What is account takeover (ATO) fraud?
Account takeovers are where attackers use stolen credentials to break-in to a genuine user account and take control. Modern fraudsters use innovative techniques to break-in to user accounts, which makes it challenging to detect and block account takeover attempts. Manipulated digital identities, automated bots and scripts, and advanced evasion techniques make it difficult to spot account takeover attacks early in their tracks.
A successful account takeover attack allows cybercriminals to remotely control a genuine user account. This enables them to siphon off funds, redeem reward points, and even access the saved passwords and payment details. However, the motivation for account takeover goes beyond financial gain. Attackers use compromised accounts for a number of crimes that can have far-reaching social consequences.
One in five logins is an account takeover attempt
It is estimated that account takeover attacks rose 72% last year; and, there seems to be no let up visible in the near future. Arkose Labs Q3 Fraud and Abuse Report reveals that one in every five login attempts is fraudulent. Account takeovers are on the rise because, unlike a CNP (card not present) fraud, account takeover fraud allows attackers ample time to abuse the compromised account without getting detected.
The spate in account takeover attacks can be attributed to frequent incidents of data breaches, which provide bad actors with massive tranches of fresh consumer credentials. They use all of this data to corrupt digital identities at scale. Attackers impersonate genuine users and mimic their online behavior to fool fraud prevention teams. They also tap into the parallel ecosystem of cybercrime to access the tools and techniques that can help them evade detection.
Why fighting account takeover fraud can be so difficult
The business of cyber crime finds support in a parallel ecosystem that funds and benefits from criminal activities. Malicious actors tap into this ecosystem for cheap automated scripts, bots, and sophisticated criminal toolkits that help them scale their account takeover attacks. They use these resources to tailor their attacks for maximum profits against the investments made. Ultimately, ATO fraud techniques are becoming more complex, sophisticated, and strategic.
"Account takeover fraud techniques are becoming more complex, sophisticated, and strategic."
As the number of ways consumers access the internet increases—now including web, mobile, gaming consoles, and APIs—it expands the attack surface fraudsters can exploit. Businesses are deploying a variety of attack-prevention solutions to fight attack takeover attacks. However, the limitations of legacy approaches prevent businesses from adequately protecting themselves and their customers.
Cybercriminals have studied the defense mechanisms that businesses deploy. They use this knowledge to mobilize resources—bots, human sweatshops, or a combination of both—so they can launch more complex and nuanced account takeover attacks.
Some of the common ways attackers employ to orchestrate account takeover attacks at scale include:
- Bots: Bot-driven attacks allow digital criminals to maximize returns on investment by launching large-scale account takeover attacks.
- Credential stuffing: Bots are used to try multiple combinations of usernames and passwords to find the correct matches. This provides bad actors with the tools to launch large-scale automated account takeover attacks.
- Sweatshops: Low-cost human laborers are hired to mimic good customers in order to circumvent attack-prevention mechanisms designed to eliminate automated attacks.
- Account enumeration and account validation: Exploit the authentication processes with a view to check if the account identifier is valid or not.
- Social engineering: The most common form of social engineering is phishing, where malicious actors harvest verified customer information by manipulating individuals into sharing personal details or redirecting them to fake websites.
Why account takeovers are challenging to detect
Automated bots and scripts allow attackers to scale credential stuffing attempts, whereas human sweatshops allow bypassing bot-mitigation solutions. Criminals use human sweatshops, especially where ATO-prevention mechanisms require more nuanced human interaction. They pay these low-cost human laborers according to the defined number of login attempts in a stipulated duration. Even though all the attempts don't succeed, those that do allow attackers to achieve scale, which justifies the investment in the attack.
An account takeover is particularly challenging to detect. This is primarily due to two reasons:
- Today consumer access to digital services is platform-agnostic, from desktops and mobile phones to gaming consoles and software APIs.
- Attackers lie dormant to play a longer game. Unlike CNP fraud, where it is possible to block the card as soon as fraud is spotted, account takeover has a longer lifespan. This allows cybercriminals to hide their true intent and orchestrate multi-level attacks.
