The utility of telecommunications services is often taken for granted. Whether it's for personal use or for a business, these services have become ubiquitous—and more important than ever before in our daily lives. Customers now expect connectivity at the touch of a finger, while also demanding increased account and data security.
The need for telecom services, as well as their prominence in our day-to-day lives as critical infrastructure, have made the industry a prime target for cyberattacks. Telecom companies have a large footprint, including individual user accounts and business endpoints, that can lead to a range of vulnerabilities that hackers can exploit to steal personal information and more.
Want to learn more about SMS toll fraud? Catch up with our webinar, Flipping the Script: How Stopping SMS Fraud Maximizes Your Own ROI
What makes the telecom industry vulnerable?
Telecom (Telco) companies all around the world are increasingly becoming a target for cybercriminals. Telecom infrastructure cost, lack of regulation, and aging/legacy systems are some of the reasons why they are vulnerable. Additionally, telecom operators are vulnerable to several network problems, including network misconfiguration, supply chain issues, and unsecured Wi-Fi.
Additionally, the nature of the telecom industry makes it attractive to hackers who wish to exploit their wide access to sensitive information, including customer credit card information and individual data. Another issue is that employees and insiders may not be aware of the threats they may pose to the system.
Exploring the telecom cybersecurity landscape
Cyberattacks against the telecom industry are becoming more prevalent and sophisticated, with many different types of tactics being utilized. Cybercriminals use tactics like phishing, man-in-the-middle (MITM), malware, and denial-of-service (DoS) attacks to gain access to sensitive information or disrupt services. The consequences of a successful telecom cyberattack can be severe, including data breaches, financial losses, and reputational damage.
Also, sensitive information that telecom businesses require customers to divulge, like Social Security Numbers and credit card information, can mean big bucks to cybercriminals. Keeping networks secure is not only critical for safeguarding against cyber threats but also for protecting this sensitive customer data as well.
Common types of telecom cyberattacks
Telecom networks are frequently targeted by cybercriminals using various types of attacks. As mentioned earlier, cybercriminals also sell customer and employee personal identifiable information (PII) on the dark web. Service providers can even also be at risk of being infiltrated by state-sponsored actors seeking to mine data and intelligence.
Finally, third-party vendors with remote access can pose a significant risk for telecom users as data breaches at these vendors can expose valuable information. Here are a few common cyber threats facing the telecom industry:
Denial of service (DoS)
Telecom providers are increasingly vulnerable to cyberattacks, with Distributed-Denial-of-Service (DDoS) attacks, enabled by bots and botnets, being one of the most common methods used by attackers. DDoS attacks on telecom providers can cause significant financial losses and network disruptions.
Session hijacking and Man-in-the-Middle (MITM) attacks
Telecom networks can be vulnerable to cyberattacks, specifically session hijacking and man-in-the-middle (MITM) attacks. These attacks can compromise both network security and that of user accounts. One way cyber criminals can gain access to user accounts is by intercepting two-factor authentication codes as part of an MITM attack. This can lead to International Revenue Share Fraud (IRSF) or SMS Toll fraud.
International Revenue Share Fraud (IRSF) and SMS Toll Fraud
IRSF, also called SMS toll fraud or SMS pumping, is a growing concern for businesses across industries. At its core, IRSF is often enabled by telecom resources and infrastructure to initiate unauthorized calls to premium numbers. These calls are then charged to the victim’s phone bill, resulting in significant financial losses. And when performed at scale, the costs for businesses can quickly rise to millions of dollars.
