This urgent need for proactive action was underscored in a recent webinar featuring industry experts Chief Insights Officer Julie Conroy from Datos Insights and Arkose Labs Head of Product Vikas Shetty. We had the honor of diving deep into this and other pressing issues, and their wealth of experience and sharp insights are incredibly valuable as we navigate the complexities of modern cybersecurity in banking. Here are the key takeaways.
From Lone Wolves to Organized Cybercrime
The session kicked off with a stark look at the shifting threat landscape. Vikas explained how cybercrime has evolved from isolated hackers to coordinated crime syndicates using advanced technologies. Banks and other financial institutions now face a significantly expanded threat surface, as attackers deploy sophisticated tools across various endpoints such as APIs. This shift has made traditional security measures less effective, requiring constant vigilance and adaptability.
A New Era of Threats
One of the most eye-opening trends is the rise of cybercrime-as-a-service (CaaS), a fully outsourced entity that generates revenue from bad actors who purchase a subscription for use of the service. Similar to a peer-to-peer (P2P) model, CaaS is an attacker-to-attacker (A2A) model where the CaaS entity provides a hosted software platform that can be used to actively engage in criminal attacks on their subscribers’ behalf, or provides an enabling service assisting subscribers with their own attacks.
Julie and Vikas illustrated how this model has significantly lowered the entry barriers for cybercriminals. Phishing kits are often purchased for just a few hundred dollars a month, and require little to no technical experience. This has resulted in a troubling increase in account takeover (ATO) attacks and a rise in sophisticated schemes like man-in-the-middle reverse proxy phishing, where phishing emails direct customers to reverse-proxy servers that capture real credentials and MFA codes. Similarly, ATO attacks now involve advanced automation and AI, making them more effective and harder to detect. Julie shared data showing that ATO continues to be a major concern globally, with attackers increasingly using AI to enhance phishing schemes and scale attacks.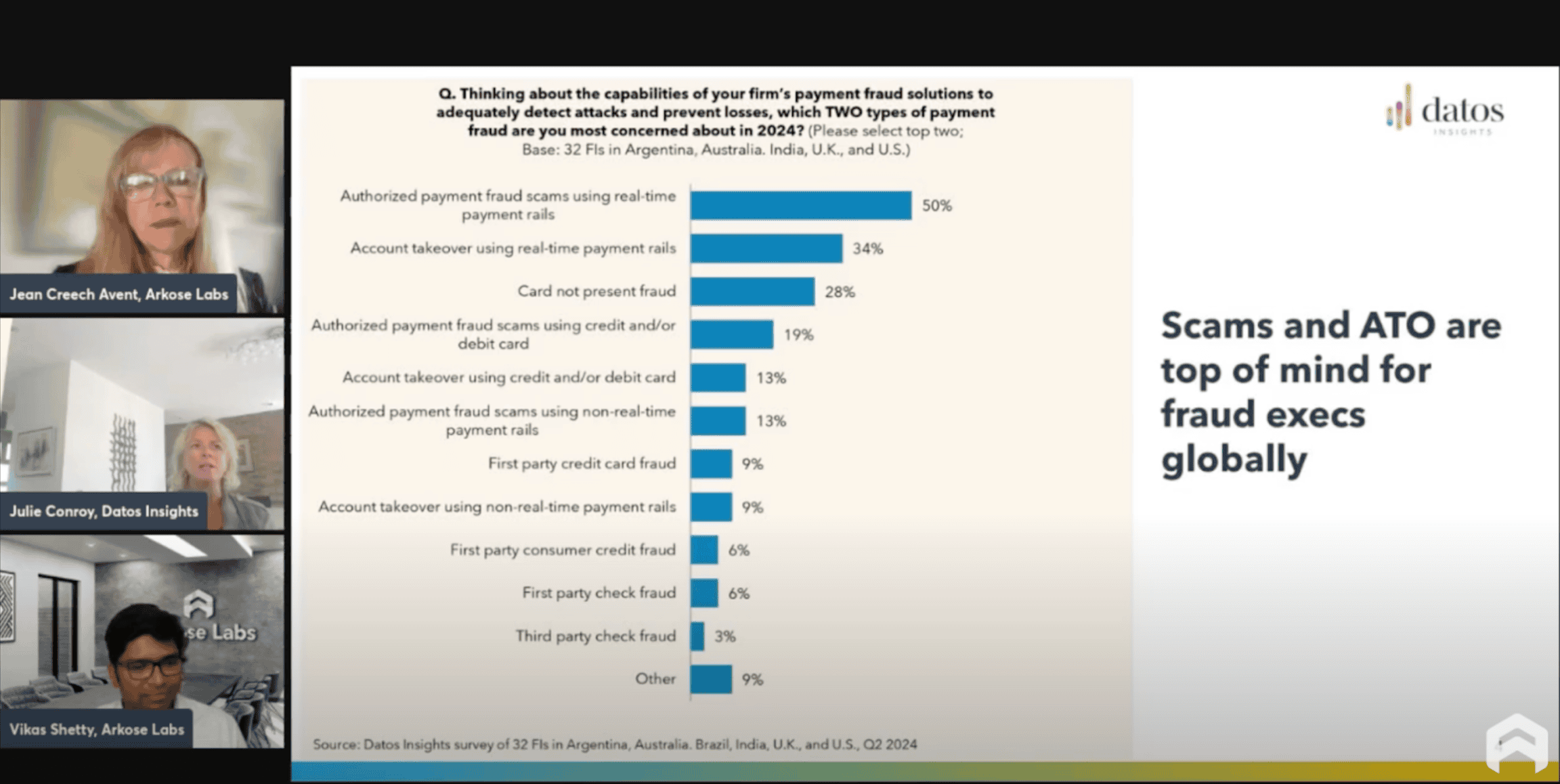
The Growing Concern of API Security
With the rise of open APIs driven by PSD2 in Europe and similar regulations in North America, API security has rapidly become a top concern for financial institutions. Securing APIs is akin to locking all the doors in a sprawling mansion, yet some doors remain hidden behind walls or beneath staircases. Without a full inventory, financial institutions can’t know which doors are secure and which ones are wide open, leaving room for intruders to slip through unnoticed.
