What is social media account takeover?
Unauthorized access to users’ social media accounts, such as on platforms like LinkedIn, Instagram, Twitter, Facebook, Snapchat and others, using devious methods like phishing, using consumers’ stolen personal information, exploiting weak or stolen passwords, or exploiting security vulnerabilities is called social media account takeover.
The compromised accounts then serve as a launchpad for multiple types of malicious activities, such as illegal fund transfer requests, spreading misinformation, scamming social media followers, or tarnishing the account owner's reputation.
RECOMMENDED RESOURCE
Snapchat Identifies Critical Risk & Shows Direct Savings with AWS & Arkose Labs
How social media account takeover (ATO) works
- Credential Acquisition: The attacker obtains the user's login credentials through methods like phishing, hacking, or buying from the dark web. Learn more about credential harvesting and how to prevent it.
- Account Access Attempt: The attacker tries to log in to the target account using the harvested credentials.
- Exploitation of Vulnerabilities: The attacker may exploit security flaws in the social media platform to gain unauthorized access.
- Account Control: Upon access, the attacker changes passwords or security settings to lock out the legitimate owner.
- Account Exploitation: The compromised account is used for phishing, spreading spam, misinformation, or deceiving followers.
What Role Do Bots Play in Social Media Account Takeovers?
In recent times, bots have come to play a crucial role in social media account takeovers. Attackers can program bots to perform specific tasks such as looking out for vulnerable social media accounts or weak security settings. Bots can then systematically use techniques like brute force attacks or credential stuffing with valid username-password combinations to compromise vulnerable accounts.
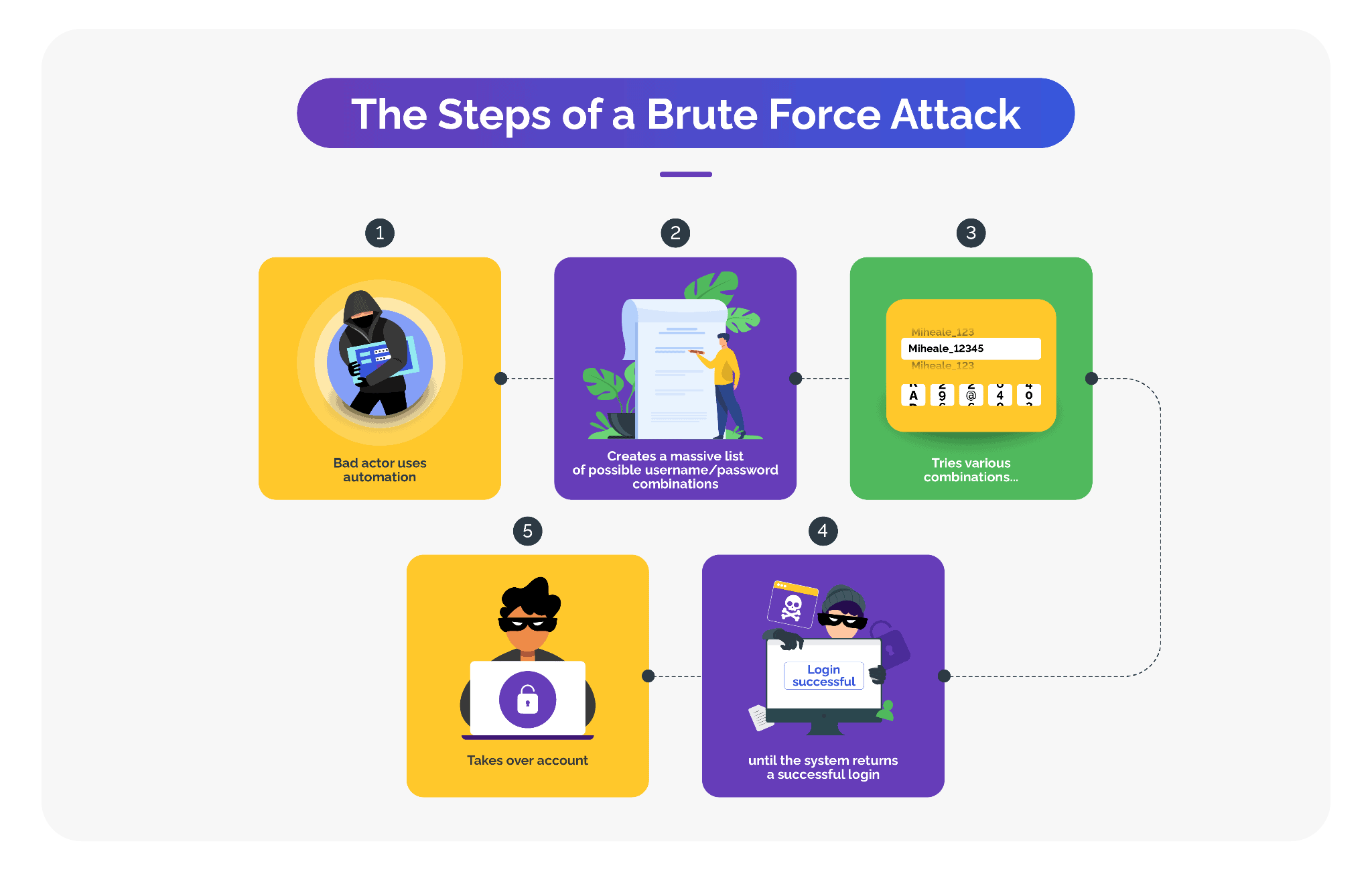
Because bots can automate the attacks, they can spread phishing links or malicious content quickly across social media platforms, amplifying the reach of the attack. Furthermore, bots can mimic legitimate user behavior not only to artificially inflate the number of followers or engage in activities like liking, following or sharing content, but also to fool social media managers and evade detection.
