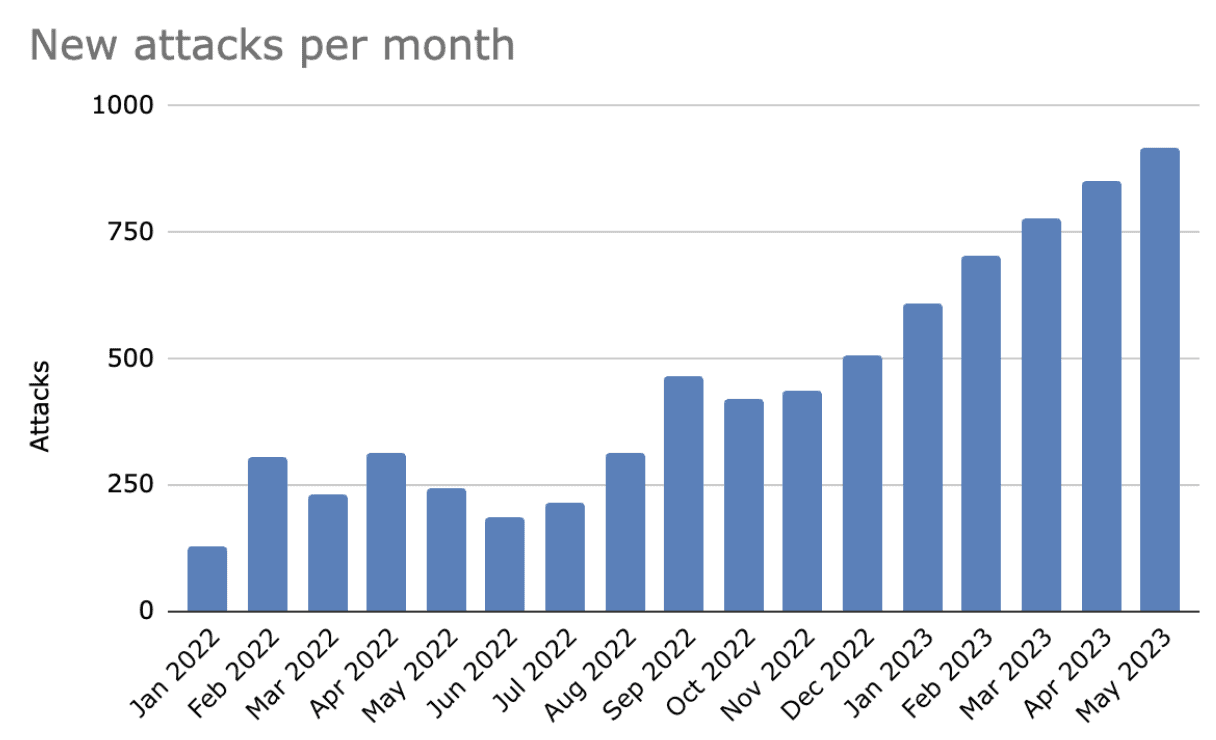
Take heed – bot attacks are on the rise.
Here at Arkose Labs, we are experts in detecting and combating cyberattacks, particularly those carried out by cyber bots. Our team is constantly surveilling the evolving landscape of online threats, utilizing techniques to identify and neutralize malicious bot activities. One of the ways we stay up to date is by monitoring the Arkose Labs Global Network, a vast network of data sources and intelligence feeds that provides real-time insights into emerging threat patterns.
In the past six months, we’ve seen explosive growth in the acceleration of attacks across our platform. While a small portion of this can be attributed to a natural increase in organic traffic growth, the data clearly show attacks are increasing at a faster rate than benign traffic. Compared to just a year ago, cyberattacks have nearly quadrupled, and they show no sign of slowing down.
Fortunately, businesses have the ability to protect themselves against attackers with the right information and tools. This blog post explores the reasons behind the increasing prevalence of bot attacks, examines some of the latest attack methods, and reviews the technology available to detect and prevent cyberattacks effectively.
Read more about today’s attack trends:
Explosive Growth – Why Now?
Digital interactions have transformed how we live and work. But the dynamic nature of online technology has also created opportunities for malicious actors, particularly bots, to exploit vulnerabilities. Botnet operators are employing advanced techniques:
- Fast flux rapidly changes IP addresses to evade detection
- Domain generation algorithms (DGAs) dynamically generate numerous domain names for communication
- Polymorphic malware changes code structure and signatures, confuses antivirus software
- Encryption and tunneling techniques conceal malicious traffic
- Resilient command and control (C&C) architectures make botnets harder to dismantle
- Cloud-based infrastructure offers scalability and anonymity
There’s also the growing availability of Cybercrime-as-a-service (CaaS) platforms, which make it easy for even unskilled attackers to launch botnet attacks. These platforms offer pre-configured botnet frameworks, user-friendly interfaces, and services like DDoS capabilities so attackers can quickly set up and control botnets without extensive technical skills.
