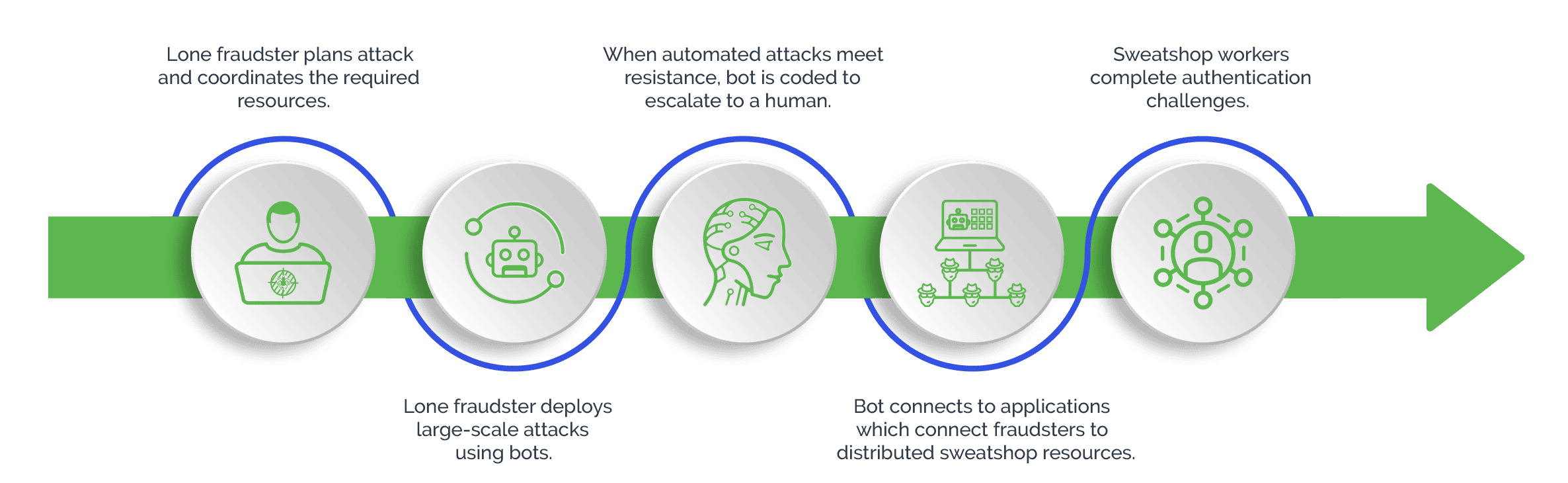
How Automated Brute Force Attacks Work
Using automated scripts, software, and bots, attackers exploit vulnerabilities, such as weak or easily guessable credentials, to quickly and repeatedly try different passwords.
In recent times, bots have become easily and cheaply available, enabling attackers to automate for greater efficiency and scale. Bots not only test various combinations rapidly and exhaustively, but also use dictionaries of commonly used passwords, or combine both the methods for greater success rates. Bots can operate non-stop and round the clock, making it possible for attackers to conduct persistent and automated attacks at scale.
Brute Force Tools
Brute force attacks leverage the computational power of CPUs, along with hardware accelerators such as graphical processing units (GPUs), and field-programmable gate arrays (FPGAs) to execute password attempts at accelerated speeds.
Some commonly used tools in brute attacks include Hydra, Medusa, John the Ripper and Ncrack. These tools use various techniques to crack passwords and have features that allow executing parallel attacks, SSH key recovery, and more. Since these tools are easily available and do not need much technical prowess, they are a popular choice.
That said, using strong passwords and encryption keys is an effective countermeasure. According to Cybernews, a strong password has the following characteristics:
- Is at least 12 characters long. The longer the better.
- Uses uppercase and lowercase letters, numbers and special symbols.
- Doesn't contain memorable keyboard paths.
- Is not based on your personal information.
- Passwords are unique for each account.
Brute Force Attacks Have a Significant Impact on Businesses
Brute force attacks can have significant negative impact on businesses. These attacks can expose sensitive data, including customer information and business data, to the risk of data breach. In addition to direct financial losses, businesses may face additional costs on mitigating the impact of the attack, implementing security measures, and addressing potential legal actions. This can strain the available IT and human resources, impacting the organization’s ability to focus on core business activities. In the event attackers are able to gain access to systems, the risk of fraudulent transactions and operational disruption increases that can affect productivity and impact the company's bottom line.
A significant negative impact is damage to brand reputation. Consumers and partners may lose confidence in the organization and hesitate to conduct business. This can lead to a decline in customer loyalty and negatively impact the ability to retain or acquire customers.
Highly regulated industries, such as banking and financial services, are mandated to comply with various data protection and privacy regulations. A successful brute force attack can cause data breach, resulting in non-compliance with the regulations and potential legal action.
Signs of a Brute Force Attack
To prevent unauthorized access and minimize the potential damage, businesses must deploy measures for early detection. Some signs are:
- A sudden increase in failed login attempts, especially from a single or a few IP addresses.
- Several consecutive failed login attempts for a specific user account.
- Login activity at odd or off-hours when regular users are less likely to be active.
- Login attempts from unexpected or unusual IP addresses.