By facilitating large-scale attacks in no time and with the least possible investment, bots aid attackers attempting social media account takeovers while diluting fraud prevention efforts.
What Are the Consequences of Successful Social Media Account Takeovers?
- Reputational Damage: Unauthorized posts or activities can harm the account owner's reputation, leading to a loss of trust among social media followers and potential damage to professional relationships or job prospects.
- Exposure of Sensitive Information: Attackers can access private messages or personal data, which may be sold to third parties or on the dark web, exposing the compromised user to further threats.
What Techniques Are Used in Social Media Account Takeover?
Attackers use several techniques for social media ATO. These may include luring users into revealing their login credentials, hacking or exploiting security vulnerabilities in social media platforms.
Common methods employed by fraudsters
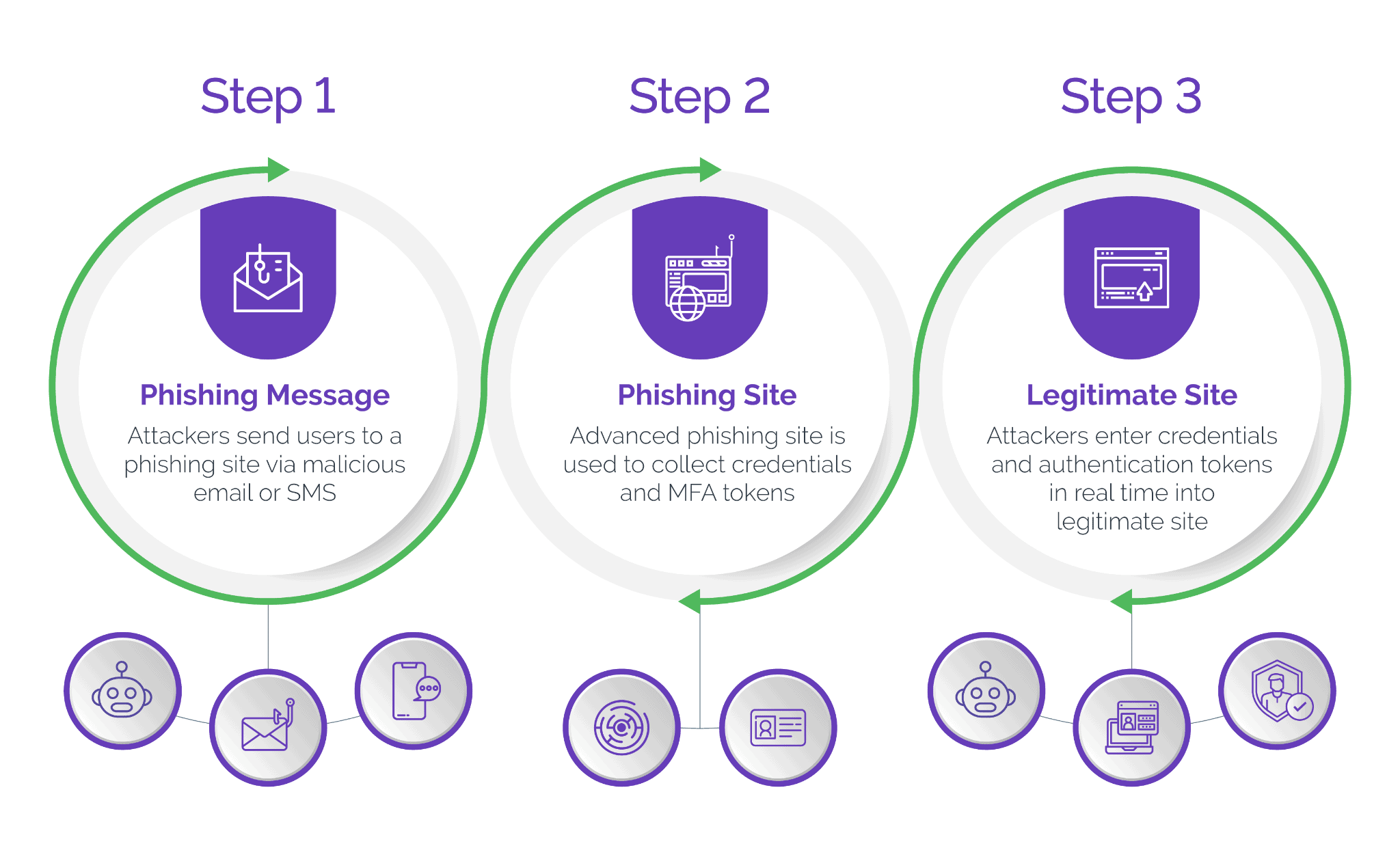
- Phishing: Fraudsters send deceptive emails or messages to trick users into visiting fake websites and sharing personal, financial, or account information.
