Recently, one of the world's most renowned video game developers found themselves ensnared in a financial quagmire. They were hemorrhaging an astonishing $1 million each month due to a sophisticated cybercrime known as SMS toll fraud.
This game developer's Achilles' heel lay within the registration process, where attackers exploited a vulnerability in the authentication system to create massive numbers of fake accounts. These large-scale attacks left the company burdened with the onerous costs of SMS toll charges sent via premium-rate numbers. The company was able to staunch the bleeding by implementing processes to protect their registration flows, but only after incurring significant financial losses.
Unfortunately, this video game company is not alone in facing the hidden threat of SMS toll fraud. This type of cyber attack is escalating, and it is becoming increasingly vital for online gaming companies to fortify their defenses against it.
SMS toll fraud in the gaming industry
While much of the talk about cybercrime in the gaming industry revolves around account takeover fraud, fake account creation, auction house abuse, phishing, microtransactions fraud, and the like, companies are beginning to turn their focus on SMS toll fraud.
In SMS toll fraud, also known as SMS pumping, artificially inflated traffic fraud, or international revenue share fraud (IRSF), attackers use bad bots and automated scripts to input premium-rate mobile numbers en masse.
The unsuspecting business, meanwhile, implements user authentication procedures such as two-factor authentication (2FA) or multi-factor authentication (MFA) via SMS, and thousands of these fraudulent SMS messages are sent through premium-rate mobile numbers. By colluding with some mobile network operators (MNOs), the attackers are able to generate income through a share in the revenue derived from the fraudulent SMS messages.
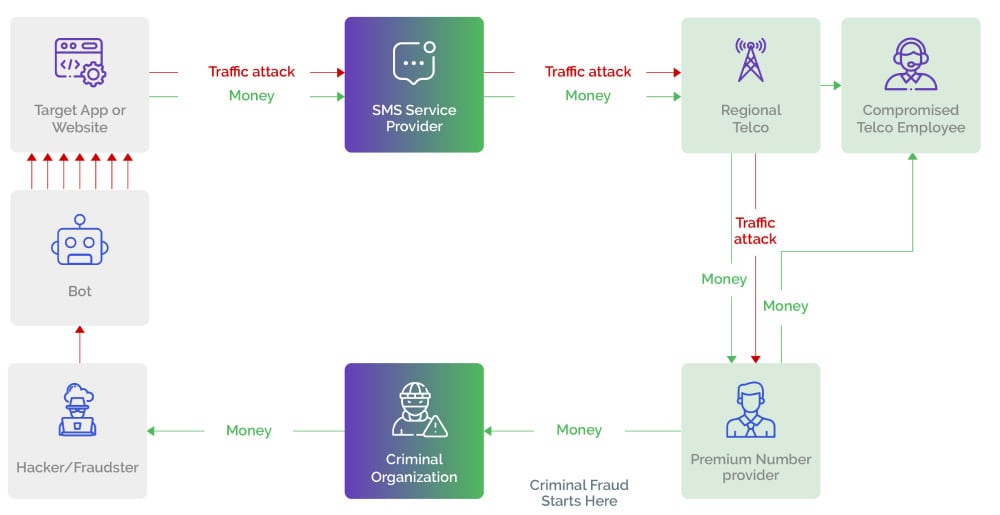
Challenges gaming companies face in detecting SMS toll fraud
One of the reasons SMS toll fraud is so difficult to detect is that by the time the business receives the outsized bill from the telecom company, the bad actor has already taken the money and moved on to the next victim. This attack vector occurs across multiple industries, but detecting SMS toll fraud can be especially challenging for gaming companies because of several factors:
- The large volume of SMS messages generated by gaming platforms for myriad uses, including promotional campaigns, in-game notifications, and player communities, makes them attractive for SMS toll fraud.
- Gaming platforms attract gamers from several geographical locations, which allows fraudsters to hide behind the anonymity of the internet and use international mobile numbers without raising suspicion.
- Cybercriminals tend to time their attacks when defenses are low, such as during the weekends or local holidays.
- Gaming companies are bound by regulations that deter them from intrusive monitoring, which may make it more difficult to detect attacks.
As a result, traditional fraud detection systems are often inadequate for identifying SMS toll fraud attempts.
Detecting automated SMS toll fraud attacks
Finance departments are usually the first group to detect SMS toll fraud, when they are presented with inflated telecom bills and realize that the SMS flows have been exploited. But there’s not much they can do, because the fraud has been identified only after the damage has been done. The inability to reverse the SMS messages that have already been initiated exacerbates the challenge. And since SMS is one of the most cost-efficient and effective channels of communication, gaming platforms cannot completely stop its use.
As mentioned earlier, SMS toll fraud makes economic sense for cyber attackers when it is executed at scale through automated non-human traffic. This is where gaming platforms can intercept the criminals and prevent the impending damages. By using bot detection solutions, these platforms can identify automated bot attacks and stop them much before they reach the SMS workflows.
It is important to note that using outdated bot mitigation solutions such as legacy CAPTCHAs will not provide the level of protection needed, and may end up adding to the overall security costs while making the platform vulnerable to repeat attacks.
Gaming platforms must, therefore, choose smart bot management solutions that can accurately identify malicious bots as well as click-farms that take over the attack when these intelligent bots can’t get through.

How Arkose Labs fights SMS toll fraud in gaming
Arkose Labs specializes in stopping automated SMS toll fraud attacks with our award-winning approach to bot management, backed up by an industry-first $1 M warranty.
Using the latest digital technologies and Arkose MatchKey, the best CAPTCHA challenge-response system on the market today, Arkose Labs uses targeted friction to stop bots, scripts, and click-farms from initiating large volumes of fraudulent SMS messages. Arkose Bot Manager leverages risk-based authentication and combines it with proprietary challenge-response authentication mechanism to identify bots and malicious human users, without degrading the gaming experience for genuine players.
While bots and scripts fail instantly, human attackers must clear more challenges that keep increasing in complexity. This wastes the time, effort, and resources of the fraudster, and renders the attack financially non-viable. As a result, attackers are forced to abandon the attack and give up for good.
Like a true partner, Arkose Labs offers 24x7 SOC support and shares data-backed insights, signals and attributes to empower gaming platforms to identify and stop evolving tactics of SMS toll fraud attacks.
To learn how you can ensure long-term protection of your gaming platform from SMS toll fraud attempts, book a demo now.