- Systematic attempts using sequential or predictable passwords, such as incrementing numbers or simple variations.
- Multiple user accounts getting locked out due to excessive failed login attempts.
- A sudden increase in network traffic, especially focused on a specific service or application.
- Undue strain on systems and unexplained degradation in performance.
Strategies and Measures to Prevent Brute Force Attacks
To prevent brute force attacks, businesses should consider implementing the following strategies and measures:
- Bot Detection and Mitigation: Identify and stop automated bot attacks at scale so you stop credential stuffing, dictionary attacks and other brute force attacks at the edge.
- Strong Password Policies: Enforce strong and unique password requirements, while discouraging users to reuse or create easily guessable passwords.
- Account Lockout Policies: Temporarily (or permanently) lock user accounts after a certain number of failed login attempts. Define lockout thresholds to balance security with user convenience.
- Multi-Factor Authentication (MFA): Add an extra layer of security with MFA to add additional verification and make it harder for attackers to attack.
- Deploying CAPTCHAs: Traditional CAPTCHAs are usually ineffective, but Arkose Labs MatchKey Challenges can improve resilience to brute force attacks and automated solvers attempting to solve the challenges through random guesses and at scale.
- Rate Limiting: Restrict the number of login requests within a specific time frame to slow down the attack and prevent automated attacks.
- IP Blocking: Use intrusion detection and prevention systems to monitor and block IP addresses with suspicious behavior, such as an unusually high number of failed login attempts.
- Update and Patch Systems: Keep all software, operating systems, web servers, and applications, updated with the latest security patches.
- Web Application Firewalls (WAF): Implement WAFs to filter, monitor, and block malicious traffic between a web application and the Internet.
- Monitoring and Logging: Review logs to detect anomalies and unusual behavioral patterns and set up alerts to notify administrators of suspicious activity.
- Security Headers: Enhance security of web applications and prevent attacks using security headers, such as HTTP Strict Transport Security (HSTS).
- Penetration Testing: Conduct regular penetration testing to identify and address vulnerabilities in networks and systems before attackers can exploit them.
- Security Training: Educate users about the importance of using strong passwords, recognizing and responding to phishing attempts, and following the best practices for account security.
Steps After Detecting a Brute Force Attack
Once a brute force attack is detected, businesses must take prompt and decisive action to minimize potential damage to the systems. Some steps that businesses can consider taking after detecting a brute force attack are:
- Respond: Initiate an immediate response, such as blocking the attacking IP addresses or locking out affected user accounts.
- Isolate Accounts: Identify, isolate, and lock out the compromised or targeted user accounts to prevent unauthorized access during investigations.
- Investigate: Determine the extent of the attack. Identify the attack vector to understand how the attackers gained access. Review logs, analyze patterns, and assess the potential impact on sensitive data.
- Change Compromised Credentials: For compromised accounts, request users to immediately change weak passwords with strong and unique passwords.
- Enhance Security Measures: Strengthen security measures. Implement additional security layers, such as multi-factor authentication (MFA), adjust account lockout policies, or enhance rate-limiting mechanisms.
- IP Blocking: Blacklist or permanently block IP addresses associated with the attack to prevent repeat attempts.
- Alert Users: Inform affected users, explain the actions taken to mitigate the attack, and recommend changing passwords or enabling MFA.
- Update Security Policies: Use the findings to update security policies, such as account lockout thresholds and implement additional measures to fill the gaps.
- Patch and Update Systems: Update all systems, software, and applications with the latest security patches.
- Incident Documentation: Document the details of the brute force attack, complete with the timeline, methodology, and the response.
- Monitor for Recurrence: Continuously monitor logs and network traffic for any signs of repeat attacks.
- Post-Incident Analysis: Conduct a post-incident analysis to identify areas of improvement in security measures, response procedures, and user awareness.
Thwart Brute Force Attempts with Arkose Labs
Brute force attacks are serious cybersecurity risks that can expose data to breaches and abuse. Arkose Labs helps businesses identify and stop automated brute force attacks early in the tracks to ensure protection of data and digital accounts.
Using a combination of the latest technologies and real-time risk assessment, Arkose Labs evaluates the authenticity of users. Depending on the risk profile, users face Arkose MatchKey challenges to prove their authenticity.
While good users can solve these challenges quickly, bots and automated scripts fail instantly. This is because Arkose MatchKey challenges are trained against the most advanced optical vision technologies, making them inherently resilient to automatic solvers and bots of various advancement levels. As a result, automated bot attacks fail instantly. Persistent human attackers and click farms face a continuous stream of challenges that keep becoming increasingly complex. Even if the attackers tried to create automated solvers, they would fail, given the wide repository of variations for each of the several Arkose MatchKey challenges.
With dwindling returns and mounting investments in terms of time, effort, and additional resources, the attack becomes financially non-viable, defeating the purpose of the attack. As a result, attackers give up for good and abandon the attack. Therefore, Arkose Labs helps businesses protect their consumers and business assets from both human and bot-driven brute force attacks.
Arkose Labs backs up its solution with 24X7 SOC support, actionable insights, and the latest threat intelligence to help its partners quickly identify known and emerging threats and take timely appropriate countermeasures.
For more information about MatchKey challenges, request a demo today.