Multiple use cases to defend against
By accessing valuable assets, financial information, customer details, and other data that can be exploited or sold on the black market, bots can reap huge monetary gains – all while inflicting devastating effects on their targets. They do so through a variety of use cases:
Account takeover: This is a type of identity theft where criminals gain access to someone's personal details in order to commit illegal activities. Once in possession of these credentials, the criminals can impersonate the account owner (hence the name account takeover), potentially leading to financial fraud, unauthorized transactions, or other forms of illicit behavior.
Credential stuffing: Credential stuffing is a cyberattack technique where stolen usernames and passwords from one website are used to gain unauthorized access to other platforms. Exploiting the common practice of password reuse, cybercriminals employ automated tools to test stolen credentials on multiple websites. This poses a significant risk as compromised credentials can lead to account takeover and subsequent security breaches.
SMS Toll Fraud: Also called SMS fraud or SMS pumping, this threat involves sending text messages to mobile phone users without their consent, charging them premium rates. It often uses short codes or premium-rate numbers. Cybercriminals may employ phishing or malware to deceive users into subscribing to costly services or unknowingly agreeing to receive higher-rate messages.
New account fraud: This attack involves the creation of fake accounts on digital platforms for illicit purposes beyond their intended use. This includes setting up bogus profiles for phishing, gaming accounts for bot-driven asset accumulation, and fraudulent financial accounts for obtaining credit. New account fraud creation fuels various downstream attacks, making it a pervasive challenge for businesses to combat.
Website scraping: Malicious website scraping, also known as web harvesting, involves using bots to extract substantial amounts of data from websites and applications. This fuels various criminal activities, including creating fake accounts, account takeovers, generating fraudulent listings and reviews, hoarding inventory, and more. Additionally, scraped data may be sold to third parties or competitors, exacerbating the risks and implications of such attacks.
Inventory hoarding: Inventory hoarding involves accumulating excessive amounts of goods to create scarcity and control market supply. This manipulative practice aims to drive up prices and take advantage of limited availability, often resulting in inflated costs for consumers.
See how Snapchat reduces fake accounts:

RECOMMENDED RESOURCE
How Snapchat Replaced a Leading Bot Mitigation Solution to Dramatically Reduce Fake Accounts on the Web
How bots attack – and attempt to evade Arkose Labs
Not only are we seeing growth in the number of attacks, but we’re also seeing new attack vectors. Defending the most prominent brands online poses a significant challenge as attackers constantly seek ways to evade our defenses. For example, Arkose Labs safeguards 3 out of 10 leading social media platforms, and they are prime targets for creative attack techniques.
It’s common to see attackers try to avoid detection through different techniques like:
- Using a proxy server: A proxy server can be used to hide the user's IP address and make it appear as if the request is coming from a different location. This can make it difficult for bot management products to identify and block bots.
- Using a botnet: A botnet is a network of infected devices that can be controlled by a single attacker. Botnets can be used to launch large-scale attacks that can overwhelm bot management products.
- Using a custom bot: A custom bot can be designed to specifically target a particular bot management product. This can make it difficult for the bot management product to detect and block the bot.
And recently, we’ve seen a new technique that relies on a 2-step process.
- Step One: The cybercriminal generates a volumetric attack, which attempts to overwhelm a target with a massive volume of network traffic to generate significant load and noise on our detection infrastructure.
- Step Two: In the ensuing chaos, the attacker performs a more advanced attack, hoping it will go unnoticed amidst the large volume of traffic.
Here’s an example of this new type of attack, performed against an Arkose Labs customer. In this case, the attackers generated a 10-fold increase in transactions in an attempt to create enough noise so that they could slip in undetected.
