“This is the lesson: never give in, never give in, never, never, never, never—in nothing, great or small, large or petty—never give in except to convictions of honour and good sense. Never yield to force; never yield to the apparently overwhelming might of the enemy,” thundered Winston Churchill as he addressed his Alma Mater in 1941. These are powerful words that, even today, stir emotions, strengthen resolve, and brim with a call to continuous action.
Churchill’s words were uttered at a time when all seemed lost, and threats appeared insurmountable. Eighty-two years later, I am moved by the tenacity of that call to action, and often find myself thinking on his admonition as threats, challenges, and obstacles abound. “Never give in” is a mantra that all of us involved in the honorable pursuit of protecting businesses and consumers from omnipresent cyber threats need to take to heart.
Churchill also famously said, “It is no use saying, We are doing our best. You have got to succeed in doing what is necessary.” Two powerful directives applicable to our struggle against cyber threats: “Never give in” and “do what is necessary.” Both are imperatives in the ongoing battle against cyber threats and bad actors that require us to be prepared, predictive, intentional, and relentless in our risk mitigation efforts.
Find out more about today’s cyber threats in our new eBook: Bad Bots & Beyond: 2023 State of the Threat Report.
Preparedness: Do what is necessary.
This call to action presupposes a deep understanding of the risk environment. As CFOs, it falls to us to bridge the gap between cybersecurity preparedness and the financial implications for our organizations. By ensuring that security imperatives, technology investments, and personnel are properly funded and strategically prioritized, we are “doing what is necessary.”
Whether we own the reporting relationship with the CISO, as is the case in many public companies, or we own the responsibility for business risk mitigation, which is the case in every company, we own the imperative of preparedness. So, what does it mean to be prepared…to be constantly prepared? We must all grapple with this question, especially considering the dynamism of the current threat environment. Minimally, we must:
Understand our vulnerabilities. For example, can we distinguish between sophisticated bot activity vs. legitimate customers vs. bad actors in new account registration and login activities? If so, do we know:
- How much friction to introduce into the activities to ensure that the individuals transacting in those workflows are legit?
- What would happen if the bots or bad actors succeed in their efforts?
- Can we quantify the potential financial exposure and the downstream costs associated with the compromise?
- What data might be exposed?
Implement a culture of continuous cyber threat training. We must instill a degree of professional skepticism into the functions most likely to be affected by a compromise attempt.
- Do we run simulations that test the latest known threat vectors, including, Smishing, Phishing, Business Email Compromise, and others?
- How did our people respond?
- Are we still relying on grammatical errors or unfamiliar tone in an email as the gotchas for detecting a Phishing scam?
- What happens to that approach when AI can now compose grammatically and contextually tonal emails better able to trick the recipient?
Select proven partners. As CFOs, we cannot fall to the allure of cool technology delivered by thinly capitalized and unproven vendors to power our critical systems. Have we selected vendors that are enterprise class? Think bank class…
- Would they pass the rigor of a critical vendor in a highly regulated institution?
- Is their reputation and product efficacy well regarded and proven?
- Do they stand behind their products with warranties, SLAs, and cyber threat experts ready to assist at the moment of need?
Preside over a cyber threat committee. Bring together a group of internal constituents which meets frequently to assess risk, quantify exposure, determine insurance requirements, and report our cyber threat posture to the c-suite and the board. Minimally, the committee should include business line owners, the CISO and the infosec team, and legal.
Predictive: Don’t wait for the onslaught.
A quote often attributed to Churchill, “Let our advance worrying become advanced thinking and planning,” highlights the need to be predictive as it relates to our position as CFO in staying one step ahead of cyber threats. This thinking requires us to embrace the notion that it’s not if but when our organization will be attacked. Consequently, we must develop the predictive muscle, informed by our preparedness, that minimally:
Focuses us on following attack trends, hardening targets, and using data for protection.
- What have we seen in attacks that have affected our competitors?
- What was the financial impact of those attacks?
- What downstream implications resulted from the attacks?
- When did the CFO become aware of the threat vector and resulting compromise?