Legacy approaches don't match up to complex account takeover attacks
The limitations of legacy approaches make the fight against preventing ATO fraud even more difficult. This is primarily because businesses continue to use outdated solutions that are no match to today's complex and strategic account takeover attacks. These solutions fail businesses by allowing attackers to pass through with the least resistance while simultaneously creating a poor valid user experience.
The limitations of legacy approaches hinder the fight against preventing ATO attacks in the following ways:
- Automated solutions: Many organizations are still using automated tools to detect large-scale identity testing and credential stuffing attacks. However, bot technology has evolved to such an extent that bots can accurately mimic human behavior and bypass these antiquated defenses. Further, bots are now coded in such a way that they can hand over the attack baton to a human sweatshop if faced with a defense mechanism that requires more nuanced human interaction.
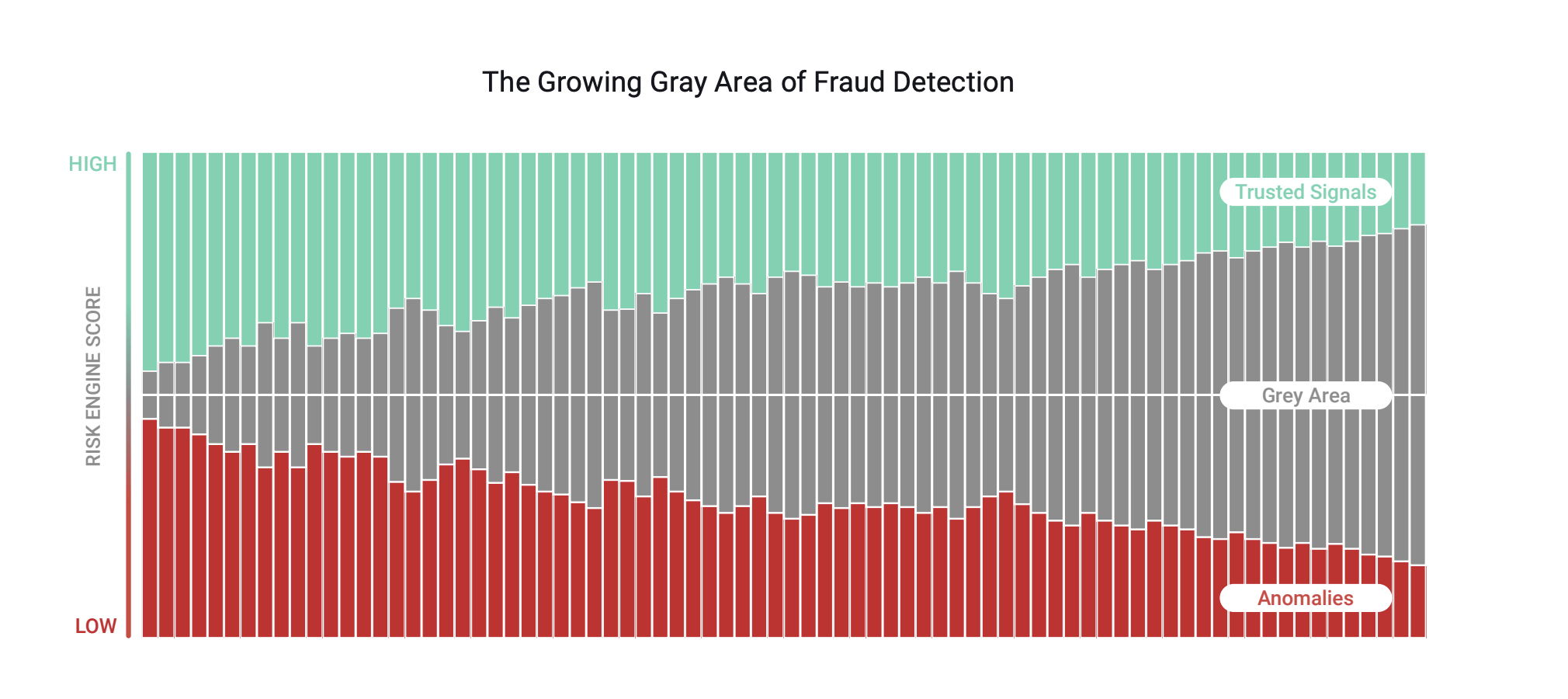
- Risk scores: In an effort to minimize inconvenience for their customers, businesses use risk-based attack-prevention solutions. These solutions analyze digital intelligence—device, identity, and behavioral analysis—to assign risk scores and create rules. However, risk- and rule-based fraud solutions depend on clear 'trust' or 'mistrust' signals from the users. When the signal falls in the gray area, the solution fails to distinguish between a good and malicious user. Incidentally, signals are increasingly in the gray area as fraudsters have corrupted digital identities at scale and good users display unpredictable behavior. This obliterates the attack-prevention efforts despite businesses investing time, effort, and money. When businesses use multiple solutions to address the limitations of risk-based attack prevention, they end up having complex tech stacks, alert overload, and intelligence that is difficult to action.