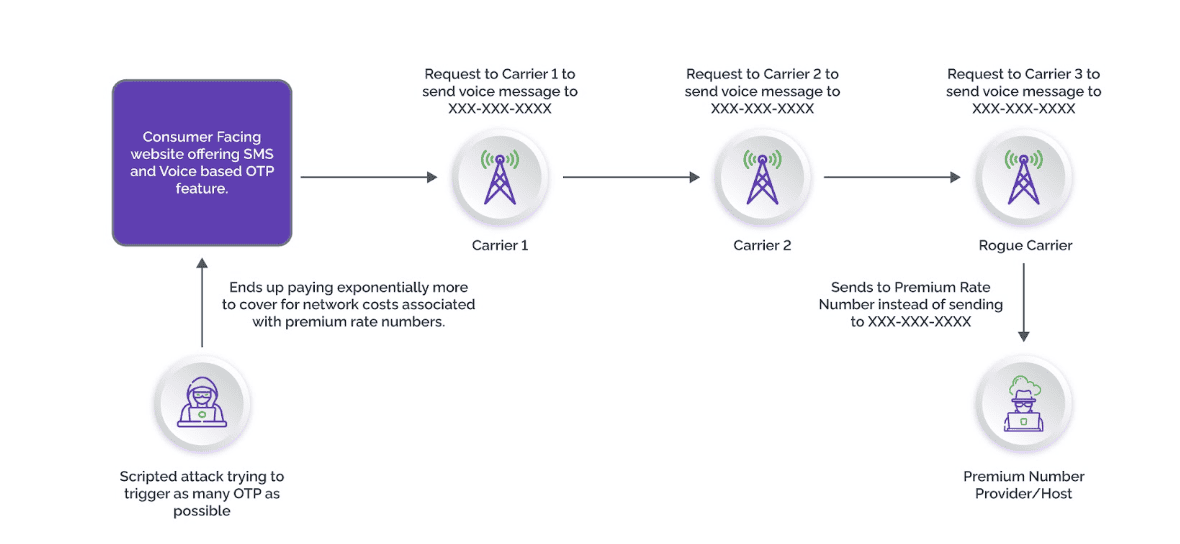
Struggling with IRSF? Use our calculator to estimate potential cost savings from stopping it.
Phishing and social engineering
For cybercriminals looking to gain access to user accounts, phishing and other social engineering attacks often provide their entryway. By creating fraudulent web pages or email messages that imitate popular telecom brands, cybercriminals can trick unsuspecting customers into providing their login credentials, credit card numbers, and more. In the instance of a user providing their login credentials, these accounts can be taken (ATO) over by cybercriminals and used for downstream attacks and fraud or sold on the dark web.
Effective strategies to mitigate telco risks
Cyberattacks can be devastating to both the telecom industry and its customers. Third-party providers may be used to gain entry into the network, so it is essential to monitor and secure them properly. One of the most important ways to mitigate these threats is investing in a bot management solution, combined with 24/7 managed services that act as an extension of your own security team. As bots enable most attacks against the telecom industry, stopping advanced automated threats is imperative.
How to Prepare for Future Telco Attacks
To prevent expensive downtime and loss of data, telecom operators should identify and address potential vulnerabilities in their network infrastructure. Additionally, they should take essential steps like implementing strong authentication protocols, encrypting sensitive data, and regularly monitoring networks to secure their infrastructure and data from cyber threats. Consumers should be regularly informed of the importance of difficult and complex passwords and ensuring that they don’t reuse the same password across multiple accounts.
Arkose Labs secures telecom providers from cyberattack
Telecom industries play a vital role in our daily lives, but they are also one of the top targets of cyber attackers. Arkose Labs removes the economic incentive to cybercrime by sabotaging attackers’ ROI and rendering the threat impractical and unaffordable. This is a fundamental shift from prevention to cybercrime deterrence.
Global enterprises trust Arkose Labs for attack detection and prevention while protecting the user authentication touchpoints that are often targeted by threat actors. By rooting out cybercrime early, and stopping it at targeted entryways, businesses are able to strengthen relationships with customers by offering an increasingly secure financial platform without sacrificing a positive user experience.
If you want to learn more about how Arkose Labs secures businesses from advanced and automated threats like bots, reach out to us and book a meeting today.
- What makes the telecom industry vulnerable?
- Exploring the telecom cybersecurity landscape
- Common types of telecom cyberattacks
- Denial of service (DoS)
- Session hijacking and Man-in-the-Middle (MITM) attacks
- International Revenue Share Fraud (IRSF) and SMS Toll Fraud
- Phishing and social engineering
- Effective strategies to mitigate telco risks
- How to Prepare for Future Telco Attacks
- Arkose Labs secures telecom providers from cyberattack