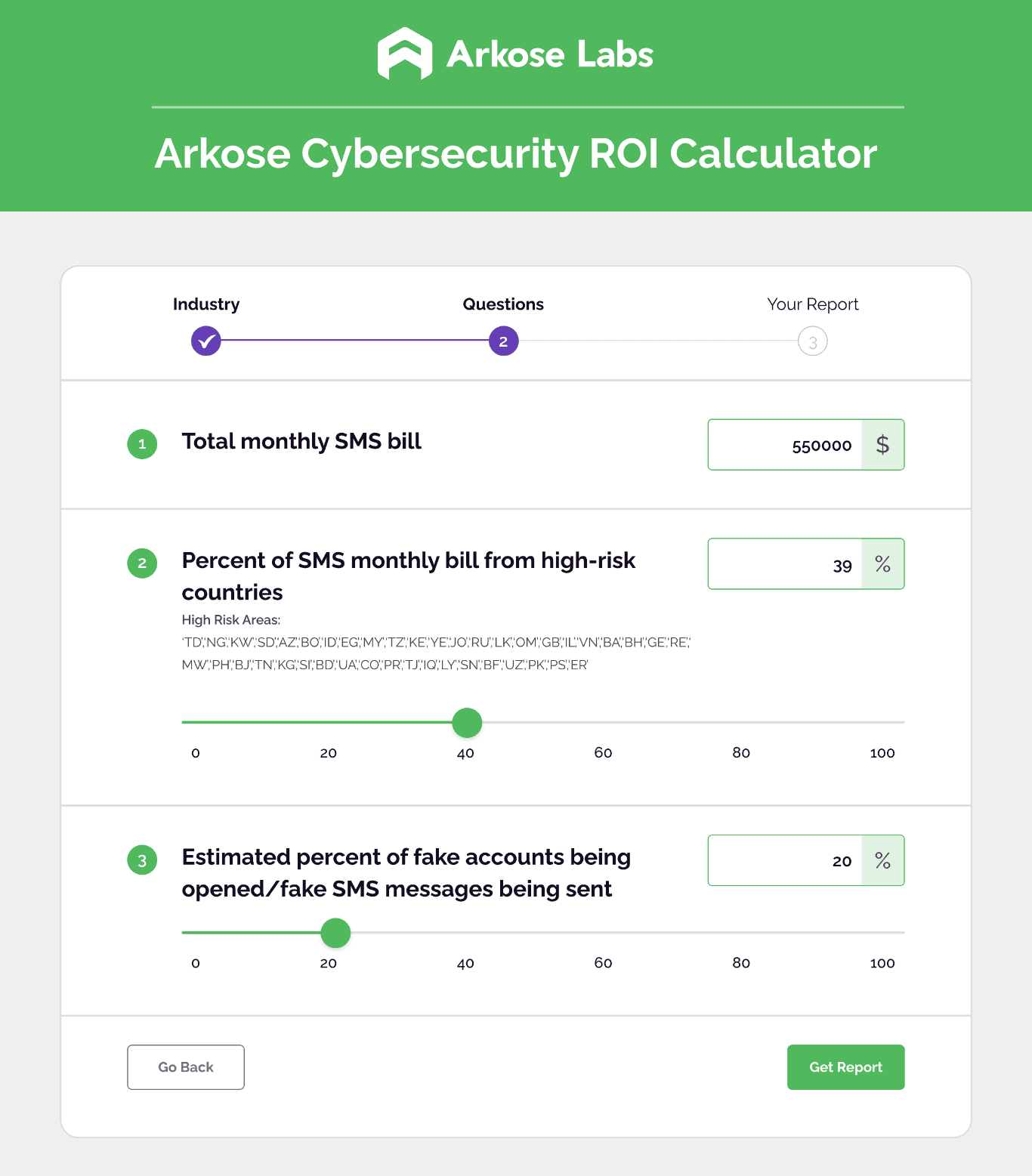
The last question is critical because many expensive cyberattacks go undetected by the finance organization for months. For example, consider SMS toll fraud, which is one of the most prevalent and current attack vectors. Bad actors and unscrupulous telcos and carriers collude to share the proceeds of illegitimate SMS activity during a registration process.
As CFO, we may interpret our increased SMS charges as proof of successful marketing initiatives to drive new registrations. It may take months before that premise is proven false—and by then, millions may have been lost. Why do I note millions? Because that is the magnitude of that attack vector on other organizations today. So, now that I am aware of the trend, I need to create a feedback loop that scrutinizes SMS spend against new registrations and deploy technical solutions that are proven to stop the attack.
Estimate the potential cost savings associated with stopping SMS toll fraud. Use our calculator today!
Interdict: Relentlessly fight and never give in.
The bad actors are intentional…they always come back with new attack vectors. It is not a one and done exercise. The key here is to be equally intentional and engaged in interdiction and mitigation. As CFOs, we must be vigilant and aggressive in our counterpunching. As the person stewarding my organization through business risk, it is imperative that I minimally:
Make the compromise effort expensive for the adversary. Consider the cybercrime-as-a-service environment in which we operate today. All of the tools needed for DIY fraud are readily and easily available to potential adversaries. For example, bad bots can be rented at scale, social channels like Discord, Telegram, and others are replete with DIY fraud information, and compromised data derived from innumerable data breaches is everywhere. In this environment, our job is to make compromise hard and expensive.
How? Use technologies and vendors that can increase the processing cost associated with automated attacks and then deploy those technologies in all workflows where financial opportunities abound.
The reality of cyber threats is a “follow the money” model. If the attack is increasingly expensive to perpetuate, and the value of the target is diminished and hardened, the incentive to compromise, the ROI if you will, becomes less attractive.
Determine the cost of compromise and engage vendors that help lessen that cost. The internal ROI must also be quantified to ensure alignment and continued engagement in the fight. Again, not a one and done exercise. Quantify the potential fraud losses, credit repair losses (call centers and notification services), and brand impact of a compromise in determining the budget allocation to fully fund these efforts. Remember, this is a table stakes, high-priority investment exercise that must be considered annually irrespective of the ebb and flow of cyberattacks.
Learn: Federate the data within our organization and our partners.
In February of 1941, in an appeal on the BBC to President Roosevelt, Churchill stated, “We shall not fail or falter; we shall not weaken or tire. Neither the sudden shock of battle, nor the long-drawn trials of vigilance and exertion will wear us down. Give us the tools, and we will finish the job.” Powerful and salient guidance in our mission against cyber threat.
As CFO, each of us must not just quantify the financial, regulatory, legal, and brand risks associated with cyber threats. We must steward our organizations through the maze of business risk, and we must stay vigilant and prepare, predict, and interdict by funding our teams with the right tools to finish the job! Our mission to protect our organization from this persistent and dynamic business antagonist is honorable, sensible, and never more important. Stay the course and never, never give in!
Have more questions on the strategies a CFO should employ?
Please reach out! The Arkose team and I stand ready to help.