- Social Engineering: Attackers impersonate trusted entities to manipulate users into divulging sensitive information or resetting passwords.
- Weak Password Exploitation: Fraudsters take advantage of weak or reused passwords by using automated tools to test stolen credentials from data breaches against social media accounts, gaining unauthorized access where passwords are not updated.
What Are the Emerging Trends in Social Media Account Takeover Techniques?
- AI-Powered Bots: Attackers use AI-powered bots to generate convincing messages and execute sophisticated phishing attacks with higher success rates.
- Social Engineering: Heavily relying on topical issues, societal trends, or psychological triggers to manipulate users into sharing credentials or performing risky actions.
- Exploiting New Features: Attackers adapt strategies to exploit new features and functionalities on social media platforms, such as rogue app permissions in third-party integrations.
- Targeting Influencers: Influencers are increasingly targeted to exploit their wider audience for financial gain or misinformation.
How To Recognize Social Media Account Takeover Red Flags?
Recognizing red flags indicative of account takeover (ATO) attempts can go a long way in enabling social media platforms to prevent unauthorized access, mitigate damage, and maintain user trust.
Warning signs for social media platforms
- Spike in Failed Login Attempts: An unusual increase in failed login attempts.
- Reports of Compromised Accounts: Sudden rise in reports of compromised accounts.
- Spammy Content: Emergence of spammy content or messages from multiple accounts.
- Login from Multiple Locations: Suspicious user behavior, such as login attempts from multiple locations within a short time frame.
- Unexpected Engagement Metrics: Unanticipated changes in user engagement metrics.
- Decline in User Activity: A sudden drop in user activity.
- Increase in Account Deletions: Unexplained rise in account deletions.
Warning signs for consumers
- Unexpected Password Reset Emails: Receiving unexpected password reset emails or notifications of login attempts from unfamiliar locations.
- Unexplained Changes to Account Settings: Changes to profile pictures, usernames, linked email addresses, or account settings that the user did not make.
- Unauthorized Posts or Messages: Posts or messages that the user did not create.
- Phishing Attempts: Receiving communication from the social media platform about suspicious activity, often urging the user to take immediate action, like responding to limited-time offers or special events.
How to prevent social media account takeover
Implementing strong authentication measures and training users on good digital habits can help social media platforms prevent attacks.
Enhancing security measures
Social media platforms can focus on improving the cybersecurity measures by investing in advanced authentication methods, such as biometrics. This will add an extra layer of protection beyond traditional passwords. Robust monitoring systems can help social media platforms proactively detect and respond to suspicious activities, thereby mitigating the risk of unauthorized access and potential damage.
Ensuring continuous monitoring
Social media platforms must prioritize continuous monitoring to spot anomalous user behavior and take appropriate countermeasures before an incident can take place. By regularly reviewing account activity logs, platforms can help identify abnormal login activity, unfamiliar locations or sudden changes in behavior. Social media platforms should consider using smart bot management solutions to detect non-human traffic, to prevent automated account takeover attempts. Furthermore, social media platforms must incorporate technology-driven security solutions that can trigger real-time alerts and notifications to improve proactive monitoring efforts and respond promptly to emerging security threats.
Conducting awareness campaigns and educating users about the importance of using strong, unique passwords, enabling multi-factor authentication whenever possible, and being cautious of suspicious links, emails or text messages can enable them to detect and stop account takeover attempts.
Want to know more about how to stop account takeover and other cyber attacks on your social media platform? Visit our social media and streaming solution brief.
