Recently, I accessed my bank account after a long hiatus and was pleasantly surprised to note that the bank had added multiple layers of security to strengthen authentication. Financial institutions, especially banks, are a hot target for fraudsters for obvious reasons - they can strike it big with one successful attack. Given the gargantuan task of protecting the hard-earned money of their customers, it is only reasonable that financial institutions put in place all possible checks and measures to keep fraudsters at bay.
I noticed that the bank had introduced a one-time-password (OTP) based login for each attempt and was happy with the efforts made to protect consumer accounts from pilferage. Although, providing OTP at login adds friction to the access, it provides exponential peace of mind to the customers.
Phone-based OTPs come at a cost
Having said that, phone-based OTP comes at a cost to the bank, which is mostly transactional. Although, the bank would likely pay a fraction of a penny per transaction, cumulatively, it would add up to a significant amount. Let us take an example of a large bank that has, say, 420 million consumers, and almost 50% of them use online banking. Even if these online users logged in just once a month to, say, check the online balance, the bank would end up paying close to $2 million per month on just SMS OTP costs (and this does not even take into account the fact that many customers end up having multiple login attempts).
Now if the cost per SMS-based OTP were to increase 50x per transaction, instead of the earlier $2 million, the bank would end up paying $100 million per month. The bank wouldn’t like to bear all these costs and therefore, almost often these costs get passed on to consumers as fees.
This is exactly how International Revenue Share Fraud or IRSF can affect consumer-facing businesses.
What is IRS fraud?
According to Kaspersky, International Revenue Share Fraud, or IRSF, is “a type of telephone fraud that utilizes technical means to make unauthorized calls to premium numbers. Cybercriminals use hacked phones, stolen SIM cards, and compromised corporate PBXs to direct calls to their own or leased lines with billing of incoming connections.”
This sounds complicated and one may think that IRSF would apply only to telecom businesses. But practically, this fraud can hit any consumer-facing digital property that has some mechanism to trigger a voice-based (and more recently, an SMS-based) OTP.
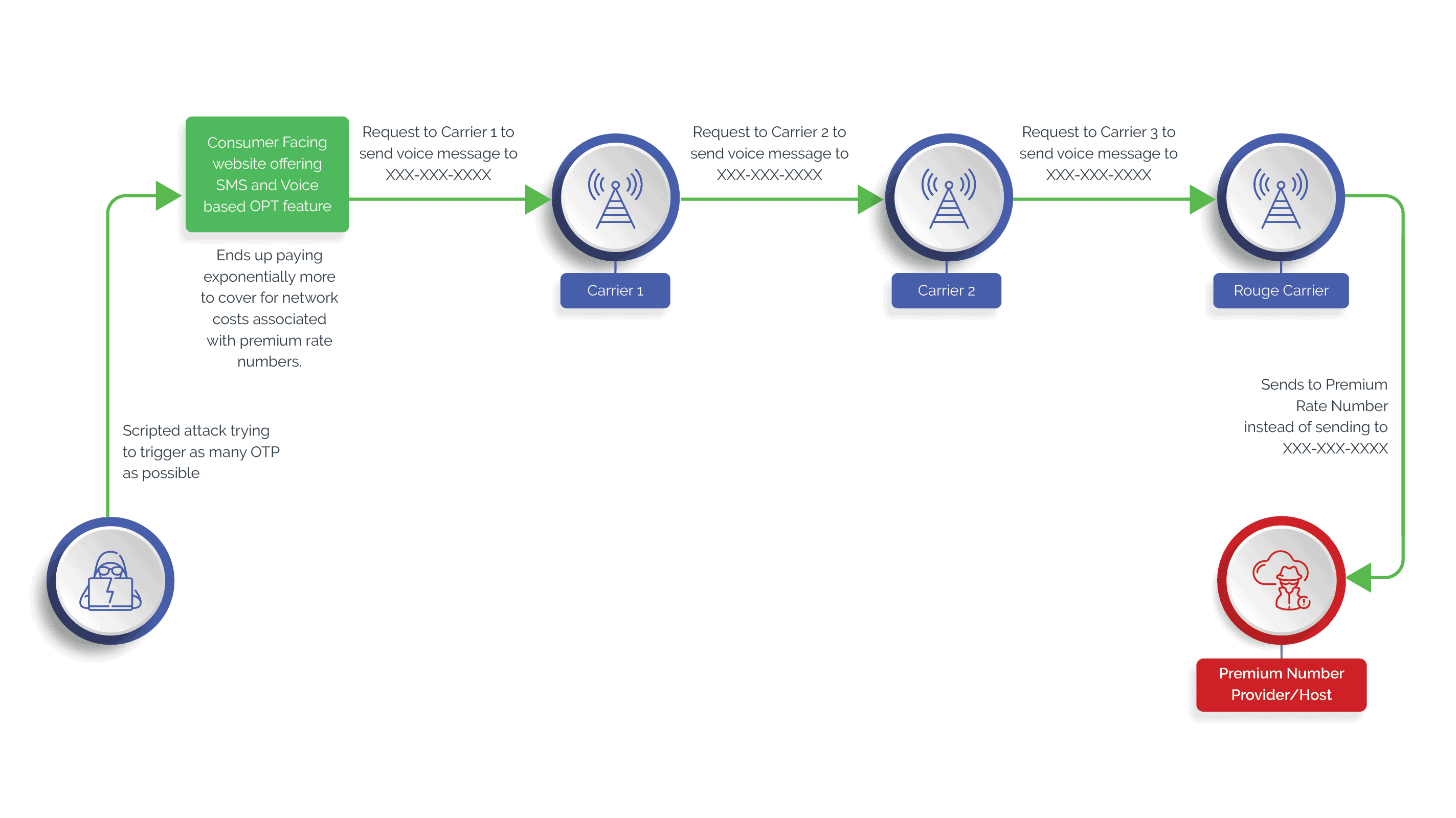
The IRS fraud involves a Premium Rate Number or PRN. Calls or messages to these PRNs usually cost much higher than regular numbers. You might remember TV game shows or live shopping shows, from almost a decade ago, where one needed to call a specified number to win a prize or purchase a ‘heavily discounted merchandise.’ Little did one realize then that these heavy discounts were balanced out by consumer’s heavy-spending on PRN calls.
In our current context, the modus operandi of the IRS fraud may look something like this:
- An attacker initiates a manual - or a scripted attack - on a webpage to trigger voice- or SMS-based OTPs. Given the high incentives, these can either be high-volume attacks or low and slow attacks.
