Let’s dive into the dark mechanics behind MFA compromise, learn what it is and how it works, and uncover why it is the Achilles heel of modern security frameworks.
The Commercialization of Cybercrime
A specific type of phishing is the juggernaut causing the surge in MFA exploitation: reverse-proxy phishing, sometimes called man-in-the-middle (MITM) or adversary-in-the-middle (AITM) reverse proxy phishing. This type of attack is hard to detect and devastatingly effective, using reverse proxies that allow scammers to steal credentials and MFA tokens – leaving consumers dumbfounded and companies in the dark for weeks after a successful compromise.
What’s feeding this ecosystem? Number one, it’s the commercialization of cybercrime. This isn’t just a few isolated incidents – there’s a vast, multi-million dollar marketplace at play. Cybercrime-as-a-service (CaaS) and phishing-as-a-service (PhaaS) sites are rampant, offering tools and platforms specifically designed to bypass defenses like MFA. These services, accessible on the Dark Web or through channels like Telegram and Discord, sell phishing kits targeting your organization. And many of these sites are backstopped by some great guarantees of authenticity and effectiveness.
When I started my career many years ago, advanced persistent threat actors were typically nation states antagonistic to our interests or they were organized crime syndicates. Today, the threat is all about people who are using these CaaS and PhaaS platforms, and the platform has now become the advanced persistent threat. These platforms provide quality guarantees, data, knowledge, hosting, phishlets, bots for scale and, in some cases, even notification when an unsuspecting customer has clicked on a link or landed at a sponsored site. Why the latter? So that the audacious fraudster can start a real-time chat with the target! Basically, once the bad guys have the phishing kit, it’s pretty much done…all they need to do is set up the sites and create the phishing emails or ads. Throw in the “generative AI” accelerant, and they’re in business in a big way!
The Role of Generative AI
Generative AI has elevated the sophistication of phishing attacks. All of us have been the recipients of phishing emails where we knew immediately the email was a scam. But those days are long gone. Just last week, my bank sent me an email about a deposit in our corporate account. My first reaction was excitement – who put money in our account? I called my VP of finance to determine if the deposit was legit and he confirmed no such deposit was made. (BTW, remember to never click the link…authenticate these messages through normal channels!) Upon closer inspection, the email was nearly perfect. The logos, framework and language all seemed legitimate, but it was not from my bank. It was a perfectly well-crafted phishing attempt designed to harvest my credentials and MFA tokens.
How MFA Compromise Unfolds
Okay, so there are these “perfect” emails out there, but what does that have to do with MFA compromise? For years consumers have been falling for fake links and fake sites, but MFA was supposed to stop the scam in its tracks.
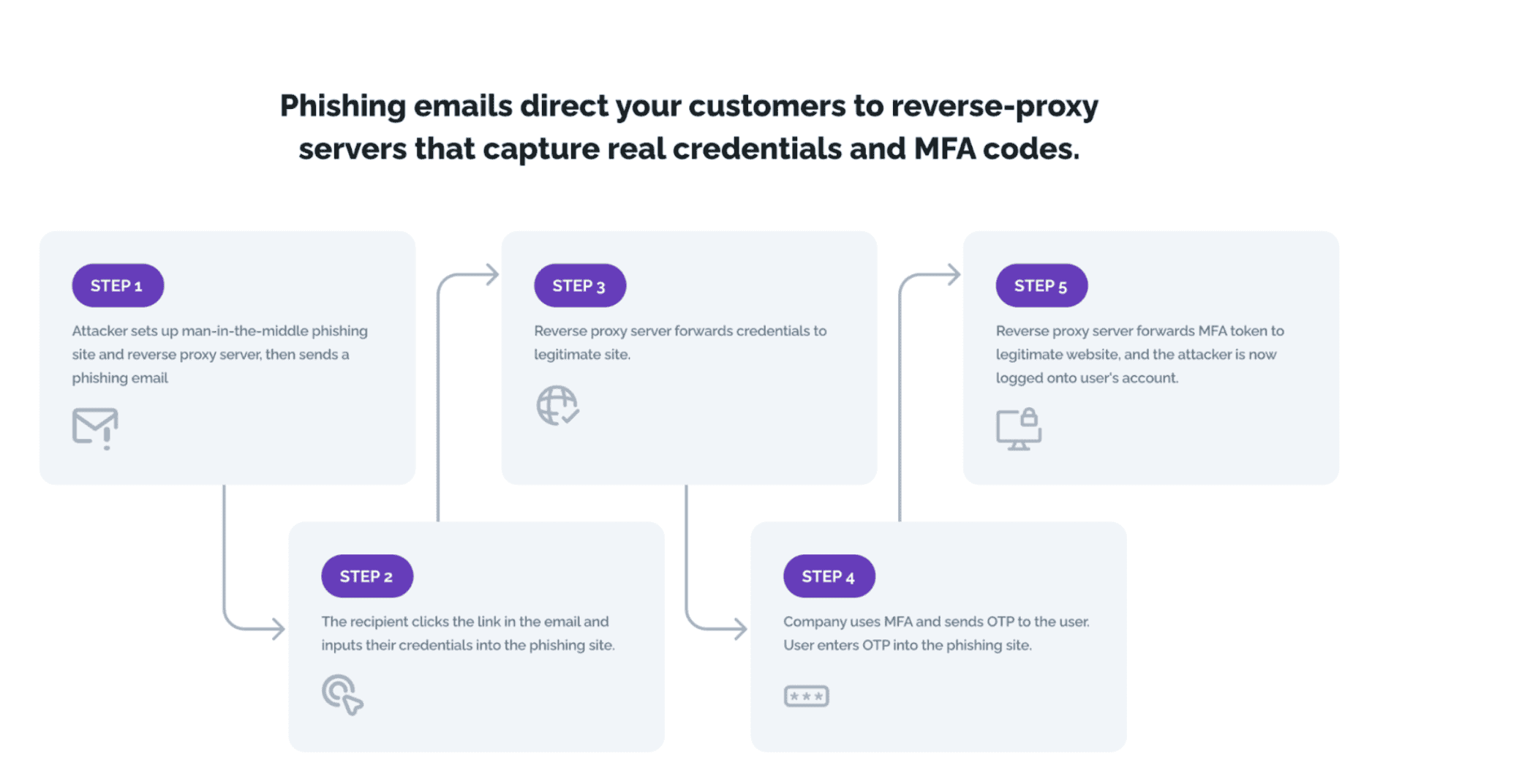
Here’s how MFA compromise is a false sense of security. The phishing kit can not only generate legit-looking emails and websites, but the attacker can also use it to set up a reverse-proxy server, which acts as an intermediary between the user and the real company website. The user thinks they’re interacting directly with the legitimate site, when in fact their requests are passing through to the attack server. And usually the attacker registers a domain name that looks similar to the real one, further obfuscating the attack.