- Out of band authentication: Authentication mechanisms such as multi-factor authentication (MFA) that aim to increase the barriers for bad actors, actually introduce unnecessary friction for good users. Attackers have found ways to intercept OTPs delivered via SMS whereas paid authentication tokens can prove expensive.
- CAPTCHAs: Designed to protect and prevent against automated account takeover attacks, CAPTCHAs are available in many variants—from free to nearly-free. That said, CAPTCHAs today have become the most abused attack-defense mechanisms. There are numerous automatic solvers—available for free or nominal prices—that enable bots to easily bypass CAPTCHAs at scale. They have also failed to keep pace with the advancements in machine vision technology. This lack of innovation in legacy CAPTCHAs means a degradation in user experience, dropout of good customers, and loss of business.
Limitations of legacy approaches obstruct ATO fraud prevention
It is clear that limitations of legacy approaches prevent businesses from fighting ATO fraud in the manner needed today. Unnecessary and repeated authentication loops disrupt user experience, while reducing friction to maintain consumer convenience clears the pathway for attackers. This makes the fight against preventing account takeover attacks that much more difficult.
Businesses, therefore, need an innovative strategy that helps them expose fraudsters, who mimic true users, to prevent ATO attacks and protect good consumers.
How to prevent account takeover fraud with Arkose Labs
Going beyond behavioral analytics, device intelligence, or taking digital identities at face value, Arkose Labs leverages the combination of real-time risk assessment and enforcement challenges to foil account takeover attempts. The dynamic risk engine of the Arkose Bot Manager platform assigns real-time risk score to every user. Based on this risk score, Arkose MatchKey—the challenge-response mechanism—presents a context-based 3D challenge to every user.
Good users solve the challenges quickly, while bots and automated scripts fail, as the 3D challenges are resilient to automatic solvers and machine vision technology. When malicious humans try to clear the challenges at scale, they face 3D puzzles that progressively become more complex. This approach slows down the attack and increases the investments needed to clear the challenges at scale. The attack begins losing its financial viability, which makes it less attractive and forces attackers to move on.
The continuous feedback loop in Arkose Bot Manager ensures that the solution adapts to the changing threat landscape. This approach helps businesses overcome the limitations of legacy approaches and protect their customers from the menace of account takeover even in the long-run. To learn how global businesses have benefitted from Arkose Labs' expertise in protecting against account takeover attempts, read our solution brief or, to see it in action, book a demo today.
The Ultimate Guide to Account Takeover Fraud
- What is account takeover (ATO) fraud?
- One in five logins is an account takeover attempt
- Why fighting account takeover fraud can be so difficult
- Why account takeovers are challenging to detect
- Legacy approaches don't match up to complex account takeover attacks
- Limitations of legacy approaches obstruct ATO fraud prevention
- How to prevent account takeover fraud with Arkose Labs