Julie pointed out that securing these APIs is a complex challenge due to their diverse nature – whether mission-to-mission, process-to-process or those powering websites and mobile apps. Vikas emphasized that no single solution can effectively safeguard all types of APIs, which makes comprehensive protection a daunting task. Many institutions struggle with inventory management and discoverability of their APIs, often leaving potential vulnerabilities unchecked.
This lack of confidence, with 59% of financial institutions still in the dark about their API exposure, highlights a critical vulnerability. As attackers become more sophisticated, even a single overlooked endpoint can lead to catastrophic attacks. Julie reinforced the urgency of addressing this issue, as APIs have quickly become a prime target for cybercriminals. Without a comprehensive, focused approach to API security, financial institutions are leaving themselves open to exploitation.
Fraud in the Era of Real-Time Payments (RTP)
Julie also highlighted a significant trend: fraud attacks that are growing alongside the adoption of real-time payments (RTP) systems. Fraudsters are exploiting faster payment rails to quickly move stolen money through extensive networks of mule accounts, making it increasingly difficult to trace and recover funds. Julie emphasized that these criminals are capitalizing on the vulnerabilities of the end customer, and the speed of transactions exacerbates the challenge of tracing and reversing fraudulent activity.
AI: A Double-Edged Sword
The discussion then turned to the role of AI, and Julie noted that while adversaries are early adopters of AI, using it to develop and scale attacks with greater efficiency, banks are still lagging behind. This is due to the lengthy process large financial institutions face in adopting new technologies, driven by a need for transparency and traceability. For instance, the process of adopting AI in banking involves navigating business cases, legal reviews, IT queues and model risk governance, which slows down the integration of AI compared to its rapid adoption by attackers. On the defensive side, banks are deploying AI in back-office use cases, such as automating claim disputes and triage, but face challenges in applying AI to frontline fraud detection.
Meanwhile, malicious actors are using AI to create highly convincing phishing schemes and to scale their operations more effectively. The introduction of generative AI into the ecosystem has further amplified these threats, with attackers leveraging advanced AI tools to craft realistic emails and execute more sophisticated fraud tactics.
Vikas elaborated on the impact of AI, distinguishing between classical machine learning methods and generative AI. While classical AI methods are being used to tackle traditional ATO and fraud issues, generative AI introduces new challenges like impersonation attacks and deep fake frauds. Vikas noted that generative AI's probabilistic nature makes it less suited for detection scenarios but emphasized that it presents significant concerns due to its potential for creating realistic fake personas and deep fakes.
Navigating the Regulatory Maze
We also explored the complex regulatory landscape, which plays a crucial role in shaping how financial institutions approach cybersecurity. Julie outlined several key regulations, including FFIEC 2021 update, Dodd-Frank 1033, PCI DSS 4.0, DORA (Digital Operational Resilience Act), NIS II and PSD3, emphasizing that while these regulations provide a baseline for compliance, they should be viewed as minimum standards. Financial institutions should aim to exceed these standards to address the rapidly evolving threat environment effectively. Regulations can help justify investments and propel business cases, but they are not a substitute for a proactive and robust security posture.
Proactive Defense Strategies for Banks
As we explored solutions, Julie discussed the importance of a nimble control framework. Traditional fraud detection often resembles putting a bucket under a leaky roof after the rain has already started. Proactive defense strategies, on the other hand, are about fixing the roof before the storm hits, ensuring the damage is mitigated before it can even occur. The challenge lies in overcoming operational hurdles and leveraging AI effectively, as the attackers do. Julie stressed that banks adopting AI-driven solutions and faster response mechanisms can significantly improve defenses.
Vikas echoed this sentiment, stressing the need for proactive detection and mitigation strategies. He explained that traditional methods of waiting until after a transaction to analyze and respond are too slow. Modern approaches involve multi-layered security and progressive proofing, where evaluations occur at various points during a transaction, starting at the login or registration stage. This allows for earlier detection of potential threats and minimizes downstream impact.
Join Us for More Insights
The insights shared during our webinar are just the beginning of what’s needed to tackle today’s cybersecurity challenges in banking. To see the actual research Julie shared and to dive deeper into these crucial topics, I encourage you to download the on-demand webinar.