So, the user clicks the link and arrives at a seemingly legitimate login page. The user then enters their credentials and the workflow kicks in. Behind the scenes, a bot is taking that information and is interacting with the enterprise. The business uses MFA to send the user a one-time passcode (OTP). Because the site is still being proxied, when the user enters the passcode, the attackers are able to suck the information on the MFA token out as well, taking control of the account.
The impact of this scam varies, depending on where the consumer and enterprise are located and the industry they’re in. Consider banking here in the U.S., where MFA compromise often focuses on draining accounts and harvesting data for resale. In Europe, the emphasis is on pushing payment authorizations, often involving small amounts to avoid detection and also harvesting data! So there’s a double whammy – the consumer’s account has been compromised and their data is now up for sale on the Dark Web.
And no industry is safe. What we see in our network is that attacks begin cross-industry, and they don't just begin at super-high value targets like banks. We're seeing that attacks start at gaming companies or at shared economy companies or at e-commerce companies…the attacks are perfected, and then once they're perfected, those attacks are vectored toward other sectors.
Why Spotting MFA Compromise Is So Difficult
These illegitimates sites mimic legitimate sites so perfectly that they can often pass through security scanners undetected. In one case, we took a site that we knew had been created via one of the phishing-as-a-service kits and ran it through a dozen of these security engines.
Every single service green-lit the site and passed it through undetected.
We knew the site wasn’t legit, but it was incredibly sophisticated. It even had a certificate that made it appear secure to the detection mechanism. To reiterate: these are very sophisticated adversaries that are using platforms and scale to attack our businesses.
How Arkose Labs Can Help
At Arkose Labs, our philosophy on helping businesses reduce the impact of attacks like MFA compromise is really pinned on three things:
- Make the cost of intrusion expensive from a computational perspective. By increasing the complexity and resource requirements of attacking our systems, we make it less attractive for attackers. The higher up the funnel you are, the more challenging it becomes, which reduces the profitability of their efforts.
- Leverage shared threat intelligence. We aggregate and analyze data across our customer base to enhance our threat detection and response capabilities. This collective intelligence allows us to better understand attack patterns and trends, making it harder for attackers to succeed and reducing their incentive to target our clients.
- Implement real-world consequences. We work with law enforcement and regulatory agencies to take legal action against malicious actors. By pursuing these bad actors directly, we help to disrupt their operations and deter future attacks. We've had great success doing that.
We apply this approach in understanding and addressing the dark mechanics behind MFA compromise so we can better protect our organizations from this escalating threat. Want to know more about how Arkose Labs helps enterprises like yours fight off this pernicious cyberattack? Check out our MFA compromise solution brief.