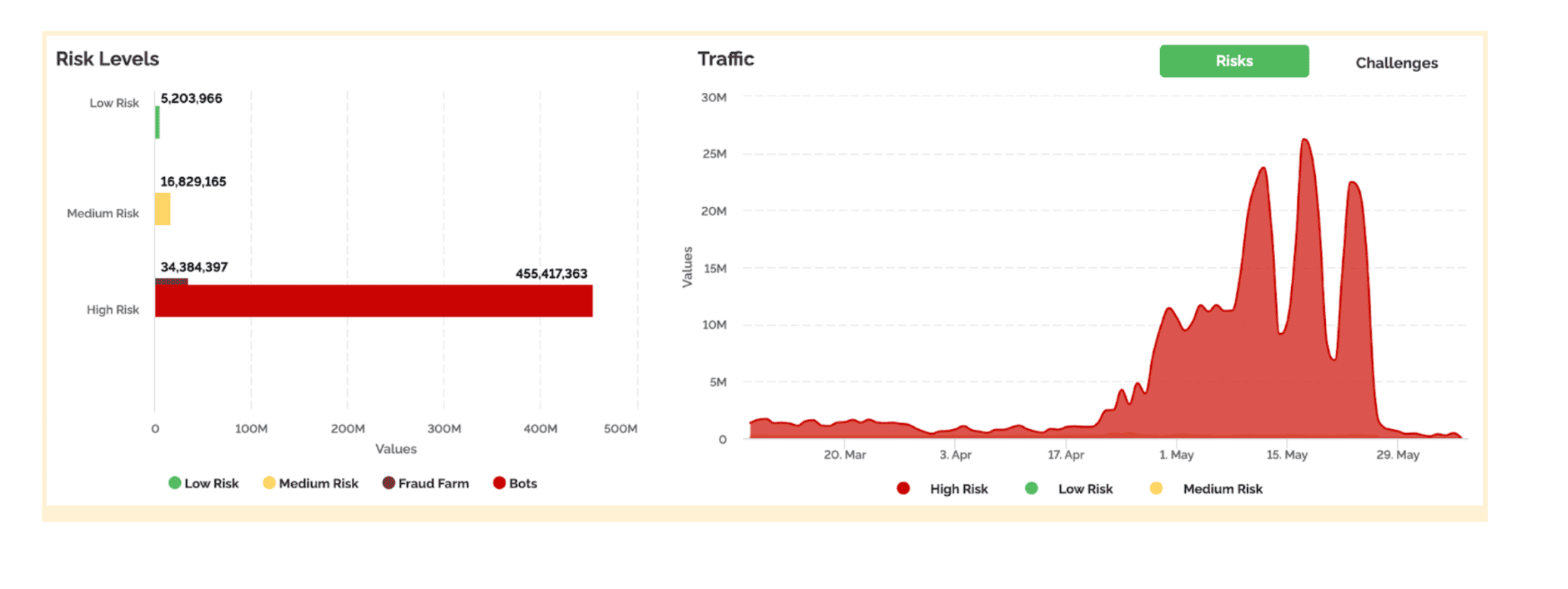
But the attempt was unsuccessful, thanks to how Arkose Labs addresses volumetric attacks. In the following diagram, you can see the 2 levels of mitigation. First, the volumetric attack is stopped immediately. Second, the targeted attack is caught at the next level.
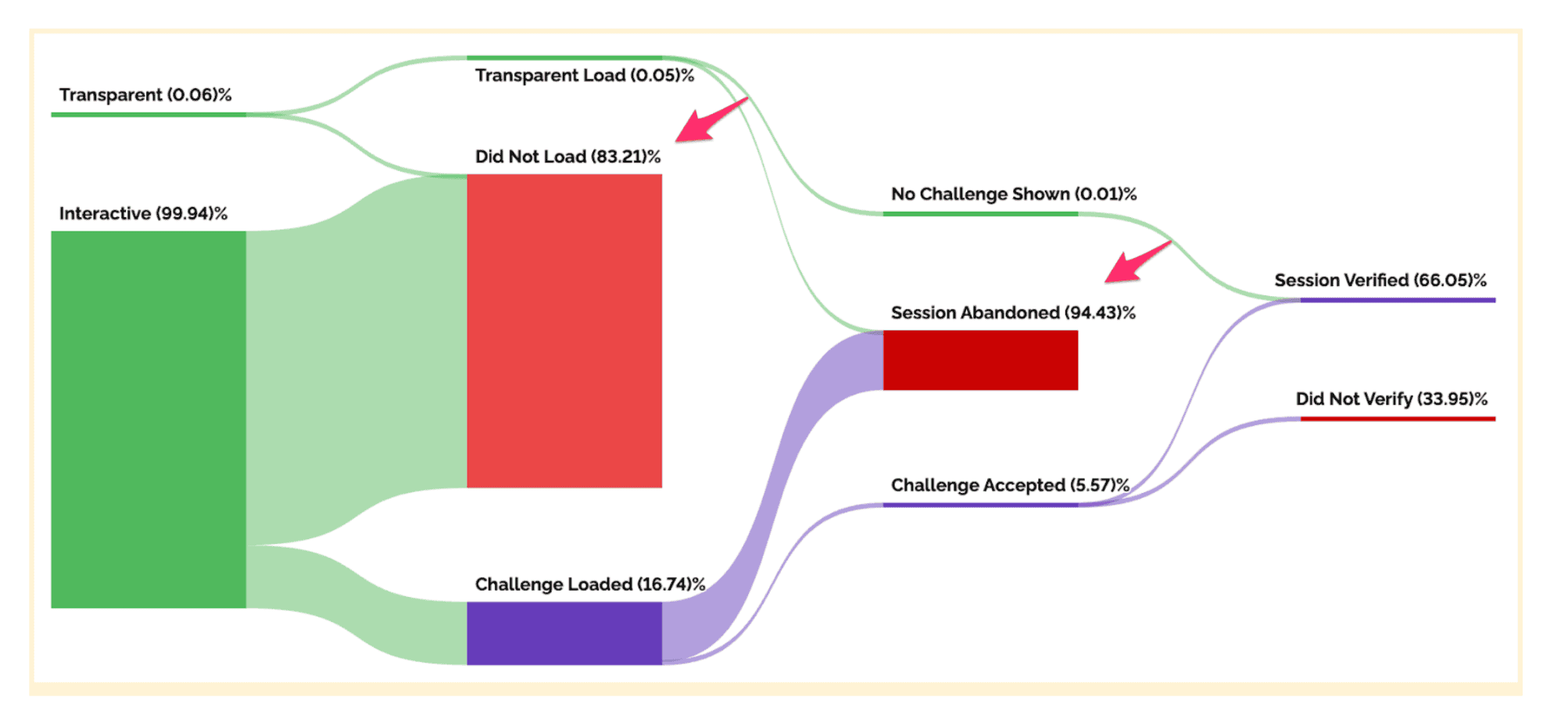
This emerging new attack vector and its implications for online platforms demonstrate the importance of continuous research and development of countermeasures to address evolving bot attacks.
Comprehensive bot monitoring and mitigation
Along with stopping this new attack method in its tracks, Arkose Labs uses a variety of techniques to detect and prevent cyberattacks. Among these are:
- Behavioral analysis: Arkose Labs analyzes user behavior to identify suspicious activity. For example, if a user tries to create an account with a new email address and then immediately tries to make a large purchase, this may be a sign of criminal activity.
- Challenge-response: Arkose MatchKey, the strongest CAPTCHA ever made, may challenge users with a variety of tasks, such as clicking on images, solving CAPTCHAs, or answering security questions. These challenges can help to distinguish between humans and bots.
- Machine learning: Arkose Labs uses machine learning to continuously improve its bot detection capabilities. As Arkose Labs sees more traffic, it learns to identify patterns that are associated with cyberattacks.
Mitigating the escalating threat with Arkose Labs
Arkose Bot Manager is an adaptive, comprehensive solution that helps businesses effectively detect, mitigate, and manage bot- and human-based attacks. It uses advanced techniques to distinguish between legitimate human users and malicious bots, allowing organizations to effectively block and prevent automated threats.
By combining machine learning, behavioral analytics, and risk assessment, Arkose Bot Manager provides real-time bot detection and mitigation, safeguarding businesses from the damaging impact of bot-driven attacks, account takeover, and other malicious activities. It does so in the following ways:
-
- Advanced Bot Mitigation: Arkose Bot Manager uses advanced techniques to detect and block malicious bots. By analyzing user behavior, device fingerprinting, and real-time data, it accurately distinguishes between human users and automated bots, effectively protecting businesses from cyberattacks.
- Adaptive Challenges: The platform utilizes adaptive enforcement challenges through Arkose MatchKey to authenticate users. These challenges present puzzles or tests that are challenging for bots but easy for genuine users, ensuring a frictionless user experience while thwarting automated bots.
- Real-Time Reporting and Analytics: Arkose Bot Manager offers real-time reporting and analytics, providing in-depth insights into bot activity, attack types, bot origins, and criminal behavior patterns. This information empowers businesses to enhance their defenses through data-driven decision making.
- Continuous Optimization and Support: Organizations receive continuous support from our expert team to analyze and optimize bot detection and mitigation strategies, ensuring businesses remain fortified against emerging threats and evolving attack techniques.
- Global Threat Intelligence: By maintaining a vast network of global threat intelligence, Arkose Labs keeps a constant watch on bot activity and cyberattack trends. This proactive approach enables businesses to stay ahead of emerging threats and evolving attack techniques.
With the accelerating menace of bot attacks, it's crucial for businesses to take proactive steps to protect their online assets. By staying vigilant and implementing robust security measures, companies can defend against these threats and ensure a safe digital environment for their operations and customers. Arkose Labs' expertise in combating cyberattack, coupled with our comprehensive monitoring of the evolving threat landscape, allows us to provide real-time insights and effective solutions.
Learn more about how Arkose Labs can protect your business from escalating bot attacks. Talk to an expert today!