As the holiday season draws near, there's a familiar buzz in the air, and it's not just the sound of carolers singing or the scent of freshly baked cookies. For those paying attention to the cyber threat landscape, it is also the season for denial of inventory attacks—a digital threat that has become increasingly prevalent in our consumer-driven world. Here, we explore this pressing threat of this virtual stockpiling, uncovering the motivations behind it and examining its impact on today’s businesses.
From online retailers preparing to meet the surge in holiday traffic to cybercriminals strategically amassing their own goodie bags, 'tis the season for inventory hoarding, a disturbing cyber threat looking to prey on heightened spending and online shopping.
What is denial of inventory and how does it work?
A denial of inventory attack, also known as inventory hoarding, has gained prominence in the digital age and is characterized by the digital accumulation of assets, resources, and goods in online spaces. This multifaceted threat takes place across industries, seriously impacting the digital experience for companies and legitimate customers.
This type of inventory fraud happens when bad actors amass assets, often with the intent of retaining them for potential future use, resale, or investment. These assets are typically diverse and far reaching. They could be digital, like cryptocurrencies, online coupons, or virtual real estate, or they could be tangible assets such as sneakers, concert tickets, and the like.
Mounting a denial of inventory attack happens through various channels, including infrastructure, payload, efficiency—and shopping bots. The attacker requires ample computing power and a range of resources, including proxies, rotating IP addresses, VPNs, and more, to enable the shopping bot's smooth operation and safeguard against detection by various bot detection and mitigation solutions.
In order to effectively run the shopping bot for items with restricted availability and avoid unnecessary resource consumption, the attacker must accurately determine the product's launch date and time, often employing a preliminary spy bot or recon bot to scan and index the e-commerce site for crucial information regarding the item release.
The attackers must establish an operational system tailored to their specific goals, where, for instance, if the aim is product scalping, it necessitates an adequate number of credit cards and storage locations, whereas actions designed to tarnish the site's reputation may not demand such provisions.
Shopping bots involved in denial of inventory attacks
The rise of shopping bots, or scalper bots, has added a new dimension to online hoarding. Automated software programs designed to purchase highly sought-after products online, often in bulk and at rapid speeds, make it challenging for genuine consumers to access these items. Fraudsters can use these bad bots to acquire assets and goods in large quantities, causing scarcity and driving up prices in secondary markets.
There’s even a category of shopping bots devoted to one particular attack: sneaker bots. The global sneaker resale market is projected to reach a staggering $30 billion by 2030, and recent studies reveal that over 70% of web traffic during limited-edition sneaker sales is attributed to bots.1 These malicious actors continuously adapt, deploying advanced bots that mimic genuine user behavior and legitimate system activities to evade detection.
A denial of inventory attack takes place when shopping bots repeatedly place an online product or service in the shopping cart without actually completing the transaction. This tricks the e-commerce site into thinking the item is out of stock, when in fact it is being hoarded from legitimate buyers. Although the attackers and their malicious bots do not necessarily complete the transaction, they find other ways to monetize the threat.
After analyzing 1.6 million visits to e-commerce sites, the cybersecurity firm CHEQ found that about a fourth of all Black Friday shoppers in 2022 were bots. The same study also revealed that out of 765,000 visits on Cyber Monday last year, one in five were from automated bot traffic.2
Malicious actors have the option to craft their own customized bots or deploy readily available bot tools tailored for cybercrime-as-a-service. Notable examples encompass software like EasyCop, NikeSlayer, SupremeBot, among others. The proliferation of e-commerce platforms and the surging trend in online shopping have given rise to a diverse range of shopping bots accessible in the market. These bad bots are highly adaptable and can be tailored to target particular websites or even specific products and services across the digital landscape.
Motivations behind denial of inventory
Understanding the context around inventory hoarding is key to recognizing its impact on digital economies, cybersecurity, and online ecosystems. Motivations behind this attack are varied, with fraudsters often driven by the prospect of asset appreciation, the belief that resources may become scarce, or the anticipation of future benefits.
Money is always a motivator. Fraudsters employ shopping bots to obtain and stockpile coveted, scarce items in high demand. Subsequently, they capitalize on this by reselling these items at inflated prices, thus creating a profitable avenue for quick cash generation.
Competitive motives are another factor. In such instances, the denial of inventory attack is initiated with the intention of tarnishing a business’ reputation and diverting potential customers to a competitor's website, where the product or service remains accessible.
Main industries affected by denial of inventory
While the practice of inventory hoarding can have broad implications across a wide range of industries, several sectors are significantly impacted by this digital threat:
- E-commerce: Denial of inventory practices in e-commerce platforms, whether involving pricing adjustments or inventory, can disrupt stable pricing structures and consumer access to products, leading to unpredictability in the market. Artificial scarcity stemming from hoarding impacts consumers' ability to access products and discounts in online stores and retail sites, hindering their decision-making and procurement. Bad actors who collect and resell digital coupons and discount codes can directly impede business revenue streams, causing disruptions in sales and undermining the effectiveness of these promotional tools.
- Online gaming: Denial of inventory in online gaming poses significant challenges, particularly in virtual economies where players buy, sell, and trade virtual items. These online hoarding practices create scarcity, inflating the value of specific in-game assets and disrupting the economy, making it difficult for newer or casual players to obtain sought-after items. Maintaining game balance is essential for fairness and competitiveness, but hoarding can upset this equilibrium, giving advantages to players with extensive collections or access to hoarded items on secondary markets like the darknet, impacting the gaming experience for others.
- Travel and hospitality: Travel and hospitality companies are significantly affected by denial of inventory attacks, with consequences including lost revenue due to canceled bookings and customer dissatisfaction, operational challenges like rebooking and resource allocation, potential damage to their reputation, financial impact through refunds and regulatory compliance issues, and a competitive disadvantage when reliability falters. Travel site owners depend on precise inventory management, and any disruption in reservations and bookings can lead to both short-term and long-term negative consequences, prompting investments in resilient systems, disaster recovery plans, and flexible customer policies to mitigate the impact of such attacks.
Arkose Labs takes down bots and cybercriminals
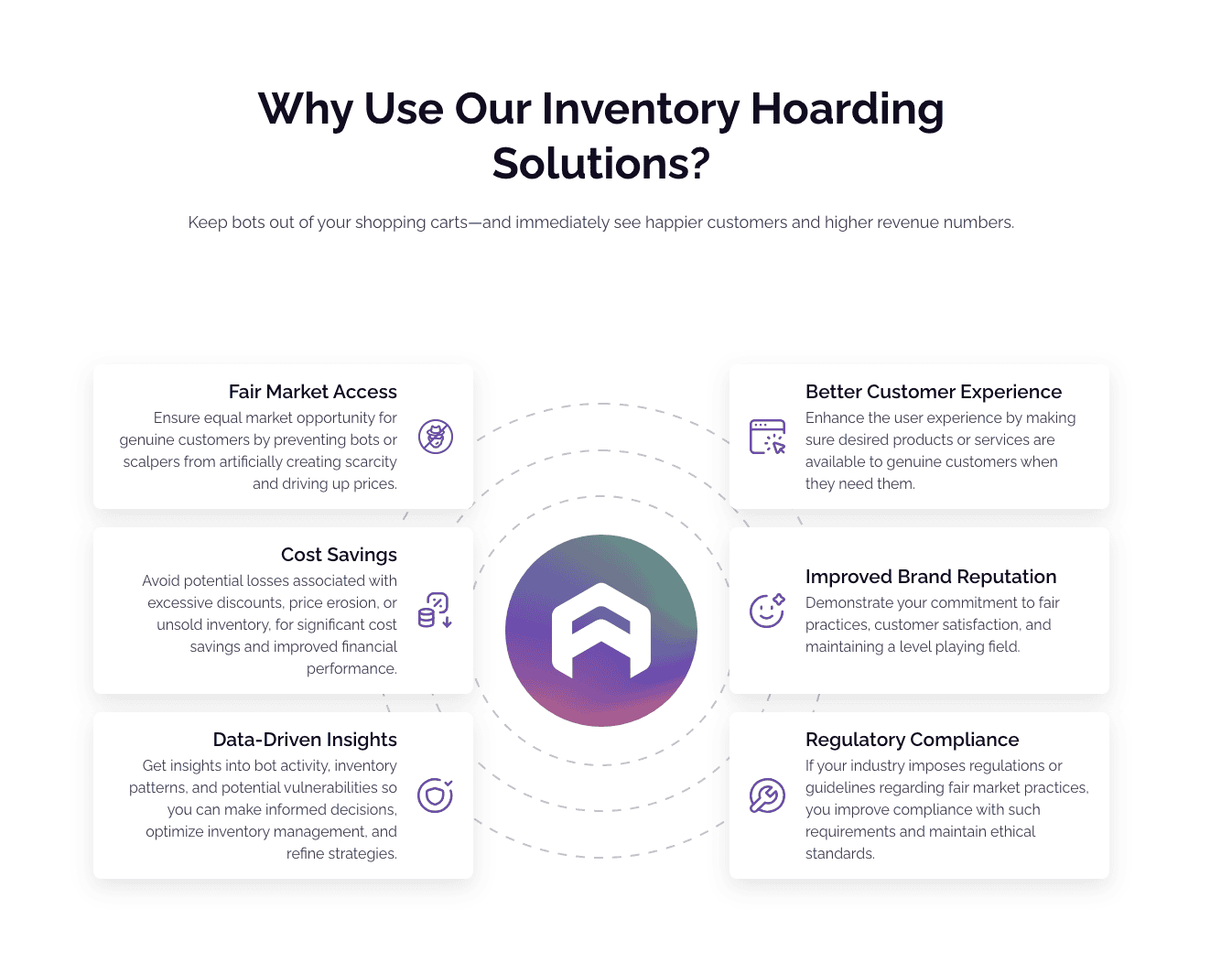
As a leader in bot prevention, Arkose Labs provides online businesses with an effective shield against bot attacks through the Arkose Bot Manager product. Our innovative solution employs advanced technology and behavioral analysis to detect and thwart malicious bots, making it difficult for attackers to disrupt online operations—and easy for legitimate shoppers to get what they want.
By actively disrupting the economics of cyberattacks, Arkose Bot Manager not only safeguards a company's reputation but also reduces financial losses due to fraudulent activities. Arkose Bot Manager is a crucial tool in defending against the rising threat of shopper bots and ensuring a secure online environment.
Find out how Arkose Labs can keep your enterprise safe this holiday season.
Talk to an expert today!