- The consumer-facing business generally forwards the OTP request to a cloud communication provider.
- The provider would then send a request to a carrier. In any given region, there are generally multiple network providers involved before the OTP can reach the intended consumer.
- In this chain, sits a ‘rogue carrier’ that may have an agreement with the PRN provider/host to forward the request to the PRN number instead of the intended recipient, whenever the network provider gets a OTP delivery request.
- Since ‘terminating’ a call on a PRN is expensive, the costs keep adding up for the consumer-facing business to eventually fulfill.
- The fraudsters end up earning a good share ($1 or more) per transaction.
Detecting IRS fraud early is difficult
It is estimated that financial losses due to the IRSF can amount to anywhere between $4 billion and $6 billion per year. This is largely due to a lack of visibility into what is happening downstream, which also makes it challenging for businesses to stop IRS fraud early in its tracks.
These challenges to the businesses make the IRS fraud lucrative for attackers, who can adapt by initiating low-and-slow attacks (instead of volumetric attacks) to bypass most attack identification rules.
Know the three attack vectors of IRS fraud
Fortunately, all is not lost for businesses. They must know that there are three main attack vectors of IRS fraud, such that they can take appropriate steps to protect themselves. These include:
#1 An attack script.
#2 A range of unused PRNs.
#3 Partnership with rogue networks.
While #3 is largely out of control, #1 and #2 are elements that can be used for International Revenue Share Fraud prediction and mitigation. Here is what businesses can do:
- Prevent Scripted Attacks - Since there are high chances of an IRS fraud being a scripted attack, using a script breaker such as CAPTCHA providers can help stop the attack. Attackers would evolve the script but so would the providers in stopping the attack.
- PRN Intelligence - The ability to identify PRN is important. Several vendors provide and use information about unused PRN ranges to predict the possibility of an International Revenue Share Fraud attack.
Even if there is no ability to identify a PRN, one can see if OTPs are being triggered to number ranges. Often, attackers would purchase unused PRN ‘ranges’ to attack. Phone intelligence data is useful in this context. Phone intelligence providers often leverage cross-customer data to determine if the same number was used elsewhere to commit International Revenue Share Fraud.
- Billing Information - If the business has real-time billing contracts with cloud communication providers, putting billing alerts for high-priced transactions can help identify such fraud. That said, most billing ends up being monthly.
Preparation is key to fight the IRS fraud
The regionalization of network providers and an over-reliance on cheap mid- and low-tier middlemen can lead to opacity, which, in turn, can fuel attacks such as the IRSF. However, with the increasing sophistication of fraud detection tools and an abundance of network-level and signaling data, businesses can certainly prepare themselves to fight International Revenue Share Fraud.
To learn more about IRS fraud and how businesses can protect themselves, contact us now.