A credential stuffing attack refers to automated or human-driven activity whereby fraudsters try to match stolen username-password combinations to find valid matches at scale. Once valid credentials are obtained, fraudsters can make money by either selling them to third parties or on the dark web or using these databases themselves to orchestrate account takeover attacks.
Credential stuffing is the fuel that powers account takeover attacks. Easy access to personally identifiable information of consumers - thanks to years of data breaches - and commoditized tools that allow scaling up an attack with least possible investments have contributed to the phenomenal rise of credential stuffing attacks in recent times. According to Arkose Lab’s 2021 Fraud and Abuse Report, there were 285 million credential stuffing attacks detected and stopped on the Arkose Labs network in the first six months of the year with spikes of upwards of 80 million in a single week.
That said, credential stuffing should not be confused with brute-forcing. In credential stuffing fraudsters use real consumer data that was exposed in incidents of data breaches; whereas in brute forcing fraudsters try to guess passwords using random characters or password suggestions. Since real data stands for greater credibility, the probability of arriving at valid username-password combinations is greater through credential stuffing, which also explains the recent rise in this activity.
How Do Fraudsters Launch Credential Stuffing Attacks?
The ease with which credential stuffing attacks can be launched has made them the bedrock for multiple types of fraud attacks. Fraudsters are in the business of fraud to make money, they try to maximize profits with the least possible investments and the ability to scale up the attacks quickly. They use automation to achieve scale, as well as human sweatshops to be able to evade defenses that are designed specifically to fight automation.
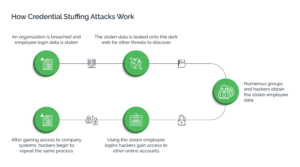
Essentially, there are three main steps to a credential stuffing attack:
-
Data Harvesting:
Before fraudsters can launch a credential stuffing attack, they need the raw materials - databases containing valid emails, usernames and passwords. This data is easily and cheaply available off the internet or the dark web; or can even be stolen through the use of malware, phishing, or social engineering.
-
Validating Accounts:
Once fraudsters have the required data, they now set out to obtain valid username-password combinations. To do this rather quickly and at scale, fraudsters deploy bots, automated scripts, human click farms, or a combination thereof. They enter the list of stolen credentials into a tool, configure the proxies, define the target, and launch the attacks. For more nuanced attacks, fraudsters use human sweatshops or may even do it themselves for high-value accounts.
-
Monetize Attack:
There are several ways fraudsters can monetize credential stuffing attacks - the simplest being selling off the validated credentials to third parties or on the dark web. They can also take over user accounts through these credentials to siphon off the money from the compromised account or use the information from the account itself to carry out further attacks such as money muling, micro deposit fraud, money laundering, and so forth.
Current Solutions Fail to Stop Credential Stuffing Attacks
In recent times, there has been a prolific rise in credential stuffing attacks; especially in the financial sector. Credential stuffing attacks constituted 41% of all attacks on the financial services sector between 2017 and 2020. This can be largely attributed to the easy availability of consumer data and cheap (or nearly free) easy-to-use bots. Further, consumers reusing the same passwords across their digital accounts is making it easier for fraudsters to hack into multiple accounts with the same valid credentials.
It is clear that the menace of credential stuffing is on the rise and there is an urgent need to arrest its further ascent. However, current fraud defense approaches are limited in their scope and therefore prove inadequate in stopping credential stuffing attacks. Identity-based solutions have been circumvented with tactics such as IP spoofing, device obfuscation, and so on, enabling fraudsters to use stolen credentials to disguise themselves as good users.
Data-driven risk assessment looks for clear ‘trust’ or ‘mistrust’ signals, which have been rendered ineffective as digital identities have been corrupted at scale and consumer behaviors, too, have evolved. Therefore, a greater portion of signals are now in the ‘gray’ area, making it difficult to ascertain the true intent of an incoming user.
Furthermore, fraudsters have the knowledge about the fraud defense mechanisms that businesses are deploying and adopting new techniques to evade them. As a result, the cat-and-mouse game continues between the businesses and the fraudsters.
An Effective, Long-Term Approach to Fight Credential Stuffing Attacks
Businesses cannot afford to keep absorbing fraud losses as the cost of doing business. They need an effective approach that can help them disrupt fraud and put an end to these large-scale attacks in the long-term.
Global brands trust Arkose Labs’ zero tolerance to fraud approach where risk-based decisioning is supplemented with intelligent step-up enforcement challenges to clearly identify bad actors from genuine users. In this approach, no user is blocked. Instead, all users can prove their authenticity and continue with their digital journeys.
Bots and automated scripts cannot pass this test as they cannot clear the 3D puzzles rendered in real-time. High-risk, human users are continually presented with more puzzles that keep increasing in complexity to wear them down and exhaust their resources. The need to put in additional effort, time, and resources to clear the challenges at scale means depletion of profits from the attack. This targeted friction makes the attack lose its attraction and forces fraudsters to move on.
Since Arkose Labs’ risk assessment and enforcement challenge mechanisms are connected through a continuous feedback loop, it helps improve fraud detection rates, while decreasing challenge rates for good users. Embedded machine learning provides advanced anomaly detection and evolving protection, which eases the burden on in-house teams.
Arkose Labs’ $1m Credential Stuffing Warranty
At Arkose Labs, we believe that businesses deserve more protection from their security vendors, delivered through true partnerships which are committed to customer success. As such, we are providing a credential stuffing warranty that makes us the first security vendor that covers key incident response costs of up to $1 million. This warranty also offers a 48-hour SLA for rapid remediation to minimize the impact of credential stuffing attacks.
To learn more about Arkose Labs’ multi-step approach to comprehensive and long-term protection from credential stuffing attacks while maintaining superior user experience